A group of researchers has found a new malware variant designed to breach the security of Windows containers in order to reach Kubernetes clusters. Identified as Siloscape, experts describe this malware variant as something unusual due to its complex features.
The report, prepared by Palo Alto Networks, notes that Siloscape was detected in early March, and was named for it because the malware’s primary goal is to escape Windows containers through a server silo. The malware uses the Tor proxy and an onion domain to establish a connection to a C&C server, to which the data and commands intercepted by the hackers are sent.
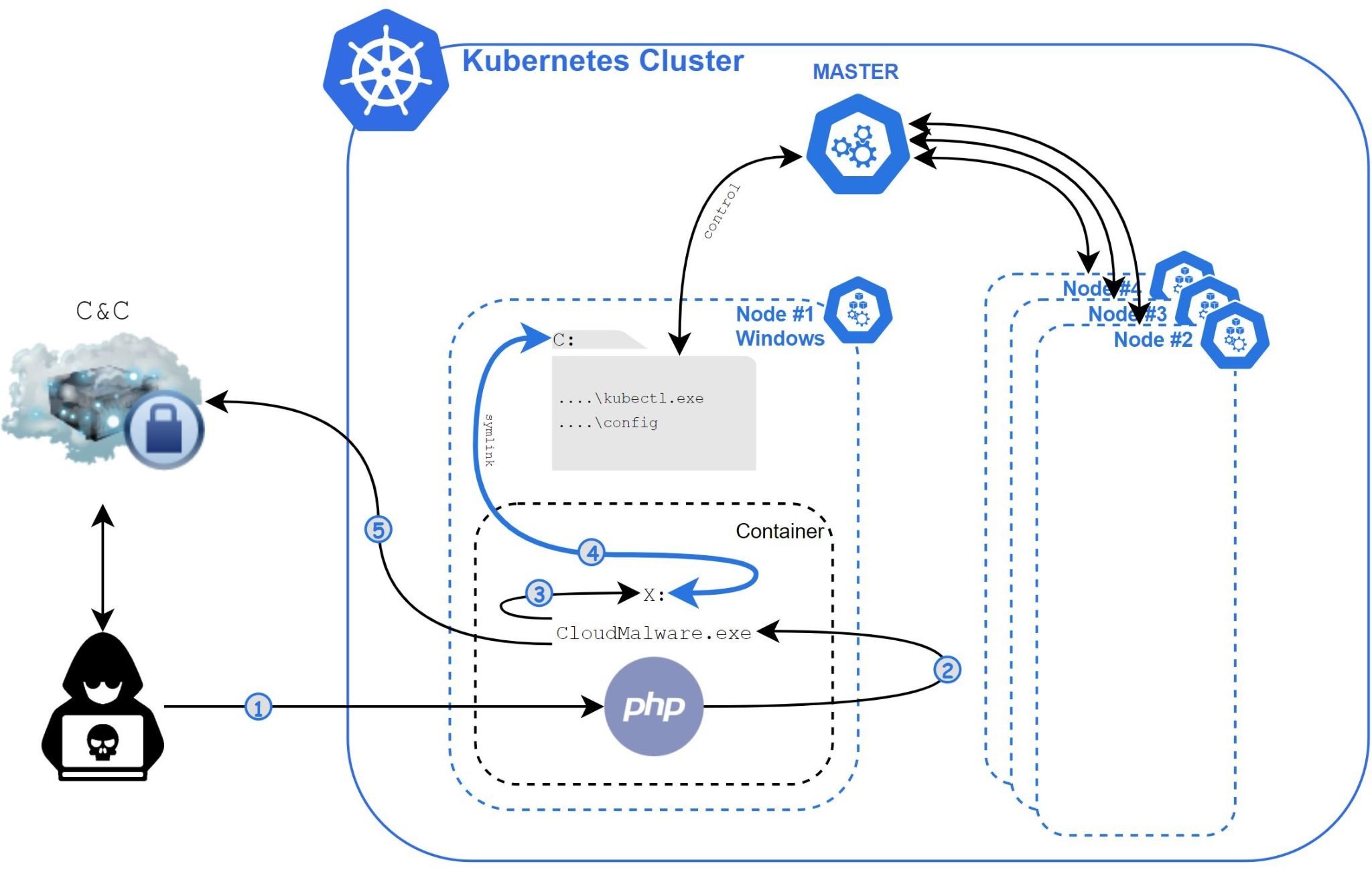
Siloscape operates under the CloudMalware.exe label, targeting Windows containers to launch attacks using known vulnerabilities that have not received updates, gaining initial access to servers, websites or databases.
Once access is gained, hackers will attempt to perform a remote code execution attack on a container’s underlying node using various hacking techniques, including CExecScv spoofing.exe: “The malware mimics CExecScv.exe privileges to invoke a newly created symlink to exit the container, linking its X drive into the container as the host’s C drive.” , the report states.
In a successful attack the threat actors will try to create malicious containers, stealing data from applications executed in malicious clusters and even loading tools for cryptocurrency mining, generating huge profits for the operators of the attack, who can go completely unnoticed.
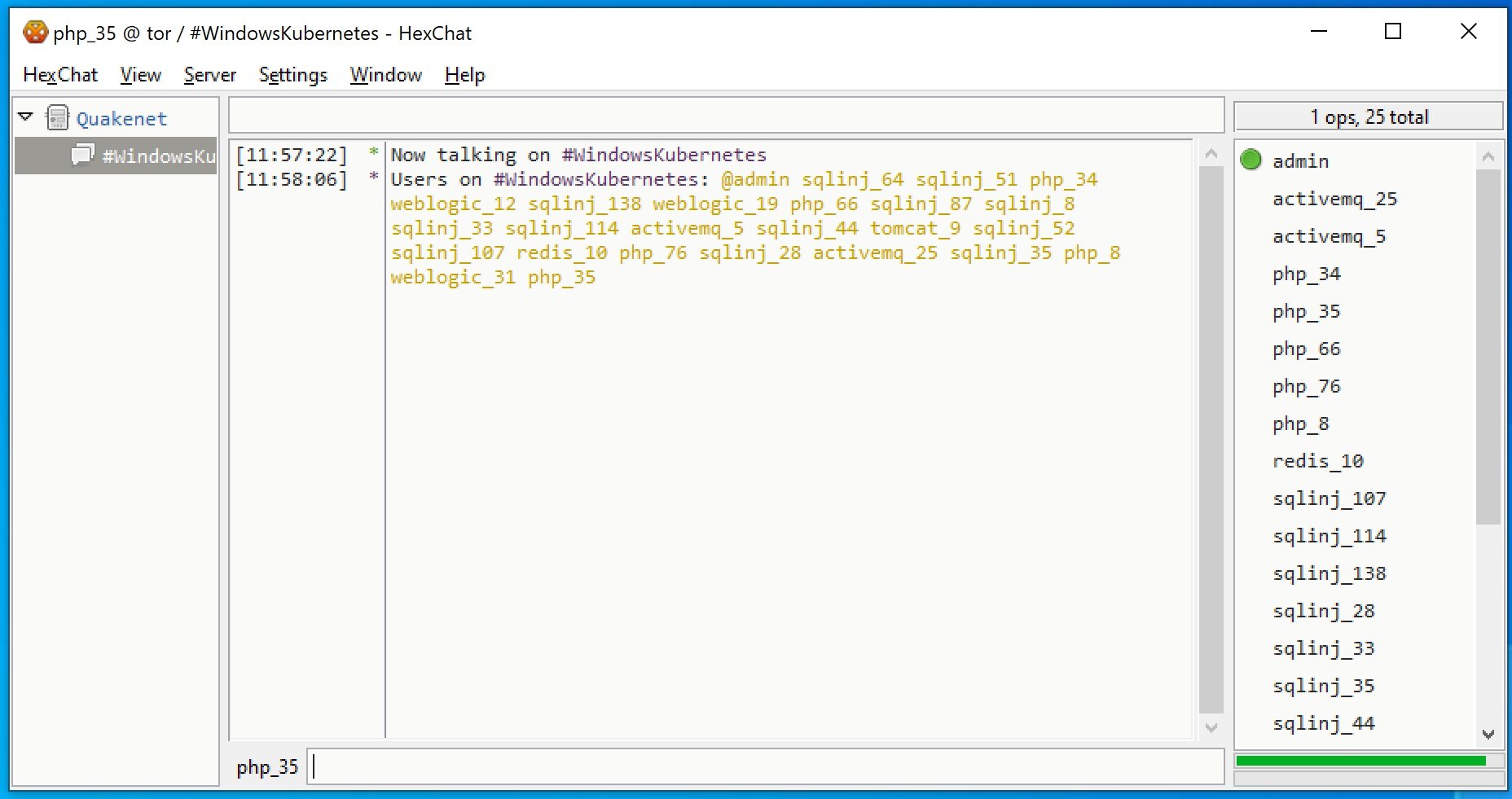
Malware developers focus especially on obfuscation, even to the point where functions and module names are only deprecated at runtime, complicating reverse engineering. Palo Alto researchers were able to gain access to C2 and identify at least 23 active victims, as well as 313 total victims, likely insured in campaigns over the past year.
Microsoft recommends that containers be implemented if this process is used as a form of security boundary rather than relying on standard Windows containers. On the other hand, the researchers added that Kubernetes clusters should be configured correctly and should not allow node privileges alone to be sufficient to create new deployments.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











