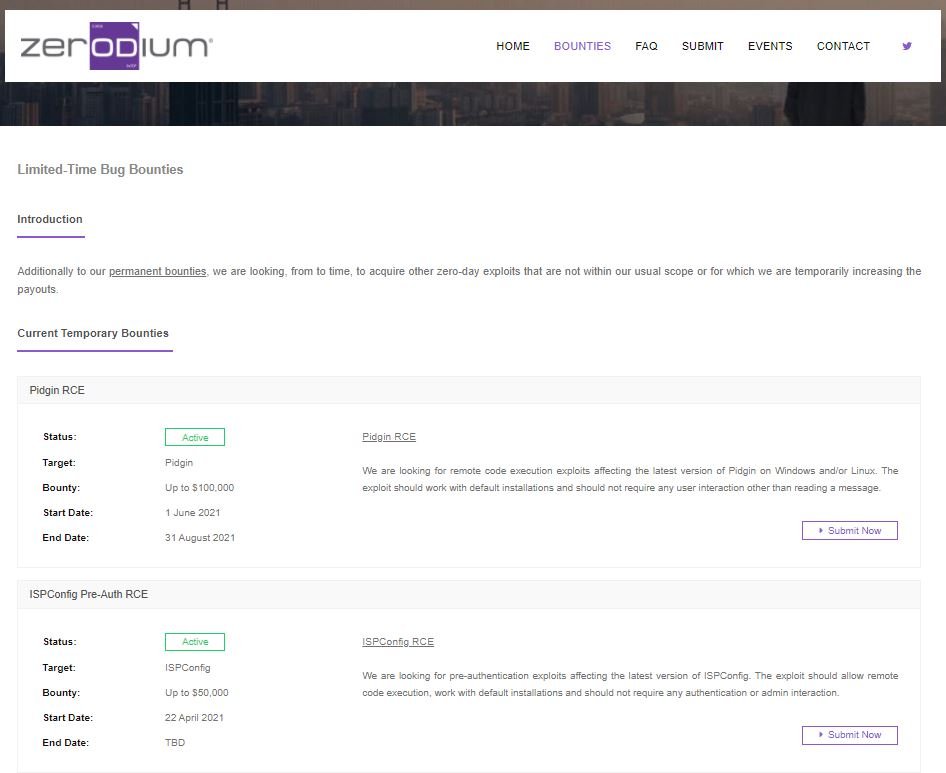
Zerodium operators announced a plan to pay up to $100,000 USD for zero-day flaws in Pidgin, the popular instant messaging client for desktop computers used by multiple cybercriminal groups: “We are looking for remote code execution exploits in the latest version of Pidgin for Windows and Linux systems” , the statement said. These flaws should work with the default installation, as well as requiring no target user interaction.
Zerodium, a technology firm dedicated to buying exploits for resale from government and research agencies, mentions that this is a project that will remain active until August 2021. The company activated this same program earlier to complete its exploits due to the increased detection of some specific attacks.
Even though the app has been used for legitimate purposes, the cybersecurity community agrees that Pidgin is essentially employed by many of the most important cybercriminal groups, mainly so that users can exchange messages using the XMPP or Jabber protocol.
To ensure that their conversations are kept private, criminal groups and underground communities often required each other to use OTR (Off The Record) or GnuPG encryption plugins, so pidgin’s arrival helped simplify many communication processes: “Cybercriminal groups moved from ICQ to Jabber about 20 years ago.” , mentions cybersecurity analyst Dmitri Smilyanets.
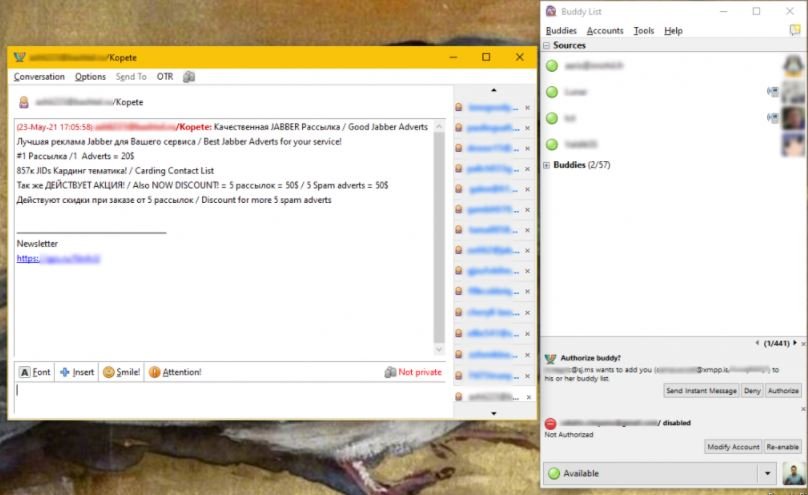
While the researcher mentions that this tool has been vital to many of the most important cybercriminal operations, implementations like Pidgin have lost ground to simpler tools: “Currently threat actors operate on platforms like Telegram and other services that provide total privacy and anonymity,” adds Smilyanets.
In addition to the zero-day vulnerabilities in Pidgin, Zerodium has also announced the activation of a special program for the purchase of exploits in WordPress and the ISPConfig web hosting panel, two tools that are often used in the deployment of cybercriminal operations.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











