Cybersecurity specialists report detecting a hacking group operating from Iran that has deployed multiple attacks and cyber espionage campaigns against Israeli organizations pretending to be a ransomware operation. This hacker group was identified as Agrius and would have been launching attacks since late last year.
Amitai Ben Shushan Ehrlich, researcher at security firm SentinelOne, says: “Agrius has deployed a series of powerful cyberattacks against multiple targets in Israel, hiding this targeted campaign as if they were common ransomware attacks.”
Agrius’ early attacks involved deploying a malware variant known as DeadWood, created to randomly delete data on infected systems. However, the latest reports indicate that hackers have left DeadWood behind, opting for a similar but more powerful version identified as Apostle.
This hacking group employs multiple attack vectors, including exploiting a vulnerability in FortiOS, SQL injection attacks and abusing some zero-day flaws: “We believe hackers use ransomware to hide their true intent, related to the mass deletion of information,” the experts add.
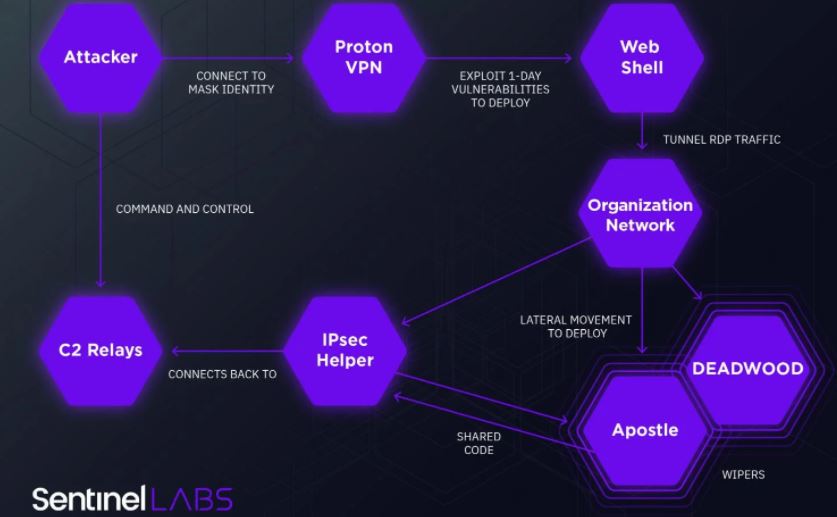
The experts’ claim is based on finding an earlier version of Apostle that hackers used exclusively to remove information from infected systems. This version failed due to an error in malware logic, so hackers had to continue developing the tool. The hacking group also created its own .NET malware identified as “IPsec Helper”, designed to provide hackers with a backdoor-like set of tools to access compromised hosts to deliver malware and steal sensitive information.
This is not the first hacking group to employ similar tactics targeting Israel. Previous reports indicate that the hackers of the APT33 group, also sponsored by the Iranian government, were behind the multiple incidents related to Shamoon malware, which works much like Apostle. Moreover, in 2019 the Agency for Cybersecurity and Infrastructure Security (CISA) issued a report on the increase in cybersecurity incidents potentially related to the Iran government. These attacks involved the use of powerful malware variants capable of removing huge amounts of sensitive information.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











