Cybersecurity specialists report that the personal information of around 100 million Android device users has been exposed due to incorrect security settings in a cloud storage deployment. This information was found in databases without the necessary protections, linked to about 23 applications with records of between 10,000 and 10 million downloads.
According to the experts who reported the incident, this is a sign of the poor security practices followed by Android developers, which undoubtedly poses a security risk. Researchers believe this is a widespread problem and easily exploitable by threat actors.
The report presented by Check Point researchers, mentions that some of the databases were unprotected and any user who knows where to look for this information can easily access it. The compromised information includes details such as:
- Full names
- Phone numbers
- Email addresses
- Dates of birth
- Texting
- Location details
- Gender
- Passwords
- Payment details
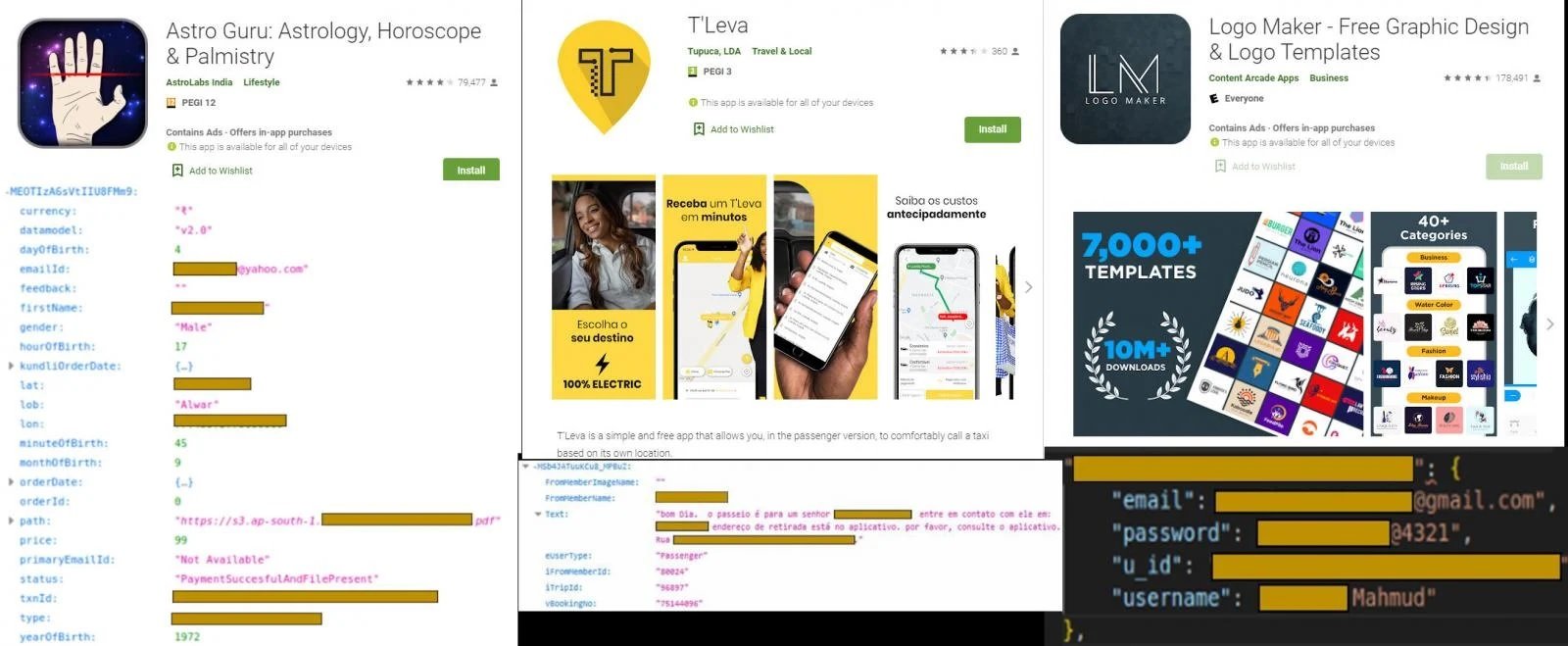
Most apps related to this leak are available on the Google Play Store and are relatively popular on the platform. Among the platforms involved with at least 10 million downloads are Logo Maker and Astro Guru; other less popular apps, such as T’Leva, rank in the range of 10,000 and 500,000 downloads.
Researchers also found sensitive information reserved for the developers of these apps, including credentials to access push notification services. Experts also found the cloud storage system access credentials for at least one app available from the Play Store.
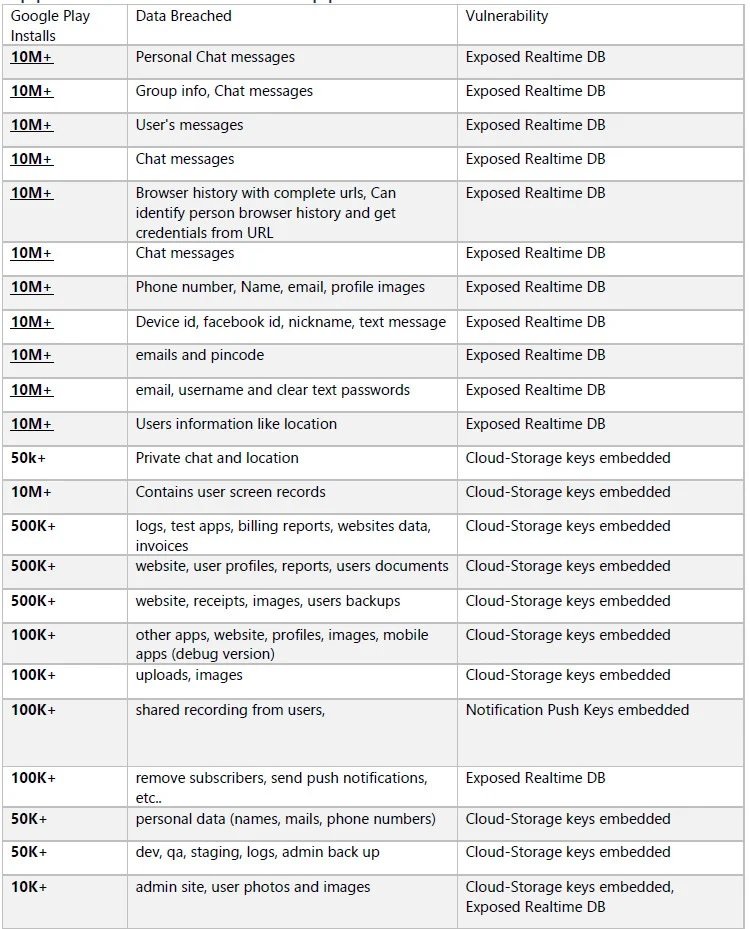
Finally, experts also discovered that the iFax app for Android also stored cloud storage keys and the database contained documents and fax transmissions from more than 500,000 users. However, experts also noted that some developers used the principle of security through darkness, obfuscating the secret calve using a base64 encoding.
Although the problem is not new, researchers are still surprised by the poor security practices employed by Android developers. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










