Attacks on ATMs on the street have evolved in great steps, leaving behind the methods of physical engagement of these machines to reach attacks using technology and advanced hacking capabilities. More recent analyses suggest that the most sophisticated method is currently known as “Black Box”, based on the use of a microcomputer with a single board.
This time, cybersecurity awareness specialists at the International Institute of Cyber Security (IICS) will show you the most important features of these attacks, which could lead to million-dollar losses to banking institutions. As usual, we remind you that this article was prepared for informational purposes only, so IICS is not responsible for the misuse that may be given to the information contained herein.
What’s inside an ATM?
Before we begin, it is worth remembering the composition of these machines. A typical ATM is a set of ready-to-use electromechanical components housed in a single enclosure. Manufacturers assemble machines from a banknote dispenser, card reader and other components already developed by third-party vendors. The finished components are housed in an area of the cashier consisting of two compartments: one upper (the service area) and one lower (the safe), mention cybersecurity awareness specialists.
All electromechanical components are connected via USB and COM ports to the system drive, which in this case acts as a host. In older ATM models, you can also find connections via the SDC bus.
On the evolution of attacks, threat actors previously exploited only physical weaknesses at ATMs, using devices known as skimmers to steal data from magnetic stripes, card numbers, or PINs. The transition to the use of hacking techniques came with the technological advancement of the manufacturers of these machines.
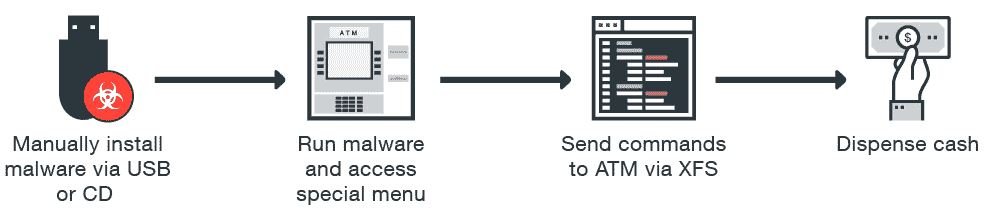
According to cybersecurity awareness experts, criminals now use malware variants (banking Trojans, skimmers, backdoors) to enter the target system host via USB drives or through the abuse of a remote access port.
How does an infection occur?
After capturing the XFS subsystem, malware can issue commands on the banknote dispenser or card reader without authorization for a variety of purposes, from reading the information from an entered card to extracting its confidential information stored on the card chip.
PIN Pad Encryption (PPE) deserves special attention. It is generally accepted that the PIN code entered into it cannot be intercepted. However, XFS allows you to use the EPP PIN keyboard in two modes: open (to enter various numeric parameters, such as the amount receivable) and secure (EPP changes to it when you need to enter a PIN or encryption key).
This XFS function allows the card to launch a Man-in-The-Middle (MITM) attack, intercepting the safe mode activation command that is sent from the host to the EPP, and then sending a request to the PPE PIN keyboard that continues in open mode. In response to this message, EPP sends hackers logs in clear text format.
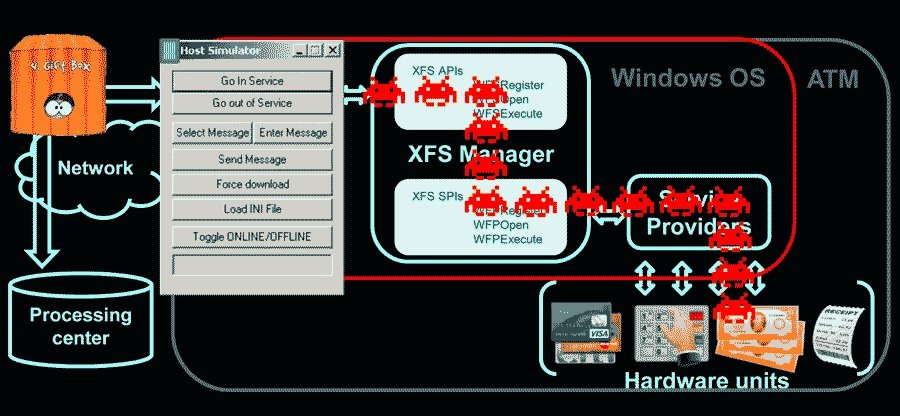
How does the Black Box attack work?
Members of Europol’s cybersecurity awareness team say that, over the past few years, a steady evolution in the development of ATM malware has been detected, so cybercriminals no longer require physical access to an ATM to complete the attack.
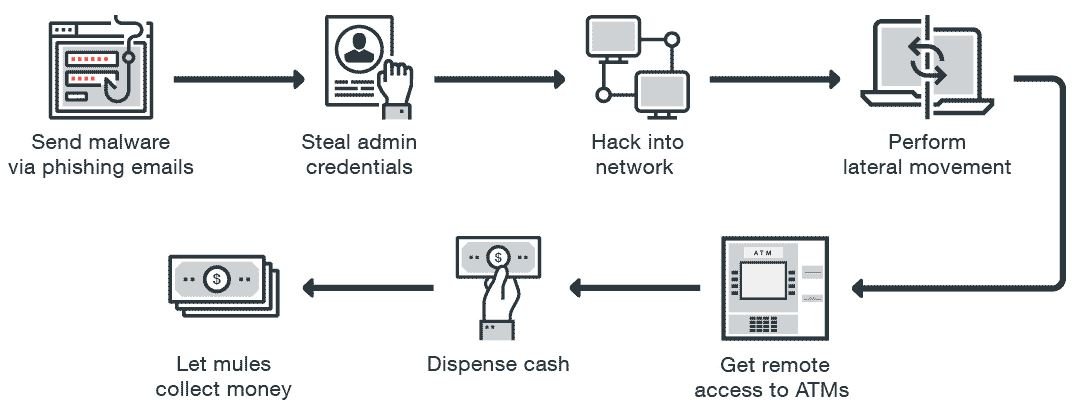
Worse, malicious campaigns can be deployed through a vulnerable bank’s own corporate network using the Black Box attack variant. Group-IB figures indicate that, since 2016, multiple such attacks have been detected in at least ten countries in Europe.
Remote access to an ATM
Antivirus solutions, firmware update blocking, USB port blocking, and hard drive encryption protect the ATM from some malware variants to some extent. But what if the card does not attack the host, but connects directly to the peripherals (via RS232 or USB), a card reader, PIN keyboard, or cash dispenser?
First contact with Black Box
Criminals with access to the most advanced hacking resources use these microcomputers with unique boards (such as Raspberry Pi) to empty ATMs, in an attack technique popularly known as jackpotting. In these attacks, criminals connect their devices directly to the cash dispenser to extract all the money stored at the cashier. This attack is able to dodge the security software implemented on the ATM host, cybersecurity awareness specialists say.

Major ATM manufacturers and government intelligence agencies mention that hackers can steal up to forty bills every 20 seconds. Agencies also warn that the main targets of these hackers are found in pharmacies, shopping malls and stores.
At the same time, not to stand out from the cameras, the most cautious criminals turn to the help of a third party known as “mule”, who will collect the stolen money to start distributing it. The BlackBox then connects to a smartphone, which is used as a channel for remote transmission of commands to a simplified Black Box over IP

In cases analyzed and recorded on video, a person can be seen opening the top compartment of the ATM by simply connecting the hacking device to the machine. A little later, several people approach the ATM and withdraw huge amounts of money. The hacker then returns and recovers his little magic device.
Analysis of ATM communications
As noted above, the system drive and peripherals communicate via USB, RS232, or SDC. The card connects directly to the peripheral port and sends you commands, without passing through the host. It’s quite simple because standard interfaces don’t require any specific drivers, cybersecurity awareness specialists mentioned.
On the other hand, proprietary protocols through which the peripheral and host interact do not require authorization, so these unprotected protocols, through which the peripheral and host interact, are easily heard and easily susceptible to a repeat attack.
Card users can use a software or hardware traffic analyzer by connecting it directly to a port on a specific peripheral device to collect the transmitted data. Using the traffic analyzer, the card learns all the technical details of the ATM’s operation, including its non documented functions such as changing firmware on a peripheral device. As a result, the attacker gains full control over the ATM and it is quite difficult to detect the presence of a traffic analyzer.
Direct control over the ticket dispenser means that ATM containers can be jackpotted without any restrictions.
How to address this problem?
ATM providers and subcontractors are developing debugging services to diagnose ATM hardware, including electromechanics responsible for cash withdrawals. These utilities include ATMDesk, RapidFire ATM XFS. The following figure shows some of these diagnostic tools.
Access to such utilities is usually limited to custom tokens and only works when the ATM safe door is open. However, by simply replacing some bytes in the binary utility code, a hacker can try to withdraw cash without going through the checks provided by the utility manufacturer. Thieves install these modified utilities on the single board microcomputer, which then connect directly to a banknote dispenser.
Communications Processing Center
Direct interaction with peripherals without communicating with the host is just one of the most popular ATM hacking techniques. Other techniques are based on the fact that we have a wide variety of network interfaces through which the machine communicates with the outside world, from x.25 to Ethernet and cellular networks.
As if that were not enough, many ATMs can be located using the Shodan IoT search engine, which can be chained to an attack that compromises the security settings of the affected machine.
The “last mile” of communication between the ATM and the processing center involves a wide variety of technologies that can serve as an entry point for threat actors, cybersecurity awareness specialists mention.
There are wired (telephone line or Ethernet) and wireless communication methods (Wi-Fi, cellular: CDMA, GSM, UMTS, LTE). Security mechanisms may include:
- VPN-compatible hardware or software (both standard, integrated into the operating system and third parties);
- SSL/TLS (both specific to a specific ATM model and third-party manufacturers)
- Encryption
- Message authentication
At best, the ATM connects to the VPN server and connects to the processing center within the private network. In addition, even if banks manage to implement the above protection mechanisms, the hacker already has effective attacks against these reactive measures. So even if security complies with PCI DSS, ATMs remain vulnerable.
One of the main requirements of PCI DSS is that all sensitive data must be encrypted when transmitted over a public network. However, many of these networks do not provide sufficient protection, so they don’t actually protect against major hacking variants, cybersecurity awareness experts mention.
Therefore, either in an unsafe communication or in a “private” network, where each ATM transmits over itself to other ATMs, a MiTM attack can be initiated, which will lead the card to take control of the data flows transferred between the ATM and the processing center.
Thousands of ATMs are potentially vulnerable to this attack variant. On the way to a genuine processing center, the hacker inserts his fake. This fake processing center instructs the ATM to deliver the tickets. At the same time, the threat actor configures your processing center in such a way that cash is issued regardless of the card being inserted into the ATM, even if its validity period has expired or your balance is zero.
The main thing is for the fake processing center to “recognize” it. A fake processing center can be crafty or a processing center simulator originally designed to debug network settings. The following figure shows a command dump to issue forty banknotes from the fourth cassette, sent from a fake processing center and stored in ATM software journals. They almost look real.

Conclusions
Cybersecurity awareness specialists often say that a truly protected computer is in an iron box and is not connected to any network, including electrical ones. This is true, as virtually any implementation is vulnerable and bank ownership is no exception.
Recently, the head of ATM Association International (ATMIA) stressed that the BlackBox attack is the most serious threat to ATMs, so manufacturers, banking institutions and researchers need to establish the best way to address this risk. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.










