Cybersecurity specialists report that a hacker or hacker group has been adding malicious servers to the Tor network in order to intercept traffic and perform an SSL attack variant targeting users who frequently visit cryptocurrency related websites. These attacks began in early 2020 and consist of adding servers to the Tor network to mark them as “outbound relays”, which are the servers through which traffic leaves the confidential network to re-enter the conventional Internet after anonymization.
Attackers have identified traffic to cryptocurrency websites to perform an SSL certificate deletion attack, which occurs when traffic on HTTPS connections is degraded to HTTP in plain text. Researchers believe that threat actors have been degrading traffic to HTTP in order to replace legitimate cryptocurrency addresses with those controlled by hackers.
The attacks were initially first detected by tor’s security researcher and operator known as Nusenu in January 2020 and have since been widely documented. The researcher mentions that the attackers managed to infest the Tor network with malicious output relays on at least three occasions, reaching almost 23% of the output capacity of the entire Tor network in each attack attempt.
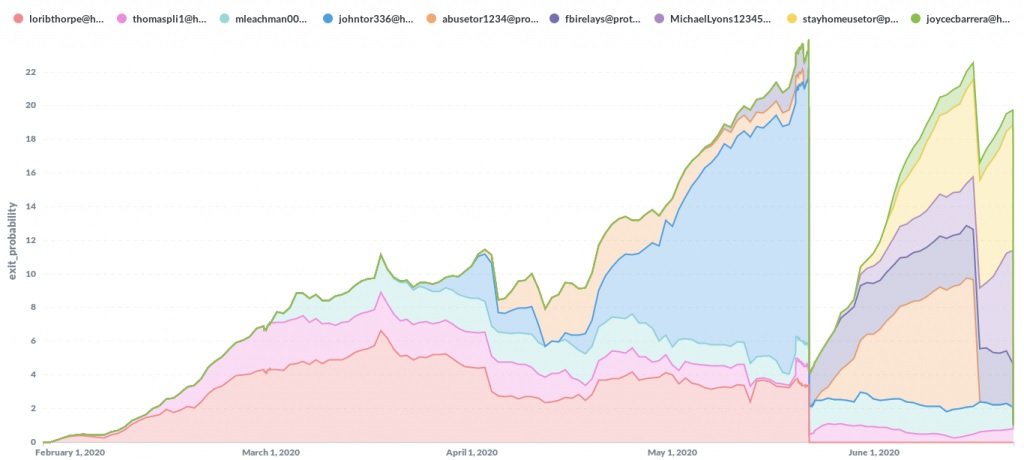
Although the activities of these attackers are well known, experts point out that the attacks have not stopped, as an incident has even been detected that is still active and has already reached almost 25% of the output capacity of the Tor network.
This new wave of attacks was recently detected, with malicious Tor output relays being removed from Tor’s network until after the attack infrastructure remained active for at least a month.
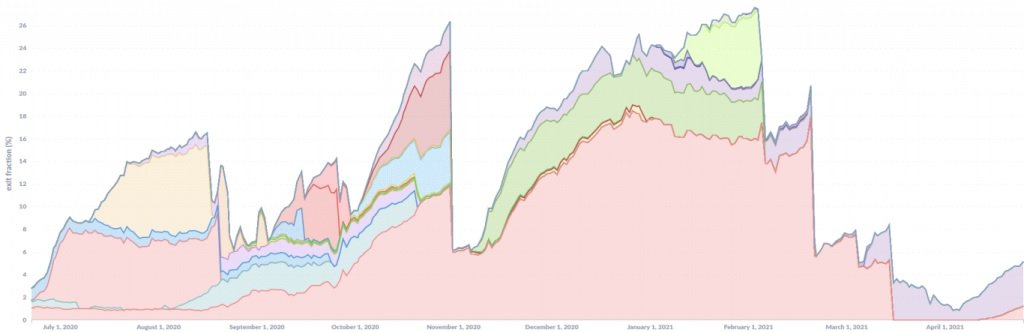
According to experts, the main reason the attacks worked for more than a year was because hackers added output relays stealthily and consistently, so malicious activity was detected until the attackers had already achieved their target. After the attack was interrupted, the hackers modified their mode of operation and tried unsuccessfully to bring all servers online at the same time.
Nusenu concluded by mentioning that since last year, attackers also appear to be making download modifications after performing SSL strip attacks, although it is unclear what exactly it is manipulating or whether it is just a technical change. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











