Cybersecurity experts report that a hacking group has developed a complex rootkit to perform backdoor tasks on Windows systems. As you will remember, a rootkit is a malicious tool designed to evade security mechanisms on a computer system to deploy subsequent attacks.
This new malware, identified as Moriya, was discovered by Kaspersky researchers and is described as a backdoor that allows threat actors to spy on network traffic on affected systems and send arbitrary commands to compromised hosts.
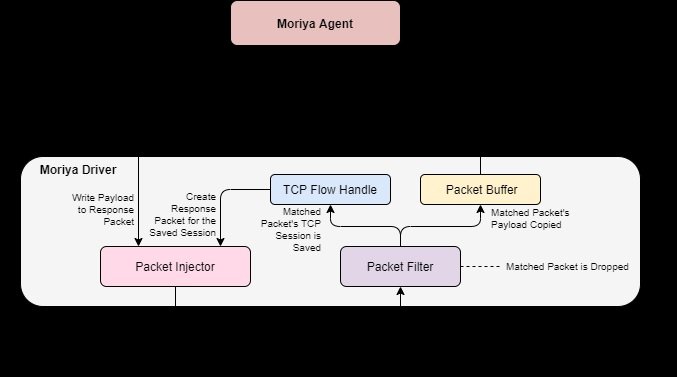
According to experts, Moriya allows its operators to capture and analyze incoming network traffic from the Windows kernel address space: “This backdoor receives commands very stealthily and through custom packets hidden within the victims’ network traffic, without having to communicate with a C&C server.” Researchers mention that such campaigns are becoming more common, so it’s not really strange to see such malware in real-world scenarios.
The malware would have been implemented on the networks of at least 10 organizations, indicating that it is a highly targeted attack. The attackers employed compromised systems belonging to diplomatic entities in Asia and Africa, accessing committed resources to take control of their networks and generate persistence for months.
Attackers also deployed additional tools during the post-exploitation stage on compromised systems. Apparently, this allowed them to move laterally on the network after searching for and finding new vulnerable hosts on the victims’ networks.
While the researchers were not completely sure about the authorship of these attacks, other members of the cybersecurity community point out that the tactics, techniques and procedures used in this attack campaign are attributable to any of the most notable Chinese hacking groups.
Finally, Kaspersky published a broader report on Moriya and its advanced hacking capabilities. This is the second report of these features recently released by Kaspersky; in October 2020, the security firm published a report on UEFI, a variant of rootkit used in multiple attacks on non-governmental organizations based in Europe and the United States.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











