Officials from the Court of Justice in Rio Grande do Sul, Brazil, confirmed that their computer systems were affected by a ransomware attack that encrypted employee files and forced the closure of court networks. Apparently, the attack was deployed by the operators of the REvil ransomware.
Everything indicates that the attack would have begun on Thursday morning, when multiple employees discovered that something prevented them from accessing their documents and images, and that a copy of the ransom note had appeared on the screens of all affected machines.
Shortly after the attack began, the court’s official Twitter account began warning employees not to log in to TJ network systems locally or remotely: “The TJRS reports that it faces instability in computer systems. The system security team advises internal users not to access computers and log on to computers within the network,” the security alert says.
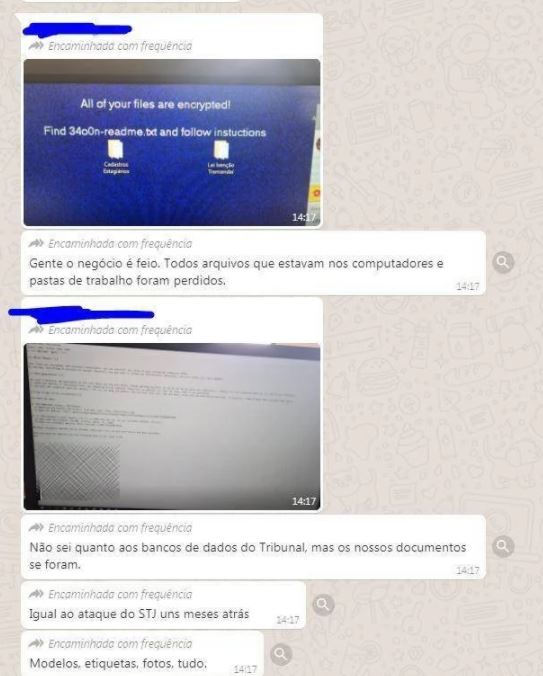
On the other hand, a Brazilian cybersecurity specialist shared a screenshot in which some employees exchanged their opinions regarding the attack, as well as showing their surprise at finding the ransom notes sent by the hackers.
A separate report mentions that REvil hackers demanded a $5 million USD ransom in exchange for restoring access to encrypted systems and not disclosing compromised information.
This is not the first time a ransomware attack has compromised Brazil’s judicial systems. Last November, Brazil’s Superior Court of Justice was attacked by RansomEXX ransomware operators who began encrypting devices just during a court session via a video conferencing platform. At the same time, websites of other Brazilian federal government agencies were disconnected as a security measure at the risk of an extended attack.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











