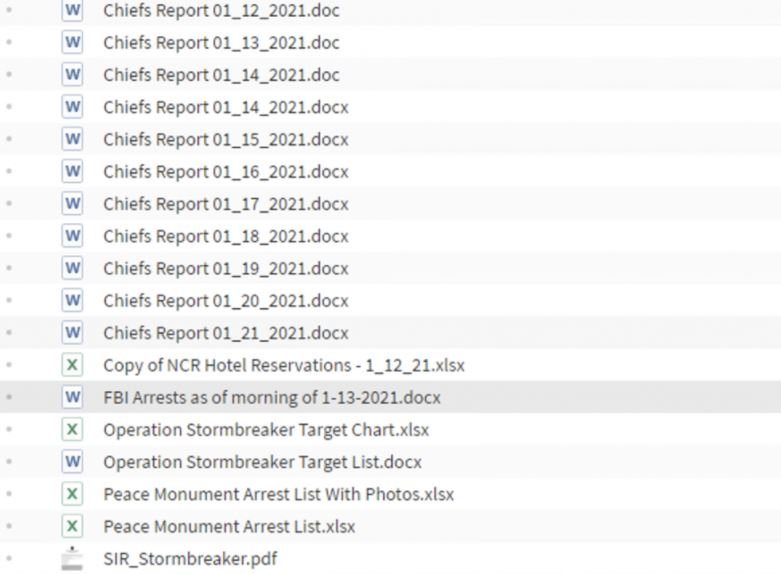
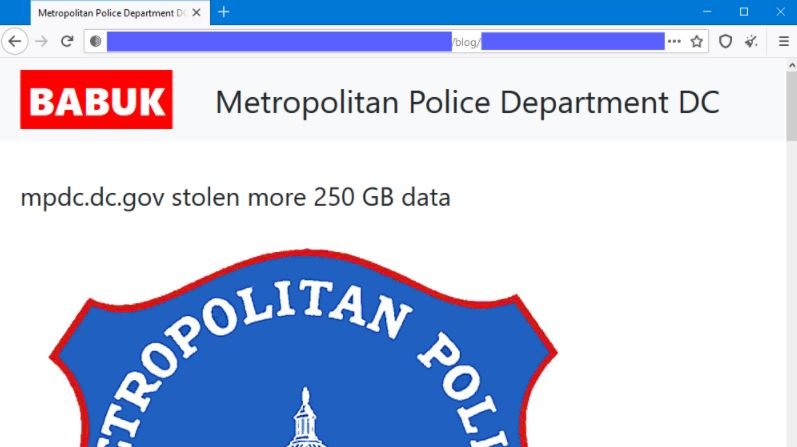
A group of ransomware hackers has released a statement threatening to expose confidential files from the Metropolitan Police Department of the District of Columbia, Washington D.C., unless law enforcement authorities authorize payment of a large ransom.
Threat actors added some screenshots of the police department’s internal files and servers, resources that were affected with the Babuk Locker ransomware variant. Police agency spokesman Sean Hickman acknowledged the intrusion into these systems: “We are aware of unauthorized access to our servers.”
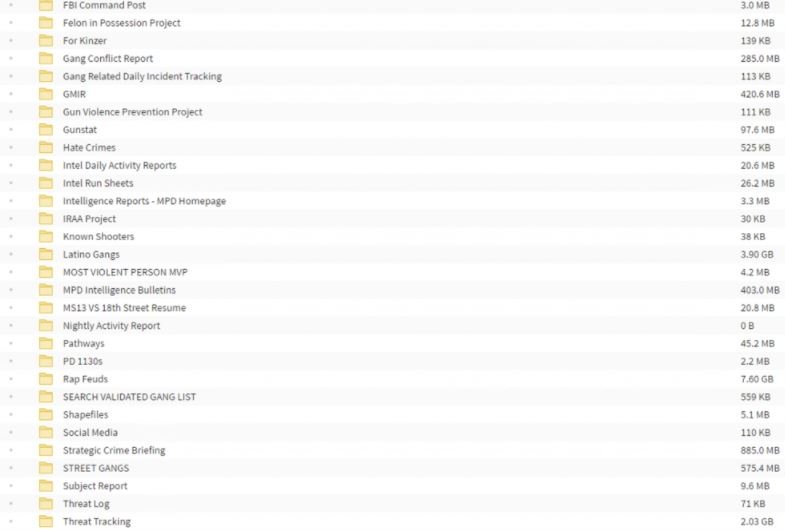
Cybersecurity experts with access to this information report that hackers would have gained access to investigative reports, personal records from some police officers, reports on local gangs, plus hundreds of photographs and internal documentation.
Babuk’s experts say the leak includes more than 250 GB of information extracted from police servers, as well as noting that the agency was granted a 3-day deadline to make the ransom payment. In case the police refuse to negotiate, hackers threaten to expose the officers’ files and even share them with local criminal groups.
The police department spokesman added that the incident is still being investigated to determine the actual impact, which is already supported by a specialized unit of the Federal Bureau of Investigation (FBI).
About Babuk, experts mention that it is one of the most common ransomware variants today. Although it was only detected in January 2021, this malware variant has already been detected in attacks against companies such as Phone House and the systems of the Houston Rockets, NBA team.
Along with variants like Darkside or RansomExx, Babuk is characterized by the ability to encrypt files stored on shared virtual hard drives, one of the most dangerous trends in the world of ransomware. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.