Cybersecurity experts point out that the Darkside ransomware controller group has added new extortion tactics to its mode of operation, primarily targeting companies listed on the stock exchange. Through their dark web portal, hackers claim that they are willing to notify sellers of confidential information on the black market so that they can reduce the price of a company’s shares before including it on their portal as victims, which could reduce the value of the shares of these companies.
On the other hand, hackers believe that the negative impact of having a company name on their list of compromised targets is already enough to cause a drop in the price of their actions: “While other ransomware groups have noticed that their operations can generate this kind of impact, experts mention that this could be the first time a threat actor makes this their main attack vector” , the experts mention.
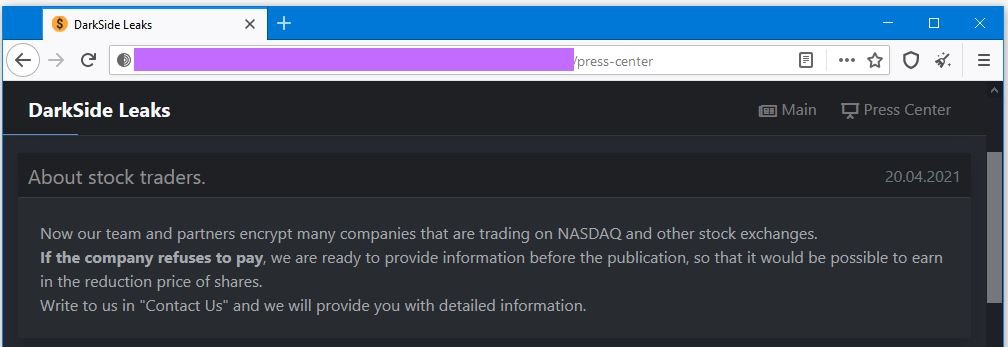
This announcement also works as an indirect method to threaten compromised companies that don’t want to collaborate with hackers. This approach is just the latest in a long list of techniques that ransomware hackers have been adding to their attack tactics, including:
- Phone calls to threaten victims
- Personal threats against executives responsible for approving ransom payment
- Threats to notify business partners of affected companies
- Deployment of denial of service (DoS) attacks against affected companies
These tactics are usually implemented once ransomware gangs learn that compromised companies refuse to pay the ransom as a pressure mechanism towards victims.
In this regard, cybersecurity specialist Allan Liska mentions: “We have anecdotal evidence that fewer and fewer users are giving in to the demands of hacking groups. This has led threat actors to find ways to force payment, which could result in financial impact on affected companies.”
Even so, Liska concludes by mentioning that, in its view, this extortion model is unlikely to be maintained in the medium term, as while an initial report could cause panic among the affected companies, the prices of its shares cannot be determined by such incidents.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











