A recent security report mentions that a dark web leak containing access keys has been published to more than 1.3 million Windows Remote Desktop servers. This is a clear indication of the scope of cybercrime and could even be binding on other incidents of which cybersecurity community knows little.
It’s not all bad news, as network administrators will also benefit from a new service launched by advanced cybersecurity firm Advanced Intel called RDPwned that allows you to verify whether an organization’s RDP credentials have been sold on the hacking black market.
As users may remember, Remote Desktop Protocol (RDP) is a Microsoft remote access solution that allows users to remotely access applications and the desktop of a Windows device. Due to their frequent use in corporate networks, malicious hackers develop an important market around the theft and sale of stolen access credentials to multiple public and private organizations.
Ultimate Anonymity Services (UAS) is a platform where developers can purchase Windows Remote Desktop login credentials, social security numbers, and access to SOCKS proxy servers. According to cybersecurity experts, the most prominent feature of UAS is that potential customers can manually verify the credentials of sold RDP accounts, as well as request customer service services and usage guides for stolen information.
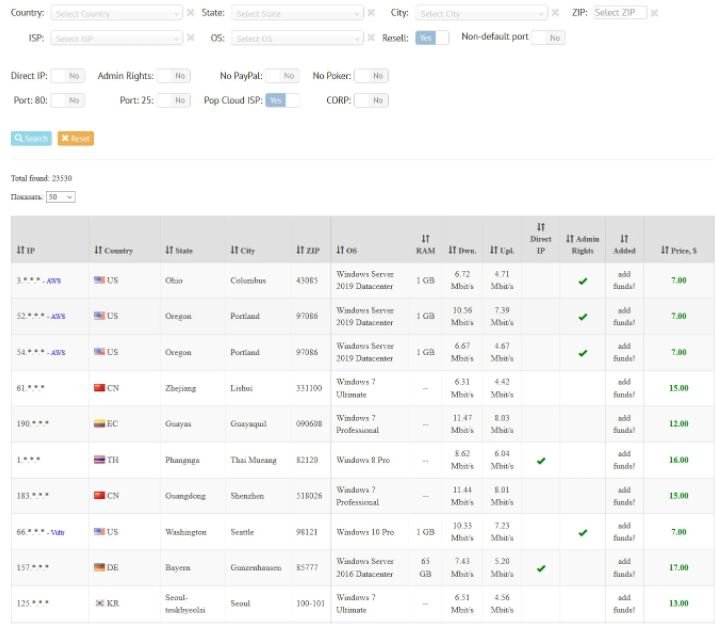
Potential clients can drill down into each server to see the number of Windows accounts, Internet connection speed, server hardware, and more, as shown below.
According to the latest reports, UAS is selling at least 23,000 RDP access credentials.
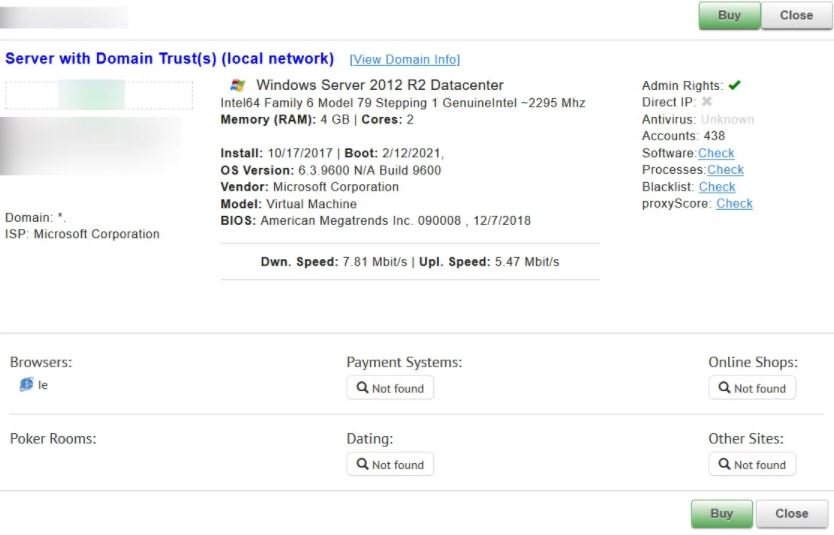
Cybersecurity specialist Vitali Kremez launched a service called RDPwned, which any individual user or organization will be able to use to find out if their servers are in the databases of hacking platforms such as UAS: “RDPwned will help administrators learn more about previous security incidents, as well as be able to resolve issues before they become a massive commitment to their assets.”
To use the service, Kremez mentions that companies would have to submit the contact information of an executive or company administrator. Once the user’s identity is verified, Advanced Intel experts will confirm whether the company’s servers are listed in RDPwned. Visitors can perform this search through reverse DNS, IP addresses, and domain names.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











