Cybersecurity specialists reported the finding of nine vulnerabilities in Domain Name System (DNS) protocol implementations on TCP/IP communication stacks present on about 100 million devices. This set of flaws, dubbed as NAME:WRECK, could be exploited to take control of the affected devices.
The find was made by experts from Enterprise of Things Forescout and JSOF, a cybersecurity unit operating in Israel. According to the report, flaws affect DNS implementations of the following TCP/IP stacks:
- FreeBSD v12.1
- IPnet VxWorks 6.6
- NetX v6.0.1
- Nucleus NET v4.3
Experts point out that a threat actor could exploit these flaws to deploy dangerous attacks targeting servers in public and private organizations of all kinds, including energy, medical, industrial and commercial services infrastructure, modifying the configurations of these computers for malicious purposes.
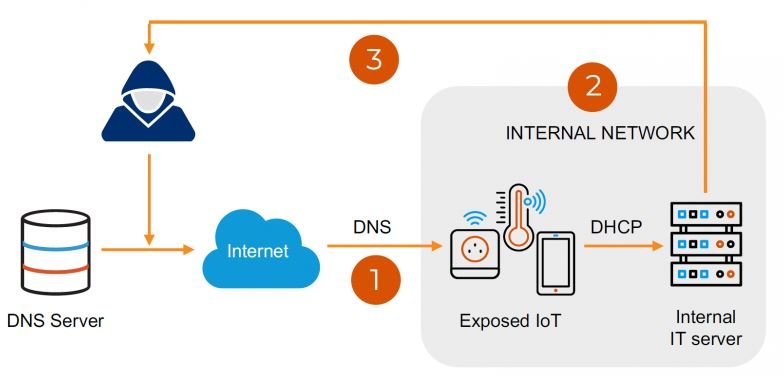
Threat actors may also alter some critical functions in business, commercial, or even residential environments, such as modifying a building’s heating and ventilation, disabling its security systems, or altering the normal operation of the lighting system.
Apparently, part of the problem has to do with the message compression feature in the protocol, which allows you to reduce the size of DNS messages in the process. According to Forescout, this feature is also present in many implementations, although some protocols do not officially support compression. This occurs due to code reuse or a specific understanding of specifications.
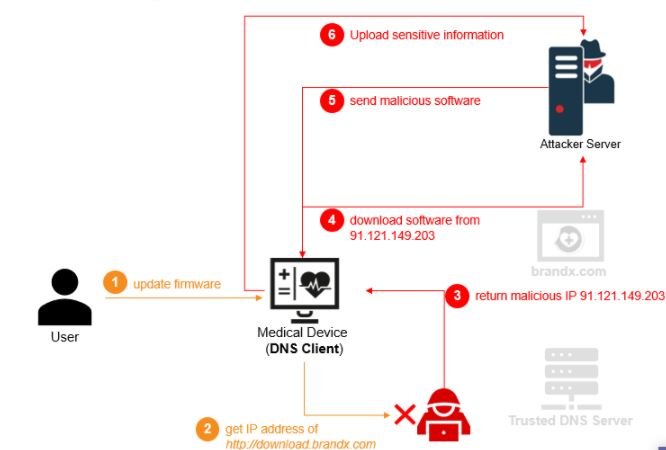
Experts stress that implementing the compression mechanism has been a difficult task, as more than a dozen vulnerabilities discovered since the beginning of the 21st century stand out. It should be noted that not all NAME: WRECK flaws can be exploited to achieve the same results. Below is a list of reported flaws and their assigned scores according to the Common Vulnerability Scoring System (CVSS).
- CVE-2020-7461: Boundary error in FreeBDS when analyzing OPTION 119 data in DHCP packets in dhclient (8). The flaw received a score of 7.7/10
- CVE-2016-20009: IPnet stack-based overflow in message decompression function. This flaw received a score of 9.8/10
- CVE-2020-1579: DNS name tag analysis functionality in Nucleus NET does not correctly validate names in DNS responses. CVSS score of 8.1/10
- CVE-2020-27009: DNS domain name record decompression functionality in Nucleus NET does not correctly validate pointer offset values. Vulnerability received CVSS score of 8.1/10
- CVE-2020-27736: DNS domain name tag analysis functionality in Nucleus NET does not correctly validate the name in DNS responses. The flaw received a score of 6.5/10
- CVE-2020-27737: DNS response analysis functionality in Nucleus NET does not correctly validate multiple lengths and counts of records. Vulnerability received a score of 6.5/10
- CVE-2020-27738: DNS domain name record decompression functionality in Nucleus NET does not correctly validate pointer offset values. This error received a CVSS score of 6.5/10
- CVE-2021-25677: Dns client in Nucleus NET does not correctly randomize DNS Transaction ID (TXID) and UDP port numbers. The flaw received a score of 5.3/10
- No CVE key assigned: Two functions in the DNS resolver of NetX do not check what the compression pointer does. The flaw received a CVSS score of 6.5/10
As mentioned at startup, successful exploitation of these flaws would allow threat actors to deploy denial of service (DoS) attacks, DNS cache poisoning, and remote code execution (RCE).
Affected deployment administrators are encouraged to go to official sources for more information on launching security patches or workaround methods to prevent exploitation. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










