Specialists at security firm Check Point detailed the finding of a new WhatsApp session hijacking attack in which threat actors employ a malicious app disguised as a legitimate Netflix tool. According to the report, malicious hackers somehow managed to place their app, identified as “FlixOnline”, in the Google Play Store, the official repository for Android apps.
Like other recently detected attack variants, this campaign seeks to take advantage of the prolonged period of isolation by the pandemic, which has been noticed in multiple ways, including increased use of streaming platforms.

On its download page, the fraudulent app promised users interested in subscribing to Netflix a free two-month subscription as a special pandemic promotion: “2 months of Netflix Premium free FOR QUARANTINE REASON (CORONA VIRUS). Get 2 months of free Netflix Premium anywhere for 60 days. Get it now HERE https://bit(.)Ly/3bDmzUw,” mentioned the app’s description in a clearly misspelled advertisement.
However, users were unaware that by downloading this app they would also be installing FlixOnline malware on their devices, which would allow threat actors to snoop on their WhatsApp accounts and even enable an automatic response protocol to other users to spread more malicious content, including malware, spam and fake news.
Another indication of suspicious activity related to this app are the requested permissions, since FlixOnline requested overlay permissions and disabled the ability of devices to automatically close the app when detecting high power consumption, not to mention that this malicious app was able to automatically respond to messages from the victim.
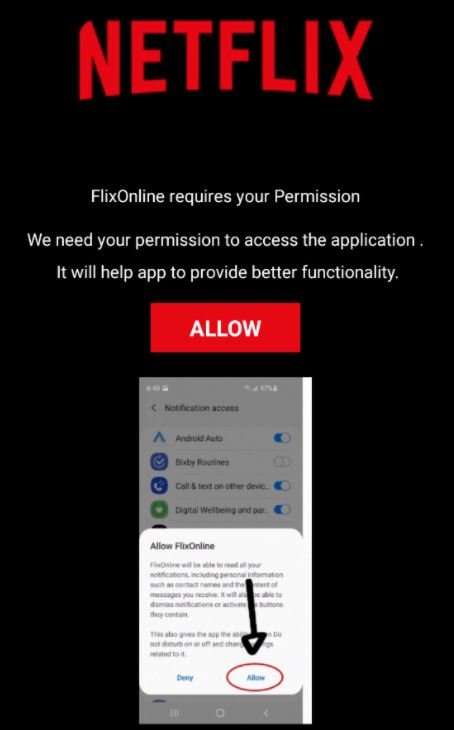
This attack also depends on a fraudulent website similar to that of Netflix where threat actors will try to trick the user into entering their credit card details. Check Point experts also mention that the C&C server operating these platforms could also be linked to other hacking campaigns.
Experts believe that at least 500 users have fallen into the FlixOnline trap, which has operated for at least two months. The report was submitted to Google, so the app has already been removed from the Play Store, although experts anticipate that the operators of this malicious app will attack again. The report was also submitted to WhatsApp, although this is not considered a security flaw affecting the instant messaging platform.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











