During the first quarter of 2021, denial of service (DoS) attacks became one of the world’s leading cybercriminal trends, in part thanks to the combination of this technique with extortion campaigns against relevant targets, including public and private organizations.
One of the biggest victims of this attack variant, known as Ransom DDoS (RDoS), is web security firm Akamai, whose systems were affected by a massive DoS condition that led to the demand for a ransom payment: “In February this year, we had to deal with three of the six largest DoS attacks ever recorded,” the company said.
Akamai also detected two separate incidents that reached volumes never before seen and apparently targeted an online betting company based in Europe, in what researchers described as a highly complex RDoS attack: “Since the start of this campaign, threat actors have demonstrated a large amount of resources, reaching an attack power of more than 800 Gbps in February 2021”, the report states.
Reports indicate that threat actors used a completely new approach to deploy the attack, taking advantage of the Datagram Congestion Protocol (DCCP), also known as Protocol 33: “This approach allows bypassing the defenses established for TCP and UDP traffic flows, which are the resources most commonly used in such attacks,” the experts mention.
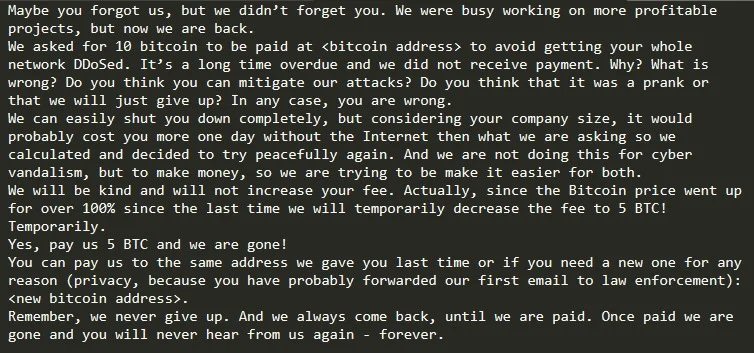
On the other hand, the specialized firm Radware points to the detection of a massive RDoS attack campaign that would have begun in late 2020 or during the first week of 2021. The operators of this campaign would have demanded a ransom of up to 10 Bitcoin in each extortion attempt. The main indicator that all attacks would have been perpetrated by the same hacking group is the ransom note received by the affected companies.
On extortion methods, hackers began to cause severe failures in affected systems just a couple of hours after sending the extortion note to victims. Akamai confirmed that its customers went through similar episodes, noting that “the 2021 RDoS campaigns have become more specific and much more persistent.” In specific Akamai described attacks on two organizations that viewed their systems disrupted for nearly a full week. The company mentions that the hackers had done an outstanding reconnaissance work before launching the attack.
Another trend recently detected is the increase in DDoS attacks above 50Gbps.
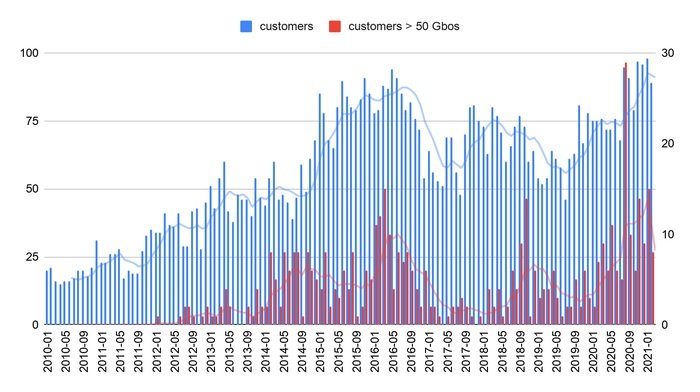
Attacks of greater magnitude than all recorded during 2019 have been reported in less than three months of 2021, demonstrating the advancement of this malicious practice around the world.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











