Operators of the Clop ransomware (also identified as Cl0p) posted an update on their website to claim that they managed to access confidential information from students and staff from the six most prestigious universities in the United States.
Threat actors claim to have compromised the systems of the following academic institutions:
- The Yeshiva University
- The Stanford University
- The University of Miami
- The University of Maryland
- The University of Colorado Boulder
- The University of California, Merced
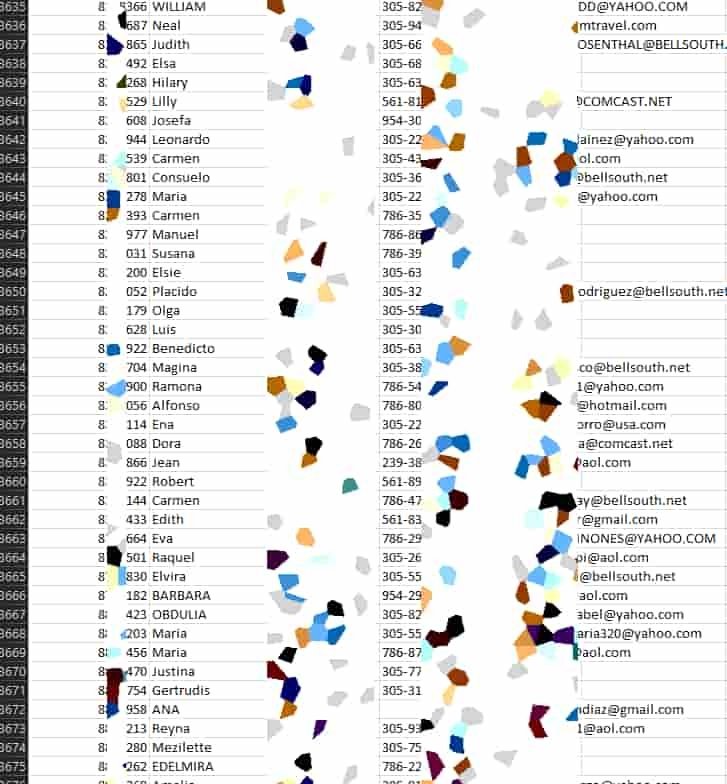
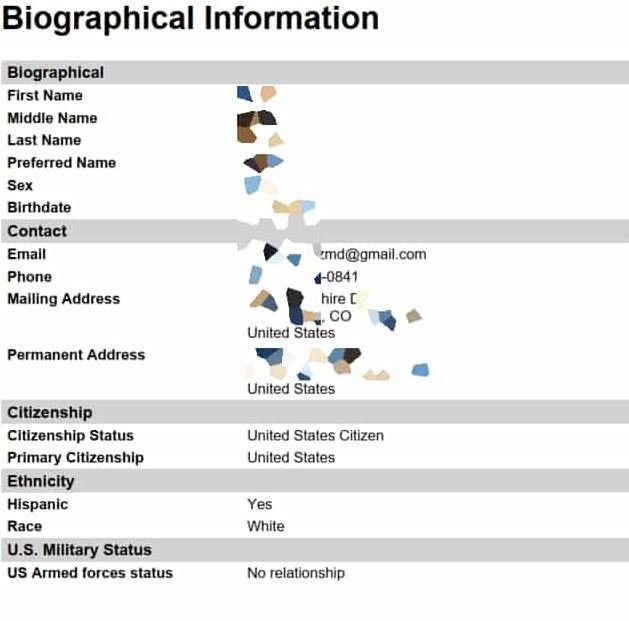
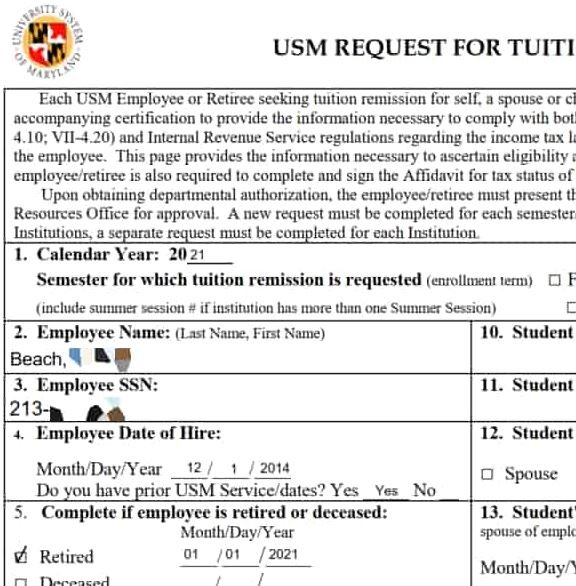
Cybercriminals posted screenshots regarding tax documentation, admission applications, nursing reports, passports, and tax summaries documents. Sensitive data such as:
- Photos
- Dates of birth
- Addresses
- Passport numbers
- Immigration status
- Full names
- Social Security numbers
Other unpublished screenshots may contain sensitive details such as social security numbers, retirement documents, benefit applications for the period 2019/202, as well as including employee late enrollment application forms and applications to enter some savings programs.
It is important to specify that this is a common practice of the operators of the Clop ransomware, used as a pressure method to force victims to pay the ransom. This is one of the most popular cybercriminal groups in the practices of “double extortion”, which involves the commitment of a system and the theft of confidential information to threaten victims with its publication.

So far the universities under attack have not spoken out about it, so there is no official confirmation of the incident.
Ransomware groups remain one of the main security risks, so it is necessary to have information on the latest cybercriminal trends today. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.