Through a recently published statement, Acer security teams revealed that their computer systems have been affected by an infection of the REvil ransomware. Early reports say threat actors demand a $50 million payment in exchange for restoring systems to normal.
As proof of this attack, malicious hackers shared some screenshots of the compromised systems on their platform hosted on dark web. Published images include spreadsheets, bank balances, and evidence of internal communication.
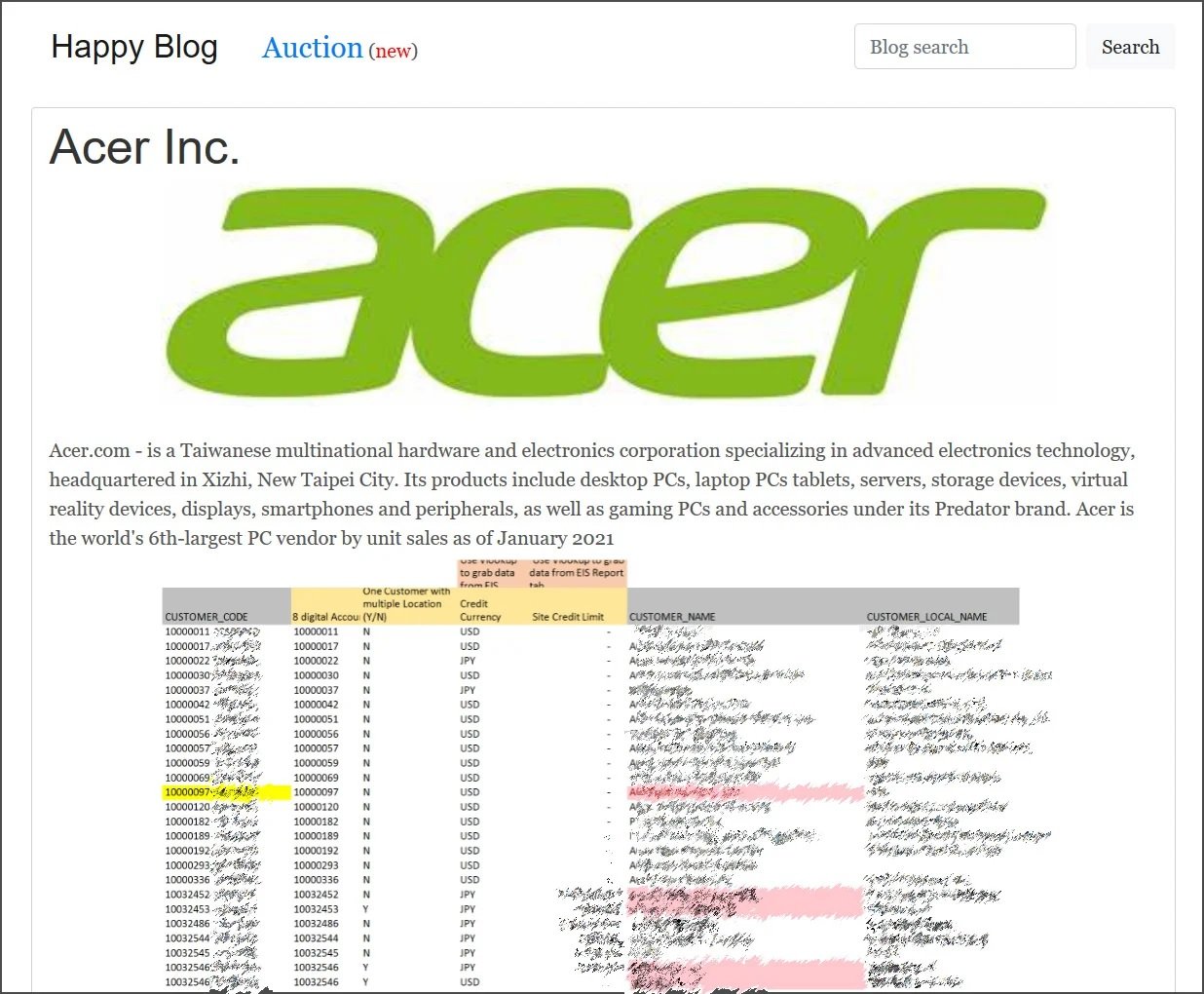
In its message, the company mentions that they are addressing the incident, as well as implementing measures to prevent subsequent attacks: “We are monitoring our IT systems for any new signs of anomalous behavior. The improvement of our security mechanisms is ongoing and we want to assure our customers and employees that this problem will not jeopardize your sensitive information.”
On the features and technical details of the attack, such as the ransomware variant used by hackers, the company merely mentioned that the investigation is still ongoing and for the time being it is impossible to provide more information.
Shortly after Acer confirmed the infection, researcher Valery Marchive revealed that the attack was carried out with the dangerous variant of REvil ransomware. In addition, a subsequent leak of the ransom note received by Acer confirmed the information submitted by Marchive.
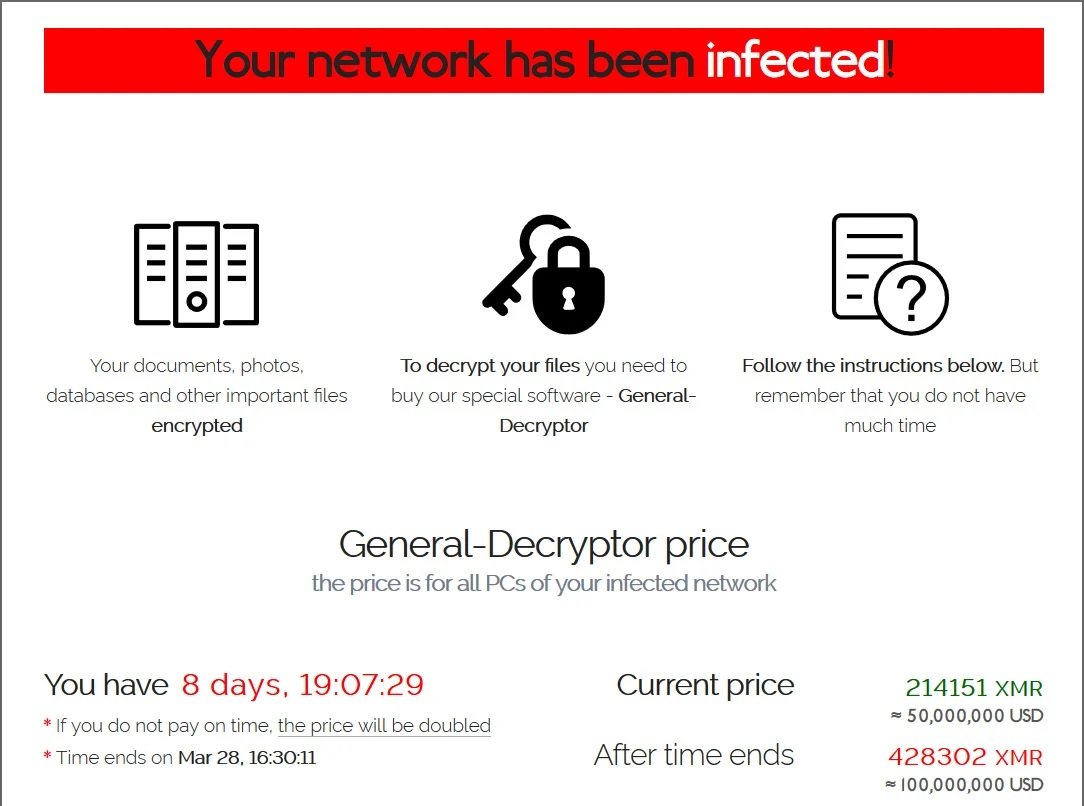
Sources close to the company mention that negotiations between hackers and Acer would have begun on March 14, although from the outset negotiators were surprised by demand for $50 million. Attackers would also have offered a 20% discount if the payment was made before last Wednesday, something that doesn’t seem to have happened.
Finally, researcher Vitali Kremez mentioned that the Advanced Intel cybersecurity and intelligence platform detected that a REvil operating group has recently been deploying multiple attacks against some Microsoft Exchange servers: “Some REvil-affiliated groups have been exploiting these flaws to infect Microsoft deployments.”
A couple of days ago it was confirmed that threat actors operating the DearCry ransomware used the ProxyLogon flaw to infect the affected systems. If REvil operators exploited recent Microsoft Exchange vulnerabilities to steal data or encrypt devices, it would be the first time that one of the ransomware operations used this attack vector.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











