Cybersecurity specialists report that multiple phishing websites are using JavaScript to prevent detection, checking whether users are browsing from a virtual machine or a secure environment, also known as headless service devices. These devices and services allow cybersecurity firms and researchers to determine whether a website is used for fraudulent purposes.
On the other hand, threat actors use JavaScript phishing kits to verify whether a browser is running on a virtual machine; in case of detecting signs of secure environment usage, the website ends up displaying a blank page instead of the complete phishing website.
MalwareHunterTeam experts mention that hackers use a script to verify the user’s screen definition, as well as using the WebGL API to query the rendering engine present in the browser.
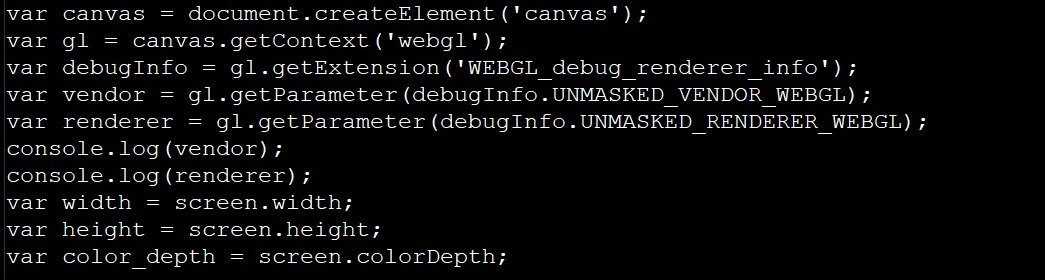
When performing checks, the script will check whether the browser uses a software renderer and checks whether the user’s screen has a color depth of less than 24 bits or if the height and screen width are less than 100 pixels. For this, threat actors rely on identifying software such as SwiftShader, LLVMpipe or VirtualBox.
In case of detecting any of these conditions, the operators of the phishing website will display a message in the browser developer’s console, showing the user an empty website. If normal conditions are detected, the hackers’ script will authorize displaying the phishing website to the users.
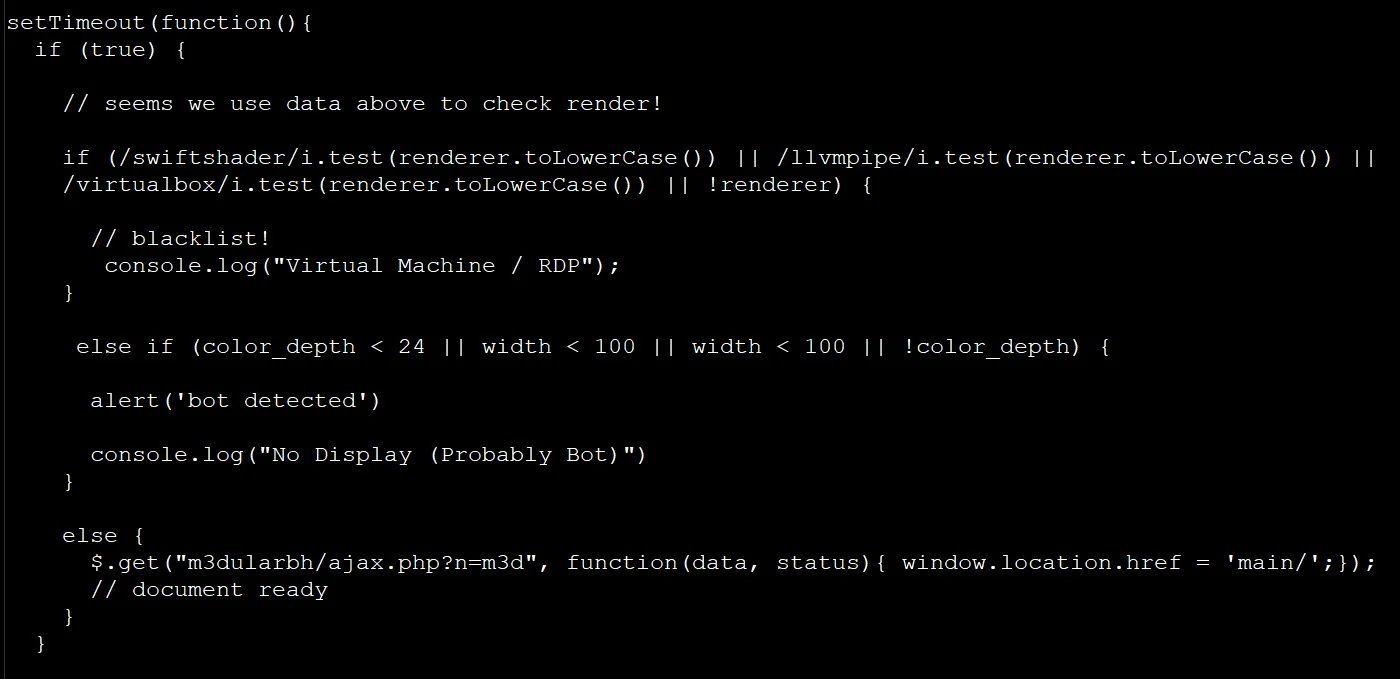
The code used by these hackers appears to originate from a 2019 article that describes how to use JavaScript to detect virtual machines in some environments.
On the other hand, security firm CEO Emsisoft Fabian Wosar mentions that his security teams use a variety of methods to search for and detect phishing sites, including signature matching and visual machine through machine learning: “These tools are very functional, although it can be relatively easy to bypass these mechanisms by simply connecting a couple of JavaScript APIs and delivering false information” Wosar mentions.
Developers and security firms consider this an opportune time to start updating the security mechanisms used in these environments and prevent phishing website operators from completing these attacks. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











