Ticketcounter, an e-ticket platform based in the Netherlands, has been affected by the leaking of a database that stored nearly 2 million email addresses due to the compromise of an insecure server. This company is dedicated to the sale of electronic tickets to enter amusement parks, zoos, museums and events in general.
A week ago, a group of threat actors created a hacking forum post with the aim of selling the stolen database, although the post was removed as soon as possible. At first the cybersecurity community attributed this decision to the work of the local police; however, a hacker contacted by an investigator revealed that the publication was removed to sell the database privately, adding that they are not afraid of the police.
The informant also mentioned that the compromised database consists of information such as full names, email addresses, phone numbers, IP addresses, and hashed passwords.
Moreover Troy Hunt, in charge of the Have I Been Pwned platform, confirmed Ticketcounter’s data breach, revealing that the company’s operators contacted him directly to report the incident. According to Sjoerd Bakker, CEO of the company, it all started when Ticketcounter copied a database to an Azure server to demonstrate how its users’ actual information was hidden using fake data; the copied database was not properly protected, resulting in its exposure, thus turning a security measure into a serious disadvantage.
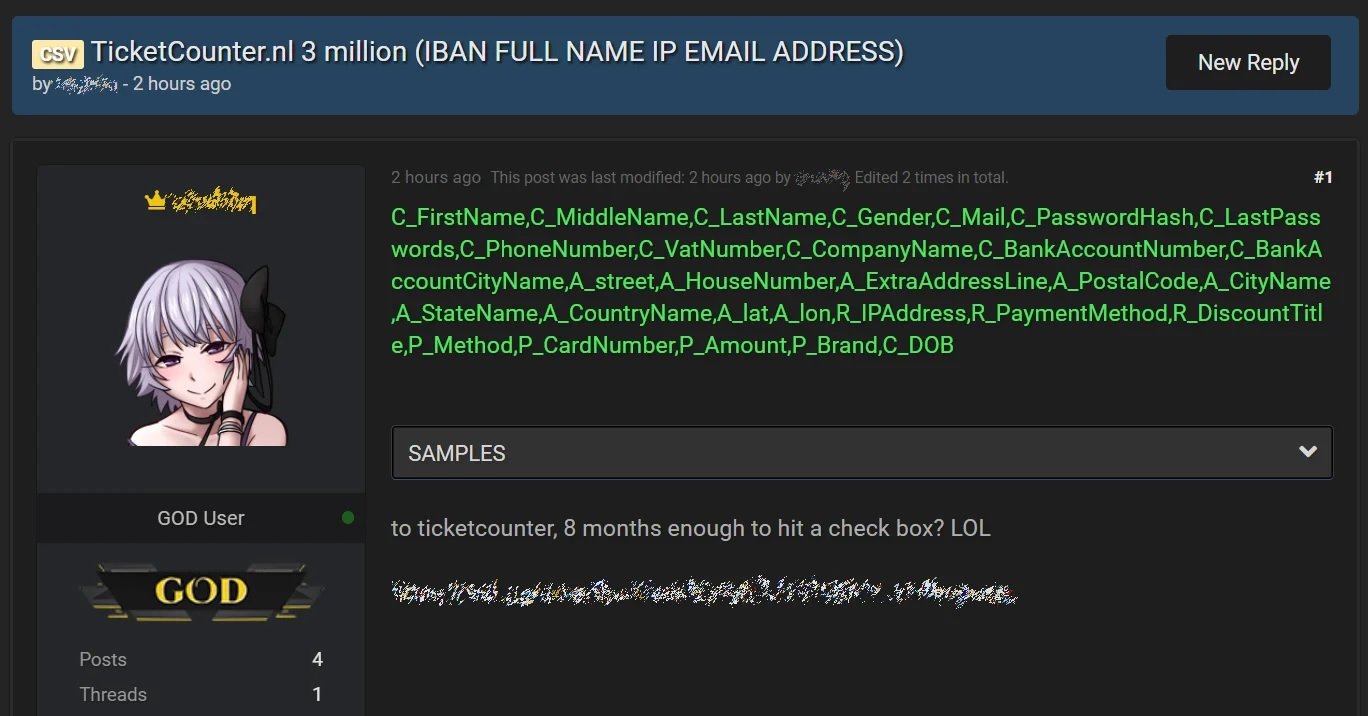
The database would have already been sold by threat actors, who also contacted Ticketcounter to demand about $340,000 USD in Bitcoin in exchange for not leaking this information. After not receiving a payment, the malicious hackers decided to publish the database for free on an illegal forum hosted on dark web.
At this point the company had already notified affected users about the incident, as well as recommending that partner establishments conduct their own notification processes to users. As part of its incident response process, the company is implementing some resources such as search widgets, FAQ website, and email templates.
For security, affected users are advised to reset their passwords to access compromised accounts, preventing dictionary or credential fill attacks. If the company delays responding to your concerns, experts recommend turning to Have I Been Pwned operators for greater knowledge of the incident and potentially compromised information.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











