A security firm reports the detection of a malicious campaign allegedly deployed by the Chinese hacking group identified as APT41 and targeting critical infrastructure in India, including power plants, power distribution centers and some domestic ports. The research was prepared by Recorded Future experts.
After multiple border clashes initiated in May 2020, political tensions between China and India have increased considerably, which has undoubtedly contributed to this cyberwarfare potential scenario. Experts claim that hackers, identified as “RedEcho”, maintain constant communication with ATP41, also known as Barium.
According to Recorded Future, at least 3 IP addresses in India were previously affected by APT42 in late 2020, impacting operations in the oil and gas extraction sectors on Indian territories.
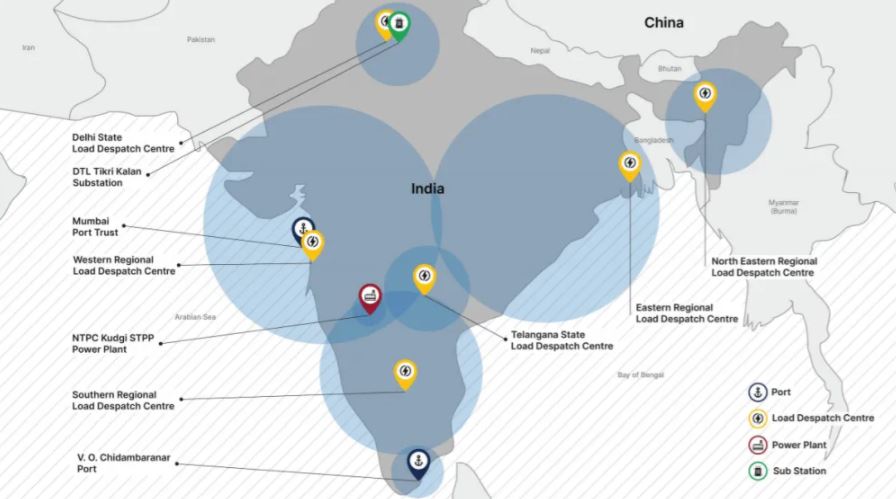
“We have observed a large increase in suspected intrusion activity against Indian organizations targeted by Chinese state-sponsored hacking groups.Through a combination of critical infrastructure scanning, domain analysis, and network traffic, we found that a subset of compromised servers in India share some similarities to security incidents previously detected and linked to Chinese government-sponsored hacking groups like APT41,” the report mentioned.
While this information suggests that the attacks were perpetrated by the same threat actor, Recorded Future experts mention that these are two different hacking groups. Experts collected evidence of multiple attacks on at least 10 power sector computer networks in India, including 4 distribution centers responsible for coverage in important territories.
In total, researchers detected 21 IP addresses associated with India’s energy infrastructure, concluding that these incidents are associated with the same hacking campaign.
Recorded Future also mentions that targeting these critical energy assets offers opportunities for economic espionage, as well as raising significant concerns about the potential prior positioning of network access to support other Chinese strategic objectives. Experts conclude their report by mentioning that, despite similarities to attacks related to APT41, the investigation has sufficient evidence to attribute this activity to the Hacking Group RedEcho, which is already considered a team specializing in critical infrastructure engagement.
What are your thoughts about this incident? Could it lead to a massive cyber warfare campaign in Asia? Are you willing to learn more about it? To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security Institute (IICS).

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











