
An article on The Telegraph dubs cybercrime as “the fastest growing crime in the world,” even labeling it as “an industry” given the impact it has on economies and the needs it creates for security firms and professionals to respond to. Cybercriminals are persistent, and they know how to evolve their attacks to defeat existing defenses.
Logically, security teams need to level up. It is not enough to simply have a security posture; an organization’s cyber defense has to be truly effective. It needs to be optimized and tested.
Operating a security operations center (SOC) is not some compliance requirement that suffices after passing a certain threshold. Even if it is developed and run by impressively credentialed security professionals, it will always require evaluation, tweaks, and improvements to ascertain its effectiveness.
So how should SOCs be optimized? Discussed below are four fundamental points that should always be covered in any optimization effort.
Training
Security validation platform Cymulate has an interesting analogy in emphasizing the importance of testing security controls repeatedly as a way of optimizing a security operations center. The company likens it to NBA star Lebron James’ training to achieve the kind of performance expected from an MVP.
James sure has the genes of a spectacular cager, but it’s unlikely for him to be one of the greatest players without training. Similarly, an SOC can have the latest cyber defense technologies in it and operated by a highly proficient and experienced security team, but it would be a stretch to expect it to deliver faultless protection without optimization.
SOC optimization requires training in terms of the technology used, the processes, and the people who are running the system.
Training is done to get the system accustomed to the stresses that will be encountered during an actual attack. Instead of waiting for an attack to find out if the security controls are indeed effective, simulations can be undertaken to determine weaknesses and implement improvements.
One of the most effective ways to train an SOC is the so-called breach and attack simulation (BAS), which is referred to as Continuous Security Validation at Cymulate. With this form of “training,” an organization subjects its defenses to various kinds of attacks to check if they are working as intended and reconfigure or replace them if the results show otherwise.
Just like systematic athlete training, Cymulate shows statistics useful in evaluating the performance of existing security controls. It quantifies the simulation outcomes to guide security teams on what needs to be done, and which specific concerns should be addressed first.
Threat intelligence
Security systems rely on information about cyber threats and attacks to prevent attacks or gain the ability to remediate an attack penetration. Without updated and reliable threat information, SOCs will have a hard time identifying threats and preventing them from compromising a network or device.
However, it is not enough to simply have an accumulation of threat details. The raw information collected should be centralized or unified for better visibility and analysis. Threat information does not equate to threat intelligence.
Cymulate’s Immediate Threats Intelligence feature allows security teams to have a full view of the state of security of their organization, from the email to the web gateway and endpoints. It does not only rely on a database of recent threat information. It performs simulations to evaluate the effectiveness of existing defenses and generate an easy-to-understand report that includes recommendations for prevention and mitigation.
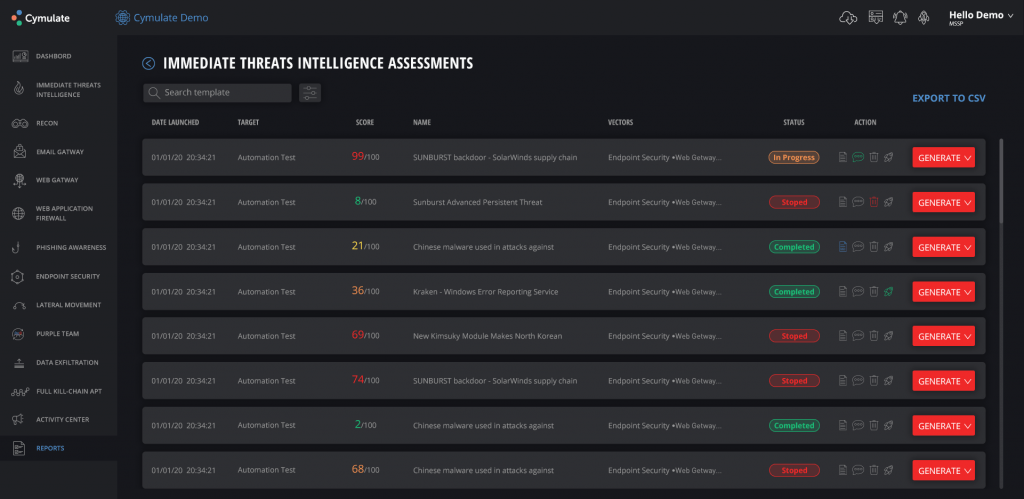
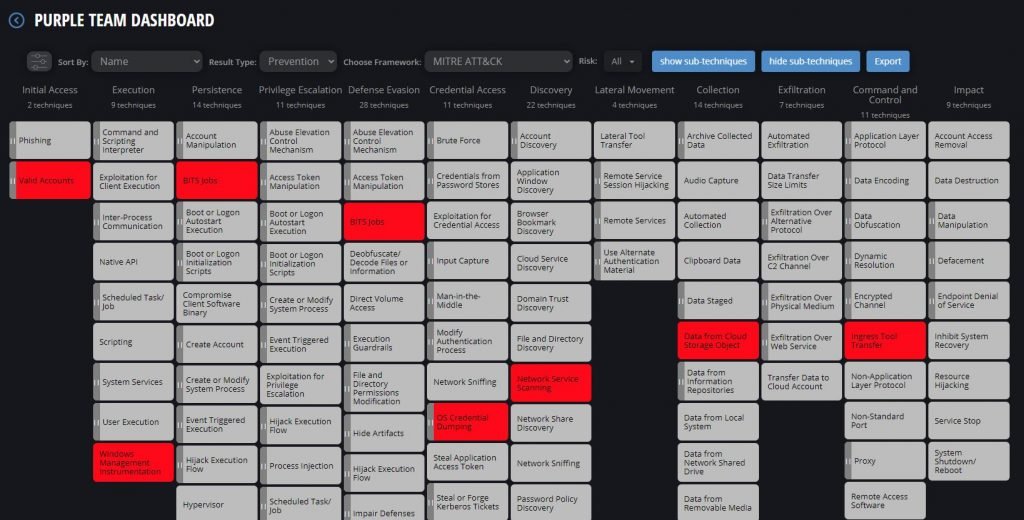
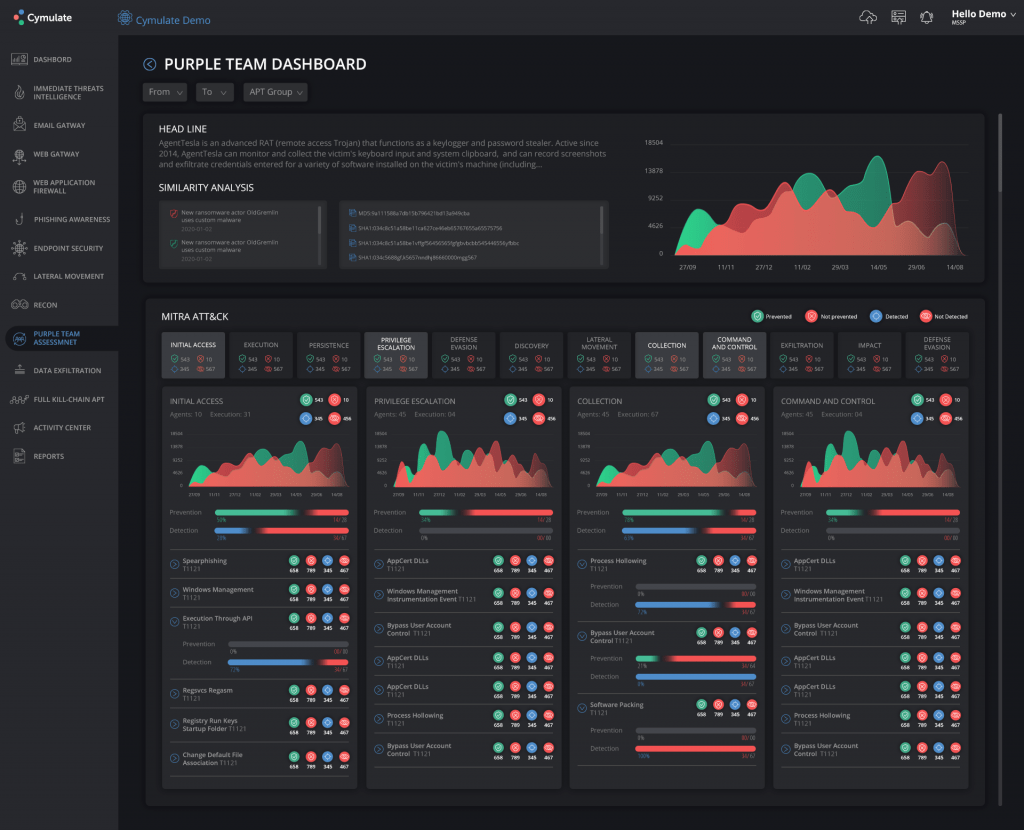
Aside from its proprietary immediate threat intelligence system, Cymulate also takes advantage of the MITRE ATT&CK framework to bolster its threat detection and response capabilities. The framework helps enable the development of custom cyber attack simulation templates. It presents over a dozen attack tactics and more than a hundred techniques that serve as a comprehensive guide for evaluating security postures continuously
Through ATT&CK, Cymulate was able to detect a new variant of the Dharma ransomware, which is known to be installed to systems by tricking device users with an offer to uninstall the ESET antivirus from their systems.
Centralization, integration, and automation (CIA)
SOCs consist of more than a few security solutions. As such, it is a must to unify and centralize all of the cyber defense software or services employed by an organization. Failing to do so can result in hidden inefficiencies and the high likelihood of getting overwhelmed by too many security notifications or alerts and missing important information critical to the integrity of the entire security posture.
Additionally, centralization and integration are vital in minimizing errors that are often encountered in manual methods of data collection and analysis. Many Tier 1 SOC analysts still rely on the mostly error-prone manual processes for threat information collection and scrutiny. This undermines optimization efforts that generally try to reduce human involvement in processes and favor automation.
With the cybersecurity technologies available at present, centralization, integration, and even automation can be achieved relatively easily. Cymulate, for instance, enables quick integrations with third-party security products including RSA Archer, Tenable IO, Splunk, Microsoft Defender ATP, IBM QRadar SIEM, and SentinelOne.
Cymulate’s integration of different security solutions enables advanced security orchestration and automation. Integrating Palo Alto Cortex XSOAR, for example, makes it possible to automatically launch an immediate simulation regarding the most recently detected threats, pick up the indicator of compromise (IOC), send the IOC for blacklisting at the relevant security controls, then repeat the process until all IOCs are stopped.
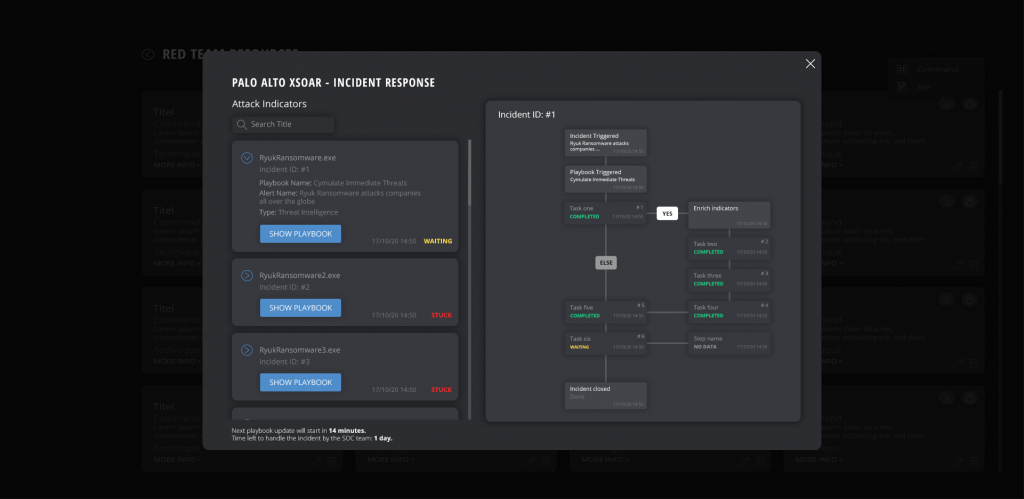
Incident response
Lastly, a security operations center must have an agilely effective incident response capability. The ultimate goal of training or stress-testing an SOC, ensuring comprehensively reliable threat intelligence, and CIA (centralization, integration and automation) is to make sure that the system has the right response to a security event.
An SOC should have a well-established protocol or plan to address a security breach or multiple attacks. It is important to plan everything ahead. The actions to be taken in case a particular cyber attack penetrates or a security control is compromised should be laid out clearly.
All plans should be carefully formulated and tested to avoid bottlenecks and confusion especially when an SOC is dealing with multiple breaches. Additionally, security teams should be mindful of restrictions such as the requirement of GDPR and NY Cybersecurity to follow a 72-hour data breach notification timeline. Compliance requirements can easily mess up response plans.
An excellent incident response capability affirms the optimization of an SOC. An optimized security operations center with full security visibility, dependable threat intelligence, and seamlessly integrated security solutions, is almost always effective and quick when it comes to incident response.
In summary
No matter how well-designed and advanced an SOC is, it cannot be excused from testing and optimization. There is no guarantee that the security measures and tools put in place will work as they are intended. Cyber attackers will always find a way to compromise defenses. Organizations need to consistently train or test their systems, adopt a reliable threat intelligence approach, and centralize and integrate all security controls.

Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.











