Recent reports indicate that the joint work of the French and Ukrainian authorities led to the arrest of multiple individuals accused of belonging to the Egregor ransomware group. Operators of this variant of ransomware, based in Ukraine, were arrested after French police invested significant resources for identification and location.
These people are accused of deploying hacking attacks against multiple organizations in order to infect their systems with the ransomware in question. The French authorities also mentioned that other members collaborated in logistics and financing activities.
About this malware, cybersecurity experts mention that this was one of the most active ransomware variants during 2020, attacking all kinds of organizations like Ubisoft, Ouest France, Gefko, among others. The investigation began last fall, when the Paris Court began receiving a large number of reports of ransomware attacks.
Egregor operates as a ransomware as a service (RaaS) platform, meaning that developers work with various clients who deploy the infection, dividing profits between the two parties. This has proven to be a highly profitable method, as it allows malware developers to devote themselves entirely to its maintenance and development.
Cybersecurity experts mention that, on average, developers can earn up to 30% of the ransom amount, while attack perpetrators keep most of the profits. Egregor ransomware would have been first identified in September 2020, just a couple of weeks after the close of operations of the Maze ransomware, one of the most popular variants.
These experts also mentioned that Maze developers began collaborating with Egregor to create a RaaS platform with advanced capabilities. Last November, operators partnered with the Qbot malware platform, allowing them to access victims’ networks, growing rapidly among the cybercrime community. However, in late 2020 researchers began to detect a decrease in Egregor-linked ransomware incidents, as well as a decrease in accumulated assets in attackers’ cryptocurrency addresses.
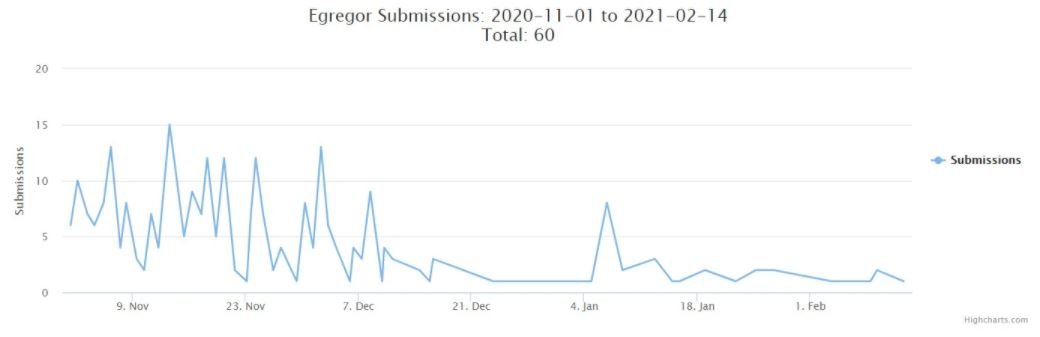
Investigators do not yet conclude whether this trend is due to the work of law enforcement agencies or whether it is a strategic movement by Egregor’s developers, although this multiple arrest could be a fatal blow to this platform. It should be noted that, at their highest point of activity, Egregor’s developers accumulated more than 200 victims, committing all kinds of public and private organizations around the world.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











