The operators of the Ziggy ransomware variant have announced the shutdown of their infrastructure and the publication of decryption keys for all versions of the malware, meaning that victims of this cybercriminal group will be able to regain access to their information without having to make any payment to the hackers. According to cybersecurity expert M. Sjahpasandi, the announcement was made through the hackers’ Telegram channel.
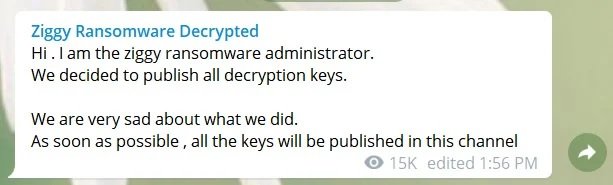
In this communication channel Ziggy’s main administrator mentioned that they created the malware as a way to generate revenue in a third-world country that was not named. On their decision, the alleged hacker mentions that, in addition to beginning to feel guilty about these actions, they thought about the actions taken by law enforcement agencies against other ransomware groups and concluded that it was best for them to stop operating the malware.
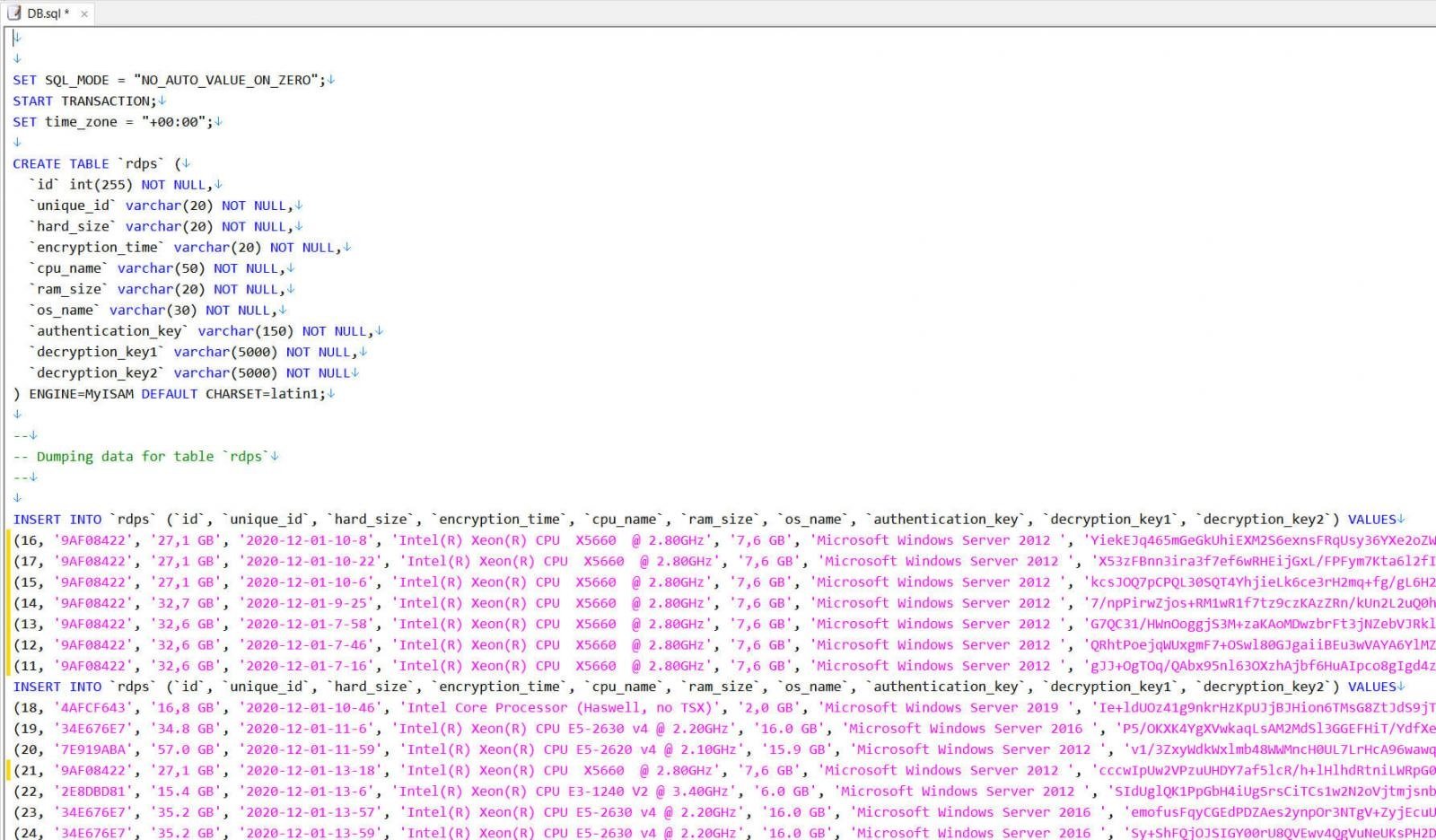
As mentioned above, the malware operator published a SQL file, with almost a thousand decryption keys corresponding to each victim of this attack. Each infected system requires three keys, so it is estimated that there are between 300 and 350 victims of the Ziggy ransomware.
Malware operators also released a decryption tool to fully regain access to affected systems. The tool is available in VirusTotal.
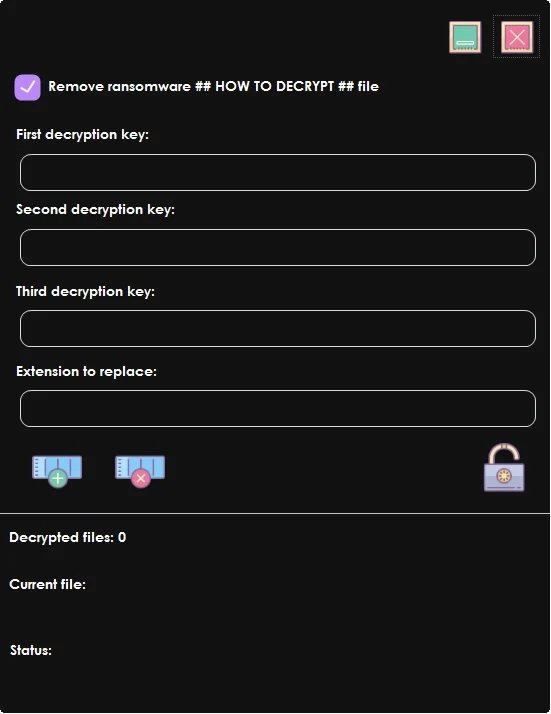
Additionally, the operator also announced the publication of the source code of a second decryption tool containing additional keys, also known as “offline” keys. Offline keys are used to decrypt ransomware-infected systems that do not have an internet connection or cannot connect to the hackers’ C&C server correctly.
Finally, Ziggy administrators shared some of their files with Michael Gillespie, a renowned ransomware researcher, who in turn created a decryption tool using the keys published by the hackers.
Although the intentions of the creator of this ransomware appear to be legitimate, cybersecurity experts recommend that victims use the decryption tools created by security firms: “The release of this information is great news for victims as they will be able to retrieve their information without paying a ransom or employing the decryption tools of the hackers, which might contain additional malware or even a backdoor,” Gillespie says.
This is not the only hacking group that has made a similar decision. A few days ago the operators of the Fonix ransomware also decided to close their trades and publish the decryption keys; it is mentioned that Emotet, an allied ransomware group, will make the same decision soon. Experts believe this is due to actions taken against operators of other variants such as Emotet and Netwalker.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











