Security agencies and hacking groups around the world use the most sophisticated network security and pentesting tools to detect vulnerabilities in a target network to perform further analyses. Experts from the International Institute of Cyber Security (IICS) mention that detection of security flaws is one of the main objectives of both cybercriminals and research agencies.
This time we will show you a list of the most popular tools employed by all kinds of black & white hat researchers and hackers. Please note that this material is made for entirely educational purposes, so IICS is not responsible for the use given to these tools.
SCANNERS FOR HACKING, PENTESTING, AMONG OTHER ACTIVITIES
This is a multi-service tool framework that provides pentesting experts with comprehensive and powerful solutions for deploying vulnerability management and analysis processes.
This tool allows malicious hackers and researchers to develop and execute exploit code against any system remotely. Other important subprojects include the Opcode database, the shellcode file, and related research.
The favorite tool of the pentesting community. Kali Linux is a Debian-based distribution designed for digital forensic analysis and pentesting processes. This distro includes numerous pentesting programs such as nmap, WireShark, John the Reaper, among others.
Pig:
This is a Linux package processing tool ideal as an add-on during the pentesting process.
This is an interactive Python-based batch manipulation program and library.
Its developers mention that this is an open source tool for automating exploit search in major databases. Pompem was developed in Python and has an advanced search engine, which makes the pentesting process easier.
Nmap:
Network Mapping (Nmap) is one of the most popular utilities for security audits and open source network exploration today. The tool is available for free via GitHub.
NETWORK MONITORING AND DATA COLLECTION IN PUBLIC SOURCES TOOLS
Justniffer is a network protocol analyzer for traffic capture and individual logging creation. By using this tool pentesting experts can emulate Apache web server log files, track response times and extract all “intercepted” files from HTTP traffic.
This is a specialized packet tracker for displaying and logging HTTP traffic. It can run in real time, showing traffic as it is analyzed, or as a daemon process that logs on to an output file. Experts mention that HTTPRY is written to be as light and flexible as possible, so it can be easily adapted to any hacking tool.
This tool provides most of the common GNU grep features, applying them at the network level. Pentesting experts mention that Ngrep supports pcap, allowing you to specify extended regular or hexadecimal expressions to match the payloads of the package data.
The tool supports IPv4/6, TCP, UDP, ICMPv4/6, IGMP, and Raw over Ethernet, and understands BFP filter logic in the same way as other popular tools like tcpdump and snoop.
PassiveDNS is a tool to collect DNS records to assist in incident management, network security monitoring, and digital forensics analysis. This tool allows pentesting specialists to examine the traffic of an interface or read a pcap file to write responses from the DNS server, as well as cache and merge duplicate DNS responses into memory.
This is a tool that uses a Snort-like engine and rules for analyzing logs (syslog/event log/snmptrap/netflow/etc).
This tool works much like Snyk, although the main difference lies in usage costs.

This is a traffic explorer that shows the use of networks in a similar way to what the popular UNIX command does, as mentioned by pentesting experts.
This tool scans and tracks the kernel of affected Windows systems and is able to capture most of the Windows kernel activity, including creating and terminating processes and threads, file system inputs and outputs, logging, network activity, loading and downloading DLLs, and more.
PROTECTION AND ANTI-INTRUDER SYSTEMS
This is an open source Network Intrusion Prevention System (NIPS) created by Martin Roesch in 1998. Pentesting experts mention that this tool is considered one of the most important open source projects ever developed.
Bro:
This is a powerful network analysis framework that represents a great alternative to using the most popular IDS.

Although the operation of this tool is a little hard to explain, its features are highly advanced. According to pentesting experts, OSSEC performs log analysis, integrated file verification, rootkit detection, and provide real-time alerts.

OSSEC works on most operating systems, including Linux, macOS, Solaris, HP-UX, AIX, and Windows.
This is a high-performance network security tool, IPS, and network IDS. This is an open source tool and belongs to a nonprofit community foundation called the Open Information Security Foundation (OISF).
This is a Linux distribution specially developed for intrusion detection and general task monitoring. Based on Ubuntu, Security Onion has tools such as Snort, Suricada, Bro, OSSEC, Snorby, ELSA, NetworkMiner, among other security tools.
This is a tool written in Python that works similarly to DenyHosts capable of collecting information about threat actors on a target network.
Pentesting experts can use this tool to verify the integrity of the scanned files. The driver starts from the computer, making it difficult for attackers to understand how the system works.
This is a next-generation Python, Ruby, Java, and Lua packet tracking engine with machine learning capabilities, Network Intrusion Detection System (NIDS) functionalities, DNS domain classification, network collector, network forensic analysis, and many other features.
DenyHosts is a tool for protecting any system against brute force attacks, dictionary attacks, among other hacking methods.

System administrators can scan log files and take appropriate action against any potentially malicious IP address.
This is a C-written security software widely used by cybersecurity experts worldwide.
Lynis is an open source security inspection and monitoring tool for Linux and UNIX systems.
HONEYPOTS, INTELLIGENCE TOOLS AND MORE
This is a mid-to-low interaction honeypot tool designed for easy deployment, extending its functionality with custom plug-ins and configurations.
This is an interactive server honeypot designed for easy deployment. By providing a set of generic control protocols, pentesting experts will be able to create the foundation for building their own security system to catch the most advanced hackers.
Amun:
Amun is a low-interaction Python-based Honeypot.
Glastopf is a tool that emulates the exploitation of thousands of vulnerabilities to collect data on attacks against multiple web applications.
This is a mid-level SSH honeypot designed to detect and contain brute force attacks, as well as analyzing all shell communications deployed by threat actors.
Kojoney is a low-interaction honeypot that emulates an SSH server. According to pentesting experts, the daemon is written in Python using Twisted Conch libraries.
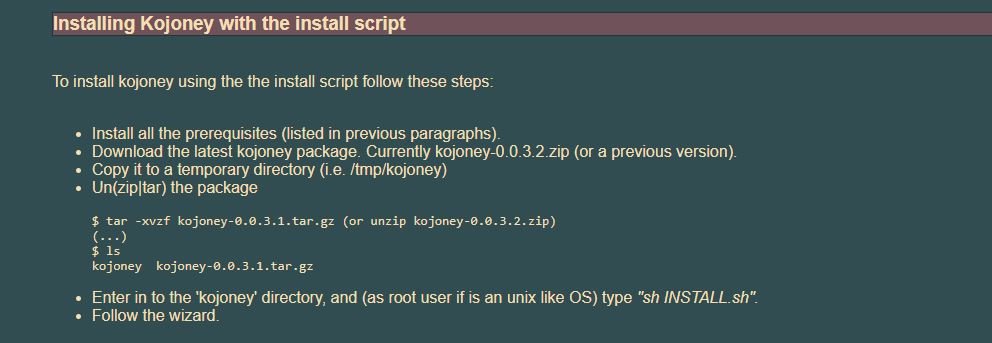
This is a high interaction honeypot really popular among developers and malicious hackers.
This is a DHCP server NAT device deployed with a network adapter directly connected to the Internet. Unlike other NAT devices, Bifrozt stands out for its ability to act as a transparent SSHv2 proxy between an attacker and its honeypot.
This is the main Linux distribution for honeypots. HoneyDrive is a virtual device with Xubuntu Desktop 12.04.4 LTS installed. The tool contains more than 10 pre-installed and preconfigured honeypots such as Kippo SSH, Glastopf and Wordpot.
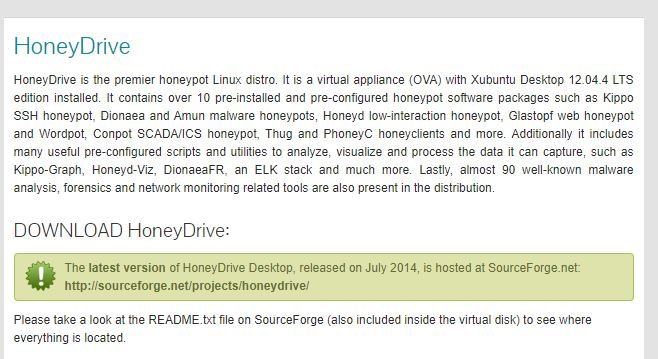
This open source software is employed for automating the analysis of suspicious files using custom components.
NETWORK PACKAGES CAPTURE
This is a program for capturing data sent as part of TCP connections and that stores the data convincingly for TCP protocol analysis and debugging.
This is a tool for extracting data about web traffic from a target system. Xplico is not a network protocol analyzer, but is an open source forensic analysis tool.
Moloch is an open source tool for capturing IPv4 packets with indexing systems and database. By using this tool pentesting experts can have a very easy-to-use interface to view, search and export the captured packages. The tool is designed for compatibility with multiple systems.
This is a set of tools that provide a lightweight full-band network traffic logger and a buffering system. The tool was designed to allow users to deploy a distributed network traffic logger on COTS hardware while integrating into existing alert and log management tools.
This is a forensic analysis network that allows pentesting experts to develop plug-ins to support network packet capture splitting in a really practical way.
This tool is designed for packet capture that provides quick and easy access to various subsets of these packages.
The second part will be published soon. For more information on vulnerabilities, exploits, malware variants, cybersecurity risks and information security courses, feel free to access the International Cyber Security Institute (IICS) website.

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.










