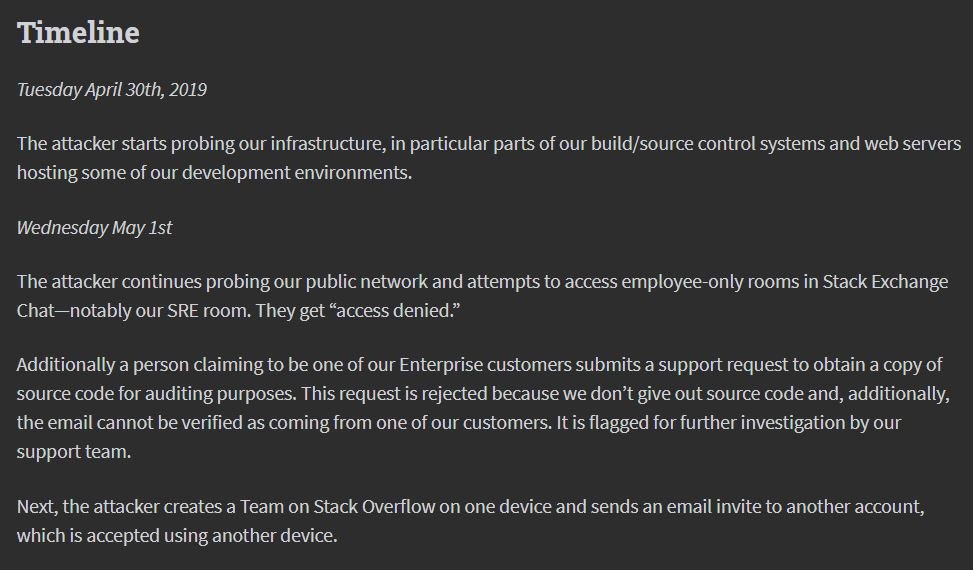
This week Stack Overflow developers released a security report related to the incident that compromised their systems in 2019. According to this report, the threat actor pretended to be one more user of the long-term Q&A platform in order to learn how to perform various hacking tasks on compromised systems.
The platform revealed the security breach in May 2019, later mentioning that this attack resulted in the leaking of some users’ personal information. In an exercise in transparency and accountability, Stack Overflow decided to publish a detailed timeline of each stage of the attack, which they believe would have begun in April 2019 and was detected until May 12, when administrators detected that a user increased their privileges without apparent explanation.
Threat actors reportedly managed to access the personal information of up to 184 users, including details such as full names, email addresses and IP addresses. Administrators believe that theft of personal information was not the attacker’s primary target, as stack overflow source code theft was also demonstrated.
As mentioned above, the attacker would have started using the platform with a non privileged elevated account, waiting patiently until they obtained the privileges necessary to access the platform’s source code.
The report emphasizes that the threat actor failed to access the platform’s public or private databases: “We also want to add that there is no evidence of direct access to our internal networks, so the perpetrator did not have access to data in products such as Teams, Talent or Enterprise,” the platform admins mentioned.
With no doubt, the most striking thing about this incident is the behavior of the hacker, who was frequently active on the forum in order to obtain information to carry out an effective attack: “In a certain way, the guidance the attacker obtained from other Stack Overflow users helped them to complete their goal,” the report says.
The investigation is still ongoing, so platform administrators are not in a position to share additional information about the attacker, merely mentioning that they’re talking about a certainly patient, skillful and determined individual. The report also includes information on the measures taken to manage the incident, in addition to the collaboration programs stacked by Stack Overflow with other platforms since then.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










