Over 1.4 million personal records of Pixlr users were exposed by a hacker through a forum on dark web; as you may remember, Pixlr a free online image editing app popular among thousands of marketing employees. Cybersecurity experts fear that this data may be used against affected users in phishing campaigns or credential stuffing attacks.
A few days ago, the hacker known as ShinyHunters published the database on a cybercrime forum, mentioning that the information was extracted from the platform during a cyberattack targeting 123rf, a stock image platform. Both websites belong to the parent company Inmagine. The information is available for free.
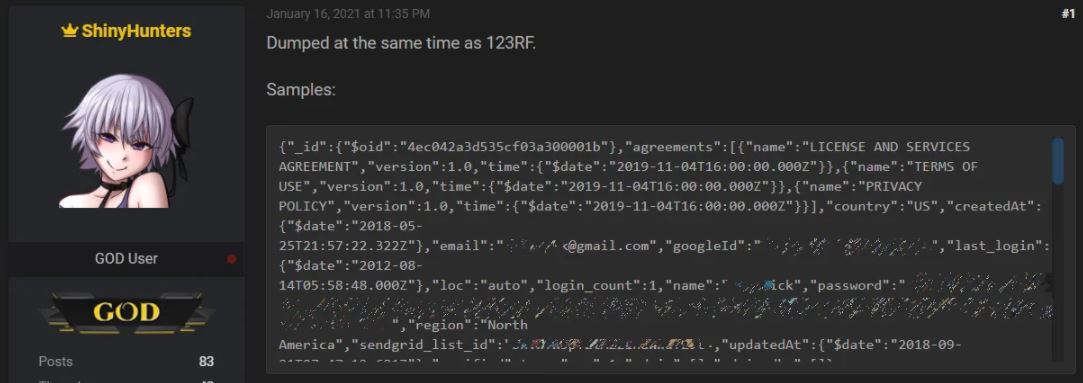
Cybersecurity experts mention that ShinyHunters is a well-known cybercriminal involved in constant attacks on multiple websites, extracting information to sell it on hacking platforms. This hacker has been linked to security incidents on platforms such as Tokopedia, Homechef, Chatbooks, Wattpad, among others.
The Pixlr leak consists of 1 million 435, 235 user records including login names, email addresses, hashed passwords, and more. The database would have been extracted from a bucket in Amazon Web Services (AWS) by late December 2020.
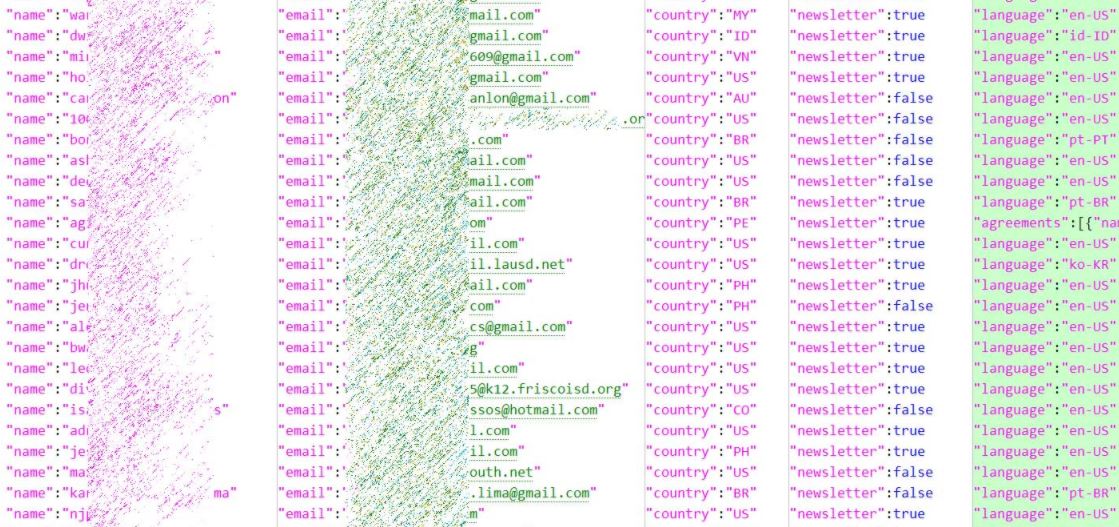
Although the company has not spoken out on the incident, various members of the cybersecurity community confirmed that the email addresses exposed are authentic, indicating that the leak is legitimate.
While Pixlr announces the steps that will be taken to address this incident, it is recommended that all users of the platform reset their passwords to avoid illegitimate access, in addition to ignoring any recently received suspicious emails. To prevent credential stuffing attacks, experts recommend users not to employ the same passwords on other online platforms.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











