According to a recent report by cybersecurity experts, the operators of a botnet have been targeting non-patched applications running on Linux systems. The botnet, identified as FreakOut, was first identified in November 2020 and has shown a new uptick in attacks over the past few weeks.
Among the main objectives of FreakOut operators are Terramaster storage units, which are web applications built on Zend PHP and sites running Liferay Portal. Experts mention that the botnet performs massive scans on the Internet to detect vulnerable applications and then exploit three vulnerabilities to gain control of the underlying Linux system.
Below is a list of the three flaws exploited in this attack by threat actors. It should be mentioned that they are newly discovered vulnerabilities, so specialists believe that each FreakOut attack has a considerable level of success:
- CVE-2020-28188: Remote Code Execution (RCE) on terraMaster admin panel
- CVE-2021-3007: Zend Framework deserialization error
- CVE-2020-7961: Deserialization error in Liferay Portal
When FreakOut operators gain access to a system, the next step is to download and run a Python script that connects devices to a remote IRC channel from which hackers can send commands to deploy all kinds of attacks.
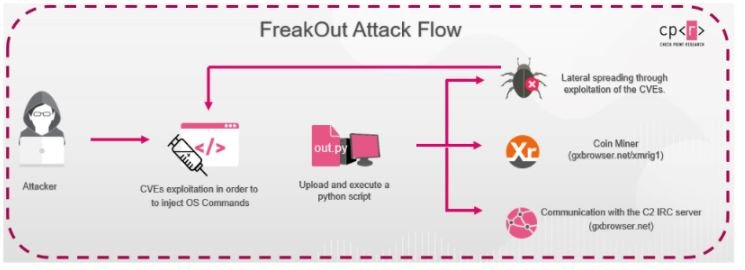
The report mentions that a successful compromise would allow the deployment of denial of service (DoS) attacks, installation of cryptojackers, and even infection of other devices connected to the same network. Although the precise magnitude of this botnet has not been determined, experts believe it is at an early stage of development, although its massive expansion may be beginning; it is even mentioned that with infected systems so far (between 180 and 300) enough and enough to launch DoS attacks.
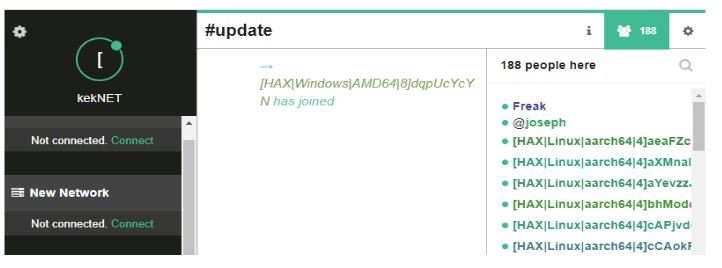
Eventually experts mentioned that evidence was detected that the malware code was developed by a malware creator identified as “Frank” among the cybercriminal community. Upon further investigation, it was concluded that this individual also developed malware from the defunct N3Cr0m0rPh botnet, targeting vulnerable Windows systems.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











