A British security specialist reported finding a critical vulnerability in Shazam, the popular music recognition app, which would allow threat actors to extract a user’s location data by sending a malicious URL. The flaw lies in the app for iOS and Android.
As you may remember, this application can identify the name of songs, movies and TV shows using a small audio sample captured by the microphone of the device thanks to the “deeplink” technology. The expert mentions that the flaw exists because an exported deeplink that loads websites into a Shazam-integrated browser does not validate its parameters correctly, which could trigger in the application’s engagement.
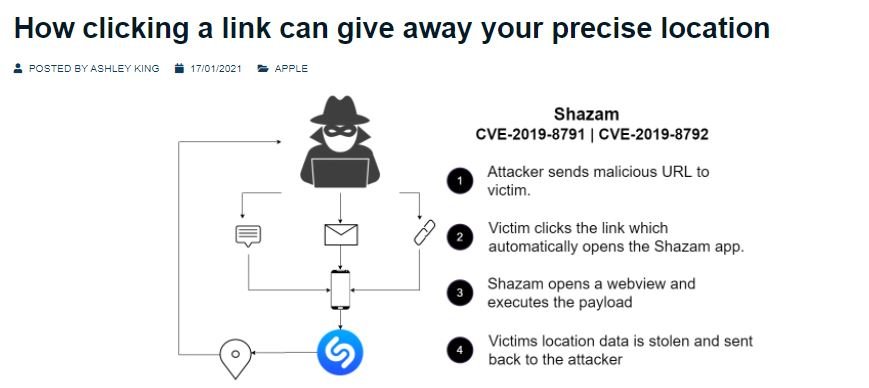
Malicious hackers could exploit the flaw by sending a malicious URL that will be opened by Shazam when the target user clicks on the received link. Shazam will then open WebView, its built-in browser, and run the payload, resulting in sending the device’s location data to an attacker-controlled server.
At the time of its patching, the flaw could have affected Shazam’s more than 100 million users. The vulnerability was fixed after Apple acquired the app, although it was mentioned that the company did not consider this report to meet the requirements set out in its bug bounty program, so the researcher was not compensated.
By taking his report to Google, the researcher received a similar response: “Google does not consider location data leaking as a serious security risk,” the expert said. However, the company mentioned through the Play Store that users could see their location data exposed if they did not use the latest version of Shazam.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











