Joker’s Stash operators have announced that the platform will be permanently shutdown in the middle of next month. This is one of the most popular and oldest illegal online markets on the dark web and for years remained the main option to buy stolen credit cards and even other data: “It’s time for us to leave forever. WE WILL NEVER OPEN AGAIN,” the message specifies with the intention of preventing customers from the possible occurrence of an imposter.
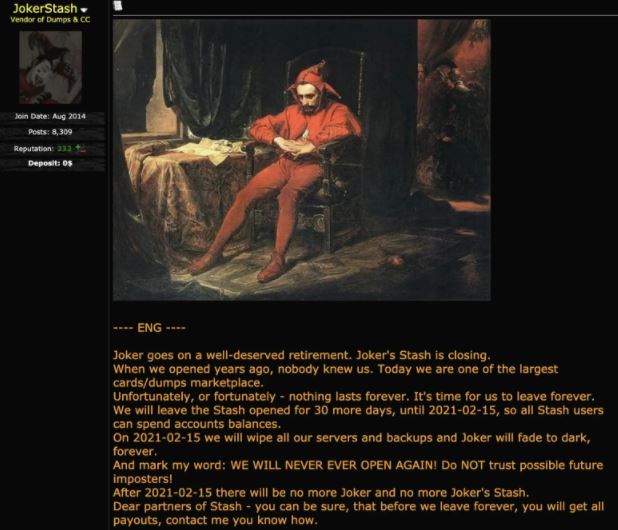
The announcement was posted on multiple illegal forums, noting that the scheduled closing date is February 15 and that all servers and backup programs will be permanently deleted.
This platform started its activities in 2014 and quickly became one of the markets most visited by the cybercriminal community. Despite the robustness of its operations, during 2020 law enforcement agencies managed to seize four blockchain domains used by this market, temporarily disrupting its operations; another drawback came when the main operator of the platform revealed that it was suffering from the aftermath of the coronavirus.
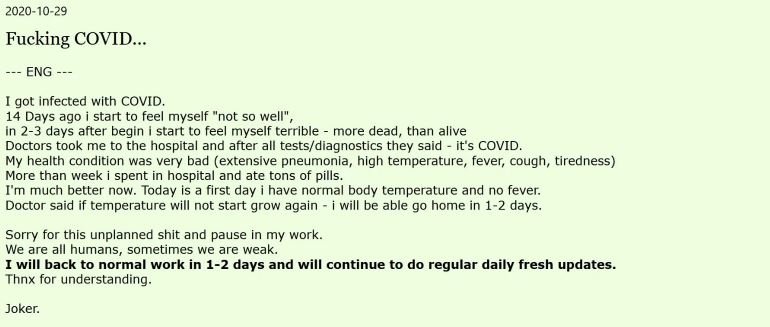
These factors contributed to a significant decrease in the credit cards available on the platform, also decreasing the number of transactions recorded each month on Joker’s Stash. In a report, cybersecurity firm Gemini Advisory mentioned that in 2020 the platform’s operators published more than 40 million new records, most derived from the point-of-sale commitment.
Experts estimate that the operators of this platform generated more than one billion dollars derived from the sale of stolen payment cards, using the use of various cryptocurrencies to complete transactions. It is believed that the main trader of the platform increased its profits considerably after the sudden increase in the value of Bitcoin, which could have influenced its decision.
Despite the researchers’ hypotheses, Joker’s Stash operator did not mention any reason for closure, concluding his message by noting that it would provide a 30-day period for all users of the platform to delete their information.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











