Cybersecurity specialists detailed the finding of a critical vulnerability in Windows 10 that, if exploited, would allow threat actors to compromise an NTFS-formatted hard drive using a simple command. According to the report sent to Microsoft, it is possible to hide the single-line command within a Windows shortcut, ZIP file, or common files to generate errors on the hard drive, damaging the file system immediately.
The researcher who detected the vulnerability mentions that the problem was introduced with the release of Windows 10 Build 1803, and remains present until the latest version. The failure is considered severe as even a user with few privileges on the target system could exploit it.
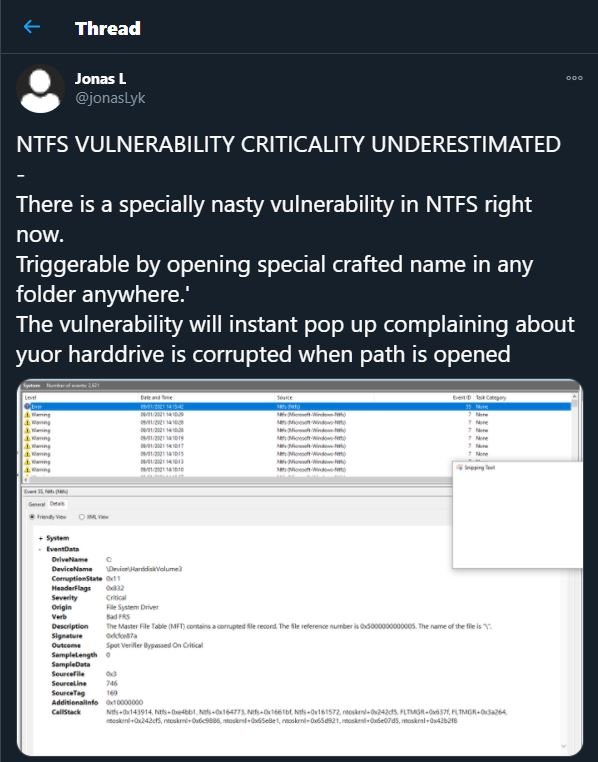
Apparently the hard drive can be corrupted even if you try to access the NTFS attribute “$i30” in the folder in a certain way. The Windows NTFS index attribute (string “$i30”) contains a list of files and subfolders in the directory, and in some cases, the NTFS index can also include deleted files and folders, which is useful in some security incident response processes or during forensic analysis.
The researcher was unable to explain why access to this attribute leads to damage to the storage unit, although he mentions that the registry key that would help diagnose the problem does not work.
After running the command on the Windows 10 command line and pressing Enter, the user will see the error message “File or directory is corrupted and cannot be read”. Windows 10 will start displaying notifications that will prompt the user to restart the computer and repair the damaged drive. When the device gets restarted, the Windows disk check utility will start repairing the hard disk.
Once the disks are corrupted, Windows 10 will fail the event log indicating that the main file table (MFT) on a particular disk contains a corrupted entry. Possible corrections will be revealed shortly.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











