Bitdefender’s cybersecurity specialists have released a free tool to remove the encryption provoked by the DarkSide ransomware, allowing victims to recover their blocked information without paying a ransom to attackers. This variant of encryption malware has been active for just a few months, although it already has thousands of victims worldwide.
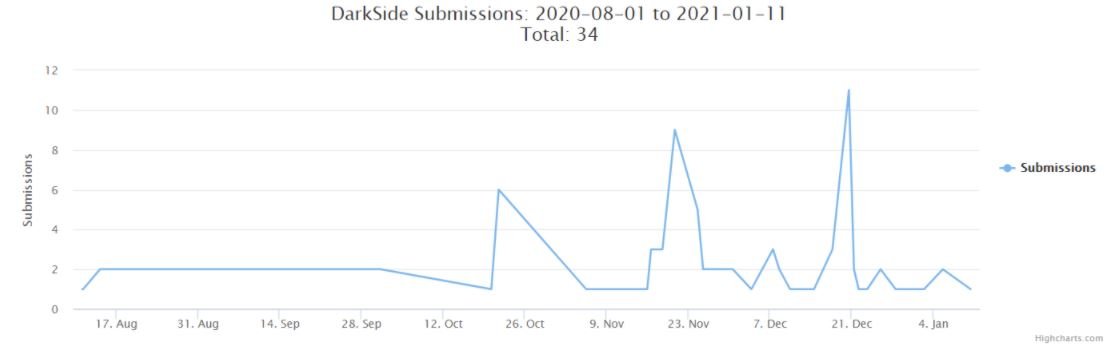
As can be seen in the graph below, this operation showed its highest activity point during the last quarter of 2020, when the number of DarkSide samples detected in ID-Ransomware increased the previous records more than 4 times.
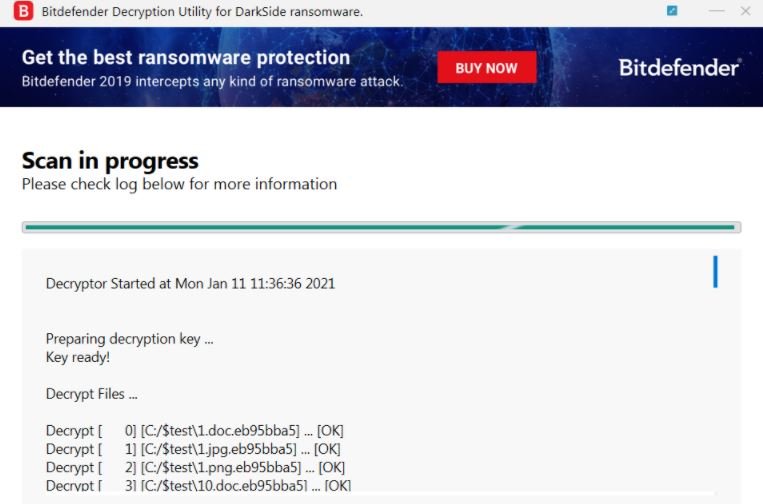
The tool is available for free on the official platforms of the developers. Using this tool you will be able to scan your entire system or search specific folders to unlock the files infected by DarkSide, as well as relying on the user to create a backup to protect their information from future incidents.
Experts note that DarkSide works under the Ransomware as a Service (RaaS) scheme and is maintained by former members of other hacking groups. After each successful attack, operators charge amounts that vary depending on the number of infected files or devices, the type of organization compromised, among other factors.
According to previous records about this hacking group, the ransom figures range from $200 billion to $2 million USD, depending on the victim.
Last November, DarkSide developers announced to their customers that they were building a distributed and sustainable storage system hosted in Iran and other unreleased locations. It should be remembered that Iran faces an economic blockade by the U.S., so these groups must look for a constant source of income to keep their operations active.
This free tool will allow thousands of users affected by this malware to reset their systems, although darkside developers are likely already working on launching new versions of the ransomware.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











