Ho.Mobile, the low-cost operator for telecomm giant Vodafone, has announced that a hacking group managed to compromise part of its customer database, which stored personal information, SIM details, among other data. This information has been posted on several hacking forums in dark web since December 2020 and cybersecurity experts estimate that it contains over 2.5 million registers.
Infosec researcher Bank Security first reported the leaking and selling of the database last December 28. In response, the company issued a statement mentioning that they were not aware of such situation. Nonetheless, everything changed last Monday, when ho.Mobile confirmed the massive data breach, pointing out that some sensitive details could have been stolen.
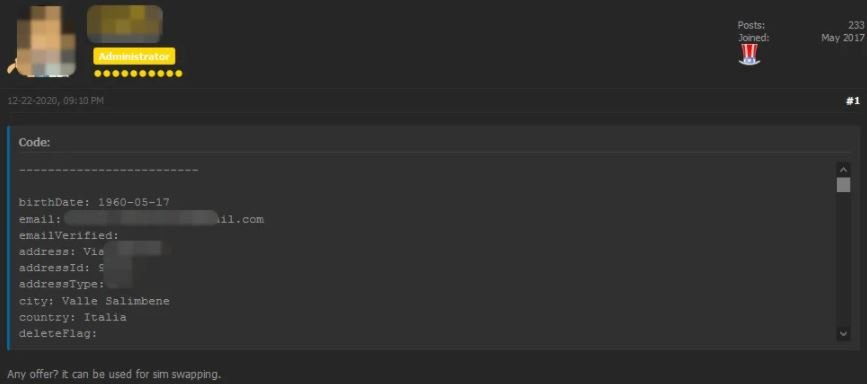
A company spokesperson mentioned that the hackers behind the incident accessed customers’ full names, phone numbers, email addresses, dates of birth and nationality. Besides, hackers gained access to the SIM ICCID, a unique number containing information over each SIM card.
Bank Security says that malicious hackers could combine these details to deploy sophisticated SIM swapping attacks, which would allow them to get control over any compromised SIM card.
The expert also said that at least one threat actor may have buyed access to the database recently, but also pointed out that the vendor has received multiple offers. An anonymous user mentioned that the vendor asked him for $50,000 USD in exchange for the whole database.
After several members of the cybersecurity community asked the vendor for a sample of the database, they could confirm the exposed registers are 100% legitimate.
Ho.Mobile representatives are still trying to minimize the potential impact of the incident, offering their customers a new SIM card for free. Nevertheless, users should consider the risk is still active, so the experts recommend them to enable an identity authentication mechanism to prevent SIM swap attacks.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











