Many users ignore it, but by using their laptop camera or any other camera with a WiFi connection, their MAC address will become visible to anyone on the Internet. Also, network security experts from the International Institute of Cyber Security (IICS) mention that it is possible to detect multiple data from a user even if their camera is not directly connected to the network.

If the camera is using a wired network, the methods described below cannot detect that device. Moreover, WiFi devices and their MAC addresses can be collected using airodump-ng, for devices on the network we are connected to, MAC addresses can be obtained using Nmap, although we need a database of hidden camera manufacturers and cameras in general.
Databases with MAC addresses
Many times we will not be able to find such databases, although we will be able to resort to the lists created by enthusiasts, mention the experts in network security. Another useful tool is the https://directory.ifsecglobal.com/video-surveillance-code004812.html website, which has multiple lists containing this kind of information.
The correct manufacturer name can easily match the MAC database, so we only need to collect the vendor names; this is perfect for our goal of finding hidden cameras.
Create a vendors.sh file:
gedit vendors.sh
Copy the following code into the file:
#!/bin/bash
TMP_FILE='/tmp/vendors.txt'
FILE='vendors.txt'
curl -s 'https://directory.ifsecglobal.com/screens-monitors-code004843.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' > $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/cameras-code004815.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/cctv-poles-and-columns-code004816.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/data-storage-solutions-code009685.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/voice-video-integrated-data-systems-code004908.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/dvr-code004822.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/voice-video-integrated-data-storage-code004941.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/nvr-code004827.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/4k-cameras-code009684.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/anpr-code004813.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/body-worn-cameras-code007865.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/hd-quality-cameras-code007866.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/low-light-level-camera-systems-code007867.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/camera-housings-code004814.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/internet-remote-surveillance-code004932.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/cctv-monitoring-code004999.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/dome-camera-code004821.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/ip-cameras-code004823.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/security-camera-lenses-code004824.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/security-monitors-code004825.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/security-screens-code007437.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/ptz-camera-code004828.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/switches-code004968.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/remote-surveillance-code004829.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/public-space-surveillance-code005012.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/infrared-cameras-code007439.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/thermal-imaging-code004833.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/ai-machinelearning-code009668.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/security-cameras-code007485.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/video-surveillance-code007482.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://directory.ifsecglobal.com/video-surveillance-code004812.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
#curl -s '' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' >> $TMP_FILE
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=A' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=B' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=C' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=D' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=E' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=F' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=G' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=H' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=I' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=J' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=K' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=L' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=M' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=N' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=O' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=P' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=Q' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=R' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=S' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=T' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=U' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=V' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=W' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=X' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=Y' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=Z' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=2' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=3' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=4' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=5' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=7' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=8' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
curl -s 'https://www.ispyconnect.com/sources.aspx?letter=9' | grep -E -o 'man\.aspx\?n=[^"]{1,}"' | sed 's/man.aspx?n=//' | sed 's/"//' | while read -r line ; do
grep -E "$line " vendors.txt >> $TMP_FILE
done
echo 'Tenda Technology Co., Ltd.' >> $TMP_FILE #https://www.google.com/search?q=Tenda+Technology+CCTV&tbm=isch
echo 'LG Innotek' >> $TMP_FILE #https://www.google.com/search?q=LG+Innotek+CCTV&tbm=isch
echo 'Hand Held Products Inc' >> $TMP_FILE #Handheld Thermal Cameras
echo 'Wistron Neweb Corporation' >> $TMP_FILE #https://www.wnc.com.tw/index.php?action=pro_detail&id=76
echo 'HangZhou KuoHeng Technology Co.,ltd' >> $TMP_FILE #https://www.google.com/search?q=HangZhou+KuoHeng+Technology&tbm=isch
echo 'VCS Video Communication Systems AG' >> $TMP_FILE
echo 'D-Link International' >> $TMP_FILE
echo 'Cisco-Linksys, LLC' >> $TMP_FILE
echo 'ICP Internet Communication Payment AG' >> $TMP_FILE
echo 'China Dragon Technology Limited' >> $TMP_FILE
echo 'SAMSUNG TECHWIN CO.,LTD' >> $TMP_FILE
echo 'Hanwha Techwin Security Vietnam' >> $TMP_FILE
echo 'Beward R&D Co., Ltd.' >> $TMP_FILE
echo 'Lorex Technology Inc.' >> $TMP_FILE
echo 'TP-LINK TECHNOLOGIES CO.,LTD.' >> $TMP_FILE
echo 'ABUS Security-Center GmbH & Co. KG' >> $TMP_FILE
echo 'ACM Systems' >> $TMP_FILE
echo 'Aztech Electronics Pte Ltd' >> $TMP_FILE
echo 'Axium Technologies, Inc.' >> $TMP_FILE
echo 'Ace Axis Limited' >> $TMP_FILE
#echo '' >> $TMP_FILE
echo "Total vendors in the list: "`cat $TMP_FILE | wc -l`
cat $TMP_FILE | sort| uniq > $FILE
echo "Unique vendors in the list: "`cat $FILE | wc -l`
The code runs as follows:
bash ./vendors.sh
This will create a vendors.txt file.
Statistics:
Total vendors in the list: 1665
Unique vendors in the list: 680
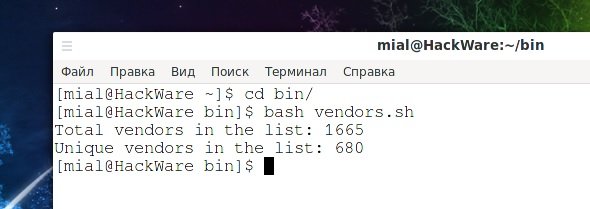
In total, 680 unique vendors were found, network security experts mention. You can then explore the list of vendors.txt and remove any unnecessary entries. For example, I noticed that many entries mention “HUAWEI TECHNOLOGIES CO., LTD”, as this company also makes mobile phones.
WiFi hidden camera scanner using MAC addresses
Now that we have a database of hidden camera manufacturers, we need to collect MAC addresses at our reach. We will use a method that has proven successful before. The following are the commands to start collecting information. Network security experts recommend consulting additional material if you do not fully understand the following instruction.
To parse the .csv file, airodump-ng needs to create it. To do this, we transfer the wireless card to monitor mode. I always start with the following two commands so that no process gets in the way:
sudo systemctl stop NetworkManager
sudo airmon-ng check kill
After that, we will put the WiFi card in monitor mode:
sudo ip link set wlan0 down
sudo iw wlan0 set monitor control
sudo ip link set wlan0 up
Now we run airodump-ng with the following command:
sudo airodump-ng --berlin 60000 -w /tmp/test wlan0
If you are also interested in the 5 GHz band and if your wireless card supports it, you can run it with the following command:
sudo airodump-ng --channel 1-13,36-165 --berlin 60000 -w /tmp/test wlan0
In the example, it is saved in the /home/mial/cameras-01.csv file; you get a response of 1600 lines there, so this will not be parsed manually.
cat /home/mial/cameras-01.csv | wc -l
1600
Next we will have to use a lighter script that will simply check if there is a surveillance camera around. And if so, you can run a heavier script to analyze which access points they are connected to.
Create the fc.sh file:
gedit fc.sh
Copy the following code there:
#!/bin/bash
if [[ "$1" && -f "$1" ]]; then
FILE="$1"
else
echo 'Укажите .csv файл, который вы хотите проанализировать.';
echo 'Пример запуска:';
echo -e "\tbash fc.sh /tmp/test-01.csv";
exit
fi
while read -r line ; do
newline="$(echo $line | grep -E '([A-Z0-9:]{17})')"
if [ "$newline" ]; then
MAC2=`echo "$newline" | sed 's/ //g' | sed 's/-//g' | sed 's/://g' | cut -c1-6`
resultshort="$(grep -i ^$MAC2 ./oui.txt)";
vendor=`echo "$resultshort" | cut -f 3`
#vendor=`echo "$resultshort" | awk -F '\t' '{print $3}'`
if [ "$vendor" ]; then
result3=${vendor%,*}
iscamera=''
iscamera=`cat vendors.txt | grep -i "$result3"`
if [ "$iscamera" ]; then
echo
echo $newline
echo $vendor
echo -e "\t\t\t\033[7mВероятно, это камера или другое устройство слежения\e[0m"
echo
fi
fi
fi
done < <(grep -E '([A-Za-z0-9._: @\(\)\\=\[\{\}\"%;-]+,){5} ([A-Z0-9:]{17})|(not associated)' $FILE | awk -F ',' '{print $1}')
The code runs as shown below:
bash ./fc.sh /ПУТЬ/ДО/ФАЙЛА.csv
If the file we got from airodump-ng is in /tmp/test-01.csv, then the command is as follows:
bash fc.sh /tmp/test-01.csv
We also need a file with a database of MAC addresses and their respective manufacturers; download it to the same directory where you placed the fc.sh file. You must download this file before running fc.sh and all other scripts in this article:
wget http://standards-oui.ieee.org/oui/oui.txt
We fix the downloaded file as it uses a DOS / Windows line break. In our case, without applying the necessary corrections the grep program could not find the line, even if it matches the pattern:
dos2unix -i oui.txt
The script, using a database that maps manufacturers to their assigned MAC addresses (oui.txt), will determine the vendor name for each MAC address collected and then check if this vendor is present in the list of camera manufacturers from surveillance, network security experts mentioned.
The script will display the MAC address and manufacturers’ names of all possible cameras. If the script didn’t show anything, nothing was found.
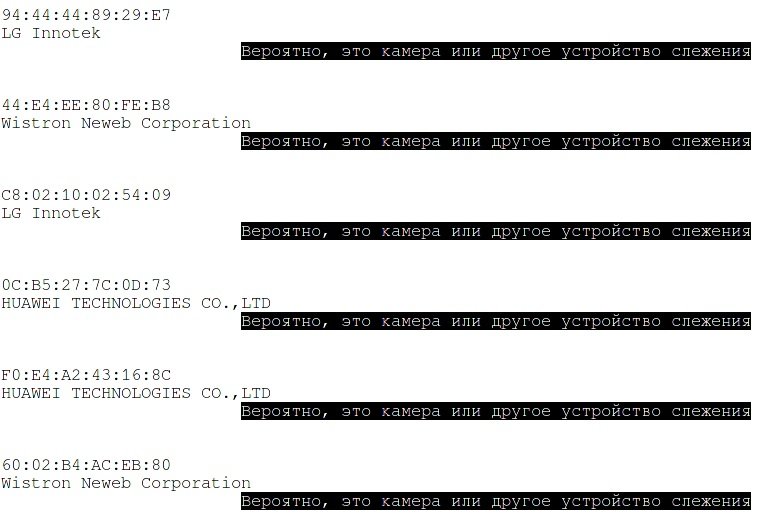
Remember that some vendors produce other devices besides security cameras, therefore “false alarms” are very likely to occur. If something is found, or even if the script shows a dozen devices, this does not mean that they are all hidden WiFi cameras. First, pay attention to the manufacturer, as these are often smartphone manufacturers.
Still, if you find something interesting, network security experts recommend using a script that shows which access points all the devices are connected to.
Create the findcameras.sh file:
gedit findcameras.sh
Copy the following code into it:
#!/bin/bash
if [[ "$1" && -f "$1" ]]; then
FILE="$1"
else
echo 'Укажите .csv файл, который вы хотите проанализировать.';
echo 'Пример запуска:';
echo -e "\tbash findcameras.sh /tmp/test-01.csv";
exit
fi
echo -e "\033[1mВсего точек доступа: \033[0;31m`grep -E '([A-Za-z0-9._: @\(\)\\=\[\{\}\"%;-]+,){14}' $FILE | wc -l`\e[0m"
echo -e "\033[1mВсего клиентов: \033[0;31m`grep -E '([A-Za-z0-9._: @\(\)\\=\[\{\}\"%;-]+,){5} ([A-Z0-9:]{17})|(not associated)' $FILE | wc -l`\e[0m"
echo -e "\033[1mИз них клиентов без ассоциации: \033[0;31m`grep -E '(not associated)' $FILE | wc -l`\e[0m"
echo -e "\033[0;36m\033[1mИнформация о сетях:\e[0m"
while read -r line ; do
if [ "`echo "$line" | cut -d ',' -f 14`" != " " ]; then
echo -e "\033[1m" `echo -e "$line" | cut -d ',' -f 14` "\e[0m"
else
echo -e " \e[3mне удалось получить имя сети\e[0m"
fi
fullMAC=`echo "$line" | cut -d ',' -f 1`
echo -e "\tMAC-адрес: $fullMAC"
MAC=`echo "$fullMAC" | sed 's/ //g' | sed 's/-//g' | sed 's/://g' | cut -c1-6`
result="$(grep -i -A 1 ^$MAC ./oui.txt)";
if [ "$result" ]; then
echo -e "\tПроизводитель: `echo "$result" | cut -f 3`"
else
echo -e "\tПроизводитель: \e[3mИнформация не найдена в базе данных.\e[0m"
fi
is5ghz=`echo "$line" | cut -d ',' -f 4 | grep -i -E '36|40|44|48|52|56|60|64|100|104|108|112|116|120|124|128|132|136|140'`
if [ "$is5ghz" ]; then
echo -e "\t\033[0;31mРаботает на 5 ГГц!\e[0m"
fi
printonce="\tИнформация о подключённых клиентах:"
while read -r line2 ; do
clientsMAC=`echo $line2 | grep -E "$fullMAC"`
if [ "$clientsMAC" ]; then
if [ "$printonce" ]; then
echo -e $printonce
printonce=''
fi
echo -e "\t\t\033[0;32m" `echo $clientsMAC | cut -d ',' -f 1` "\e[0m"
MAC2=`echo "$clientsMAC" | sed 's/ //g' | sed 's/-//g' | sed 's/://g' | cut -c1-6`
result2="$(grep -i -A 1 ^$MAC2 ./oui.txt)";
if [ "$result2" ]; then
echo -e "\t\t\tПроизводитель: `echo "$result2" | cut -f 3`"
ismobile=`echo $result2 | grep -i -E 'Olivetti|Sony|Mobile|Apple|Samsung|HUAWEI|Motorola|TCT|LG|Ragentek|Lenovo|Shenzhen|Intel|Xiaomi|zte|MEIZU'`
warning=`echo $result2 | grep -i -E 'ALFA|Intel'`
if [ "$ismobile" ]; then
echo -e "\t\t\t\033[0;33mВероятно, это мобильное устройство\e[0m"
fi
if [ "$warning" ]; then
echo -e "\t\t\t\033[0;31;5;7mУстройство может поддерживать режим монитора\e[0m"
fi
resultshort="$(grep -i ^$MAC2 ./oui.txt)";
vendor=`echo "$resultshort" | cut -f 3`
if [ "$vendor" ]; then
result3=${vendor%,*}
iscamera=''
iscamera=`cat vendors.txt | grep -i "$result3"`
if [ "$iscamera" ]; then
echo -e "\t\t\t\033[7mВероятно, это камера или другое устройство слежения\e[0m"
fi
fi
else
echo -e "\t\t\tПроизводитель: \e[3mИнформация не найдена в базе данных.\e[0m"
fi
probed=`echo $line2 | cut -d ',' -f 7`
if [ "`echo $probed | grep -E [A-Za-z0-9_\\-]+`" ]; then
echo -e "\t\t\tИскал сети: $probed"
fi
fi
done < <(grep -E '([A-Za-z0-9._: @\(\)\\=\[\{\}\"%;-]+,){5} ([A-Z0-9:]{17})|(not associated)' $FILE)
done < <(grep -E '([A-Za-z0-9._: @\(\)\\=\[\{\}\"%;-]+,){14}' $FILE)
echo -e "\033[0;36m\033[1mИнформация о неподключённых клиентах:\e[0m"
while read -r line2 ; do
clientsMAC=`echo $line2 | cut -d ',' -f 1`
echo -e "\033[0;31m" `echo $clientsMAC | cut -d ',' -f 1` "\e[0m"
MAC2=`echo "$clientsMAC" | sed 's/ //g' | sed 's/-//g' | sed 's/://g' | cut -c1-6`
result2="$(grep -i -A 1 ^$MAC2 ./oui.txt)";
if [ "$result2" ]; then
echo -e "\tПроизводитель: `echo "$result2" | cut -f 3`"
ismobile=`echo $result2 | grep -i -E 'Olivetti|Sony|Mobile|Apple|Samsung|HUAWEI|Motorola|TCT|LG|Ragentek|Lenovo|Shenzhen|Intel|Xiaomi|zte'`
warning=`echo $result2 | grep -i -E 'ALFA|Intel'`
if [ "$ismobile" ]; then
echo -e "\t\033[0;33mВероятно, это мобильное устройство\e[0m"
fi
if [ "$warning" ]; then
echo -e "\t\033[0;31;5;7mУстройство может поддерживать режим монитора\e[0m"
fi
resultshort="$(grep -i ^$MAC2 ./oui.txt)";
vendor=`echo "$resultshort" | cut -f 3`
if [ "$vendor" ]; then
result3=${vendor%,*}
iscamera=''
iscamera=`cat vendors.txt | grep -i "$result3"`
if [ "$iscamera" ]; then
echo -e "\t\t\t\033[7mВероятно, это камера или другое устройство слежения\e[0m"
fi
fi
else
echo -e "\tПроизводитель: \e[3mИнформация не найдена в базе данных.\e[0m"
fi
probed=`echo $line2 | cut -d ',' -f 7`
if [ "`echo $probed | grep -E [A-Za-z0-9_\\-]+`" ]; then
echo -e "\tИскал сети: $probed"
fi
done < <(grep -E '(not associated)' $FILE)
The code will run as follows:
bash findcameras.sh /ПУТЬ/ДО/ФАЙЛА.csv
For example:
bash findcameras.sh /tmp/test-01.csv
This script, like the previous one, requires oui.txt and vendors.txt files. Hand Held Products Inc manufactures both thermal imaging cameras and various barcode readers, etc. It can be any of these devices, since it is a TD from a store.
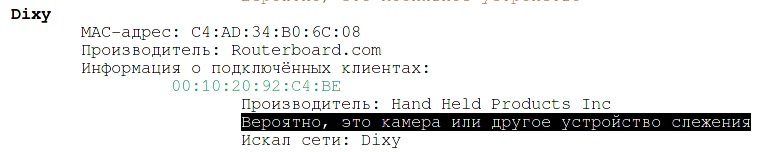
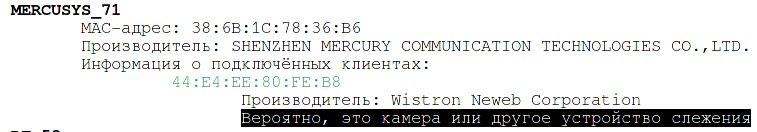
Wistron Neweb Corporation manufactures a variety of electronic products, including a very popular IP camera.
Instead of connecting via a WiFi network, cameras can use a wired network; these cameras will not be included in the list.
Search for surveillance cameras on the local network
This method works only on networks where you can get the MAC addresses of other devices, that is, only on local networks. Scanning the Internet is useless. Among the LANs we often connect to we can find public WiFi access points in airports, hotels, restaurants and public transportation, etc.
Create the fcl.sh file:
gedit fcl.sh
Copy the following code into it:
#!/bin/bash
if [[ "$1" ]]; then
NET="$1"
else
echo 'Укажите подсеть для поиска камер наблюдения';
echo 'Пример запуска:';
echo -e "\tbash ./fcl.sh 192.168.0.0/24";
exit
fi
found=0
while read -r line ; do
newline=$line
if [ "$newline" ]; then
MAC2=`echo "$newline" | sed 's/ //g' | sed 's/-//g' | sed 's/://g' | cut -c1-6`
resultshort="$(grep -i ^$MAC2 ./oui.txt)";
vendor=`echo "$resultshort" | cut -f 3`
if [ "$vendor" ]; then
result3=${vendor%,*}
iscamera=''
iscamera=`cat vendors.txt | grep -i "$result3"`
if [ "$iscamera" ]; then
echo
echo $newline
echo $vendor
echo -e "\t\t\t\033[7mВероятно, это камера или другое устройство слежения\e[0m"
echo
found=1
fi
fi
fi
done < <(sudo nmap -n -sn -PR -PS -PA -PU -T5 $NET | grep -E -o '[A-Z0-9:]{17}')
if [ $found -eq 1 ]; then
sudo nmap -A $NET
fi
Run it like this (remember that Nmap requires administrator privileges):
sudo bash fcl.sh СЕТЬ/МАСКА
For example:
sudo bash ./fcl.sh 192.168.0.0/24
If devices with MAC addresses from surveillance camera manufacturers are found, they will be displayed below. Otherwise, no response will be displayed.
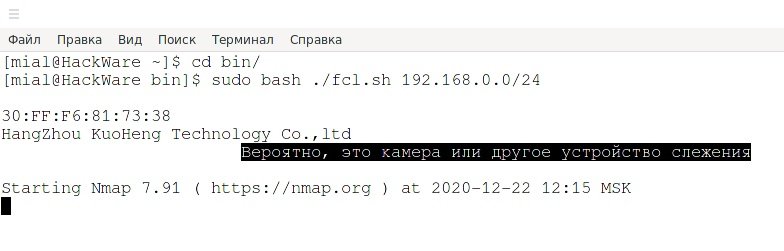
According to network security specialists, if at least one camera is found, another even more aggressive Nmap scan will be launched, with complete output of the results so that you can see the device’s IP, and it will also try to determine the version of the device, operating system and services.
Additional scan output snippet:
|_http-title: NETSurveillance WEB
554/tcp open rtsp H264DVR rtspd 1.0
|_rtsp-methods: OPTIONS, DESCRIBE, SETUP, TEARDOWN, GET_PARAMETER, SET_PARAMETER, PLAY, PAUSE
8899/tcp open soap gSOAP 2.7
|_http-server-header: gSOAP/2.7
The NETSurveillance WEB heading suggests that it is a network surveillance camera. Open ports 554 and 8899 pertain to IP camera specific RTSP and ONVIF services.
Conclusion
The quality of the scan is mainly determined by the quality of the surveillance camera manufacturers list; in other words, more and better MAC address lists are required, which is completely up to ethical hacking enthusiasts.
Note that multiple vendors were added to the vendors.sh file. This information was obtained in the following ways:
- Data captured in places where cameras are visible (stores, banks, etc.)
- Googling terms like “CCTV vendor found”, “vendor camera found”, etc.
This secure material will be of great use to researchers and network security specialists. To see more works like this, visit the official platforms of the International Institute of Cyber Security (IICS).

Cyber Security Specialist with 18+ years of industry experience . Worked on the projects with AT&T, Citrix, Google, Conexant, IPolicy Networks (Tech Mahindra) and HFCL. Constantly keeping world update on the happening in Cyber Security Area.










