More details about the severe security incident at SolarWinds are revealed every day. This time, an analysis reports the detection of a backdoor possibly developed by a second hacking group involved in the attack; identified as Supernova, this is a webshell injected into SolarWinds Orion code that would allow threat actors to execute arbitrary code on systems that use the compromised version of this product.
Supernova is a “trojanized” variant of a legitimate .NET library (app_web_logoimagehandler.ashx.b6031896.dll) used in SolarWinds Orion implementations. Threat actors were able to modify it in order to bypass the automated defense mechanisms of the target system. The Orion software uses the DLL to expose an HTTP API, allowing the host to respond to other subsystems when it requests a specific image in GIF format.
Matt Tennis, security specialist in charge of the report, mentions that this variant of malware could bypass even manual scanning processes, as the code implemented in the legitimate DLL is completely harmless. Hackers added four parameters to the legitimate file to receive signals from the malicious C&C.
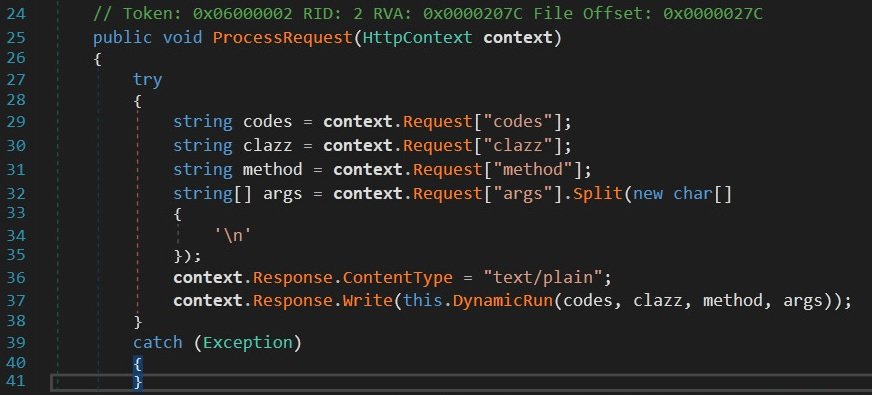
The specialist only detected the DynamicRun method, which compiles the parameters of a .NET assembly into memory on the fly without leaving artifacts on the target device disk.
Threat actors would have used this method to send arbitrary code and execute it in the context of the user. A sample of this malware is already available in the VirusTotal database, thanks to the work of 69 antivirus engines. It is unknown how long Supernova has been present on the Orion Platform, although experts estimate that the tool has been compromised at least since March this year.
The report mentions that Supernova appears to have been developed by an advanced hacking group: “Code execution in memory makes Supernova a very strange variant, as it eliminates the need for additional network callbacks to otherwise remove initial C&C requests.” Researchers continue to analyze malware samples collected after the security incident at SolarWinds and, although it seems too early to issue conclusions, chances are there are at least two hacking groups involved.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










