WiFi security is an element that sometimes receives little attention from system administrators, although it is a fundamental factor in consolidating a secure IT environment, pentesting specialists from the International Institute of Cyber Security (IICS) say.
Below are details on some tools that, while feature different functions, were developed to provide you with as much information as possible about a WiFi network at your fingertips.
When performing these wireless network analyses, pentesting experts mention that you are more likely to choose the network that gives you the best performance and the fastest speeds. In general, most listed programs provide information such as:
- WiFi signal strength
- MAC addresses
- Channels, among others
Other tools feature more advanced options, such as network troubleshooters and modification of established settings, as mentioned by pentesting experts.
Interested administrators will be able to use these tools for basic network analysis tasks in all kinds of environments, from homes to business environments. These tools will help you detect where the WiFi signal strength weakens or find the reasons why your network performance is below optimal.
Xirrus Wi-Fi Inspector
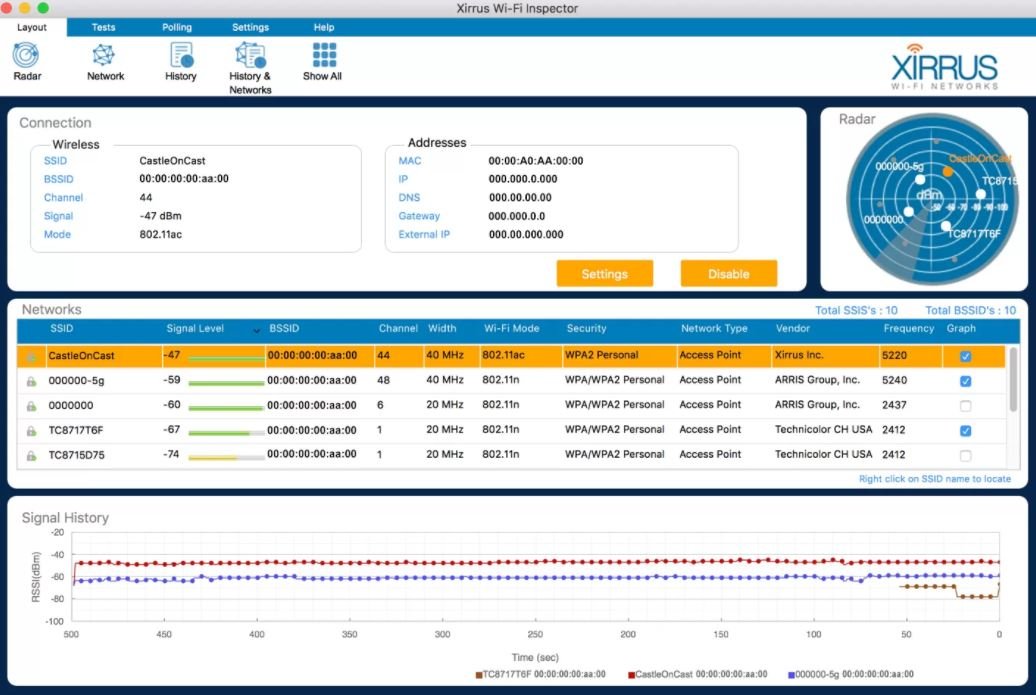
This tool was specifically designed to monitor the status of a wireless network in real time. Available for Windows and macOS systems, Wi-Fi Inspector supports the latest wireless connectivity standards, as well as detecting unauthorized access points and having IT support features, pentesting experts mention.
InSSIDer
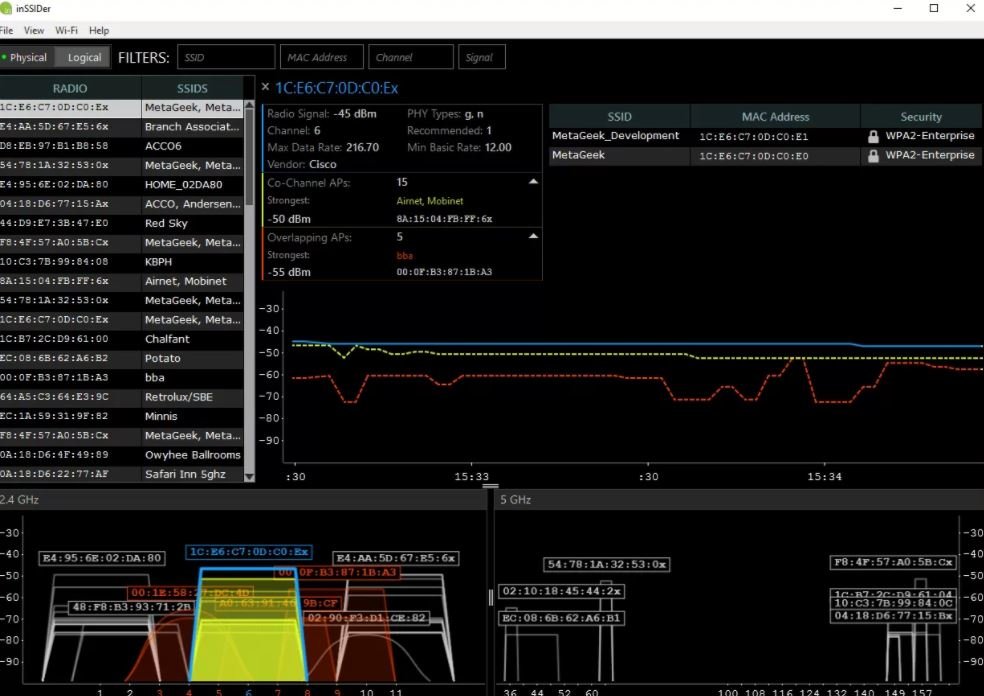
This tool displays the MAC address of each access point, in addition to the type of encryption it uses and the signal strength. InSSIDer is one of the most popular network troubleshooters, although there is no free version of the software.
On the benefits side, for less than $20 USD administrators will be able to measure the intensity and performance of their WiFi signal depending on the location of the router, so they can determine how walls or furniture interfere with the network.
WifiInfoView
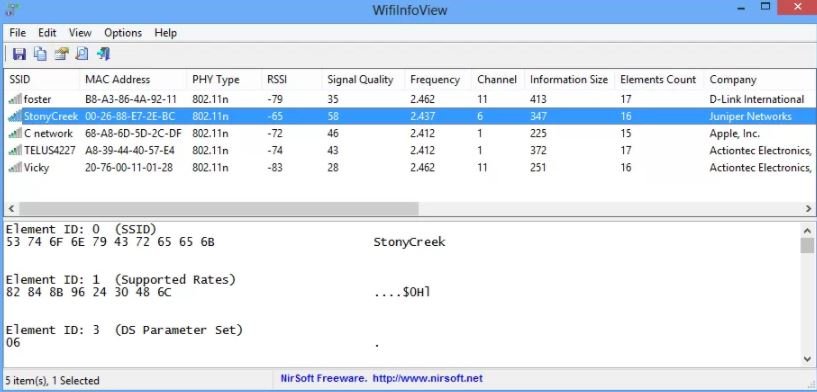
This is a nearby wireless network scanner that gives users detailed information about each available connection. According to pentesting experts, among the data that this tool can list are:
- Network name (SSID)
- MAC address
- PHY level
- Signal quality
- Top speed
- Router name and model
WifiInfoView also has a special function so that all detected wireless networks are grouped by channel number and their maximum speed. This is a free tool although at the moment it is only available for Windows systems.
Wifi Analyzer for Android
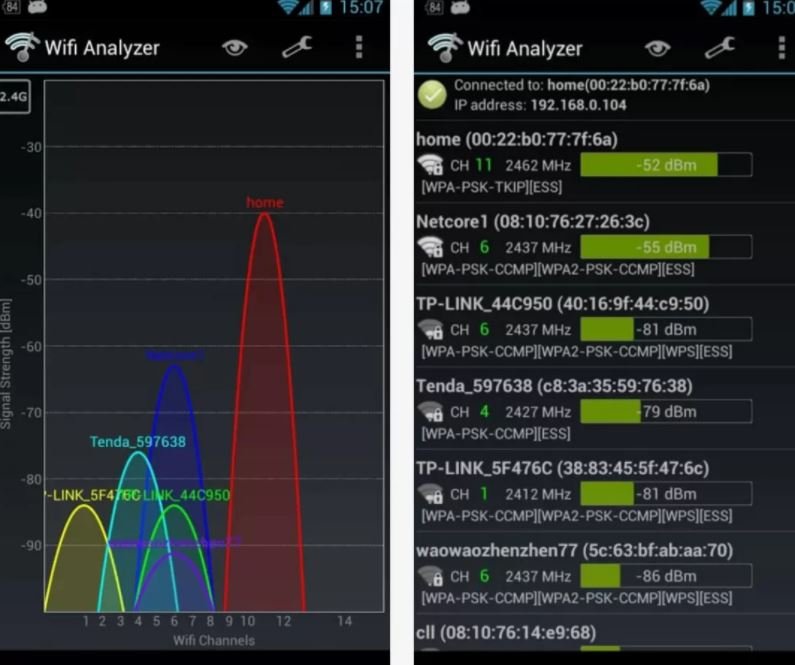
Using this tool you can turn any Android device into a powerful WiFi network analyzer, as mentioned by pentesting specialists. WiFi Analyzer can help you find the best network at your reach for your router, showing nearby WiFi channels looking for the least requested.
WiFi Analyzer also has tools like Lan Neighbors, which provides information about nearby routers, and OUI Lookup, to verify MAC addresses.
NetSurveyor
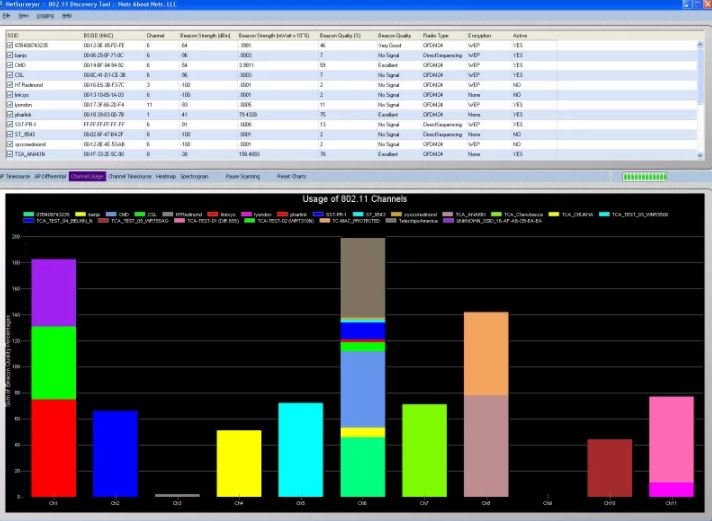
This is a tool to validate your network configuration, find areas with low WLAN coverage, detect signal interference and unauthorized access points. According to pentesting experts, the data is displayed to the user using several charts and tables very easy to interpret, not to mention that it is possible to obtain the reports thrown in PDF format.
In addition to these advantages, NetSurveyor is a free tool that can provide great learning to the uninitiated, although at the moment it is only available for Windows systems.
IICS experts believe that using these tools can help system administrators complete their security environment, as well as increase the efficiency of WiFi connections.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










