Specialists from Ben-Gurion University, Israel, published an investigation describing an attack to turn any device’s RAM card into a wireless transmitter in order to receive sensitive data from air-gapped environments with no WiFi to locations controlled by attackers.
The attack, dubbed AIR-FI, is a type of undercover channel technique for data exfiltration: “This is not a technique for accessing a computer, but is a method of data theft that few security systems could foresee,” experts say.
Although these exfiltration channels do not pose problems for conventional computer users, they are a real threat to air-gapped systems, considered highly secure. These systems are implemented in government, military and business facilities for the protection of confidential documents.
While these attacks are considered rare, their existence has forced multiple organizations to reconsider the architecture of their systems to avoid leaving loose ends.
The AIR-FI attack is based on the electromagnetic waves generated by any electronic component as electricity circulates. Threat actors could place malicious code in an air-gapped system by manipulating the electrical current inside the RAM card of the target device to generate electromagnetic waves with a frequency identical to that generated by the WiFi spectrum (2400 Ghz).
The generated signal can be intercepted by any device with a WiFi antenna integrated within its range. Researchers mention that the attack was tested with various air-gapped systems, managing to extract data at a rate of up to 100b/s, which ended up on computers, smartphones and IoT devices, among others.
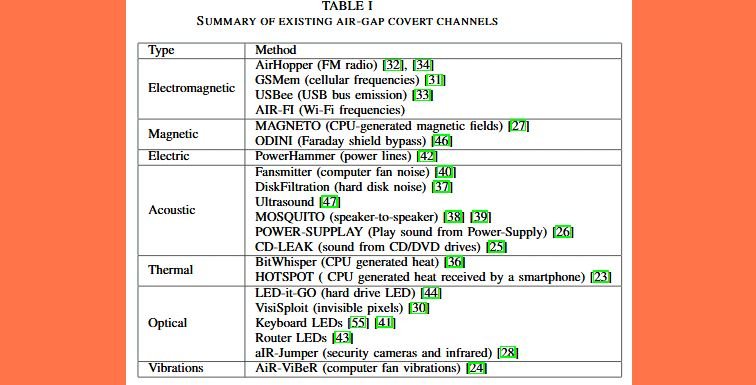
As a possible solution, specialists suggest that organizations with air-gapped systems deploy mechanisms to interfere with these signals to prevent transmission to threat actors. Ben-Gurion researchers have found at least a dozen more of similar mechanisms before. Some of these mechanisms are described below:
- LED-it-Go: Data extraction in air-gapped systems through the activity LED lights of a hard drive
- USBee: The data bus of a USB connector emits electromagnetic emissions that can be used for data leakage
- AirHopper: The local GPU card is abused to emit electromagnetic signals to a nearby mobile phone, which is also used to steal data
As mentioned earlier, these are not considered critical flaws, although air-gapped system administrators should consider security recommendations.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











