Information security specialists report that more than 85,000 SQL databases have been put up for sale on a dark web forum in exchange for $550 USD each. Apparently this illegal portal is part of a complex scheme of theft and sale of confidential information compromised as a product of other incidents.
Databases have become one of the main targets of malicious hackers, who have devised methods to easily compromise these resources in order to threaten owners with deleting all information if their demands are not met.
Although initial ransom notes mentioned that victims should contact criminals via email, eventually the operators of this malicious scheme automated their operations and created a dark web portal to conduct their negotiations with the victims.
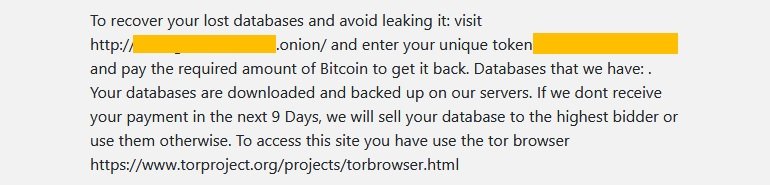
In the following screenshot we can see how before accessing the website victims are asked to enter a unique identifier found in the ransom note.
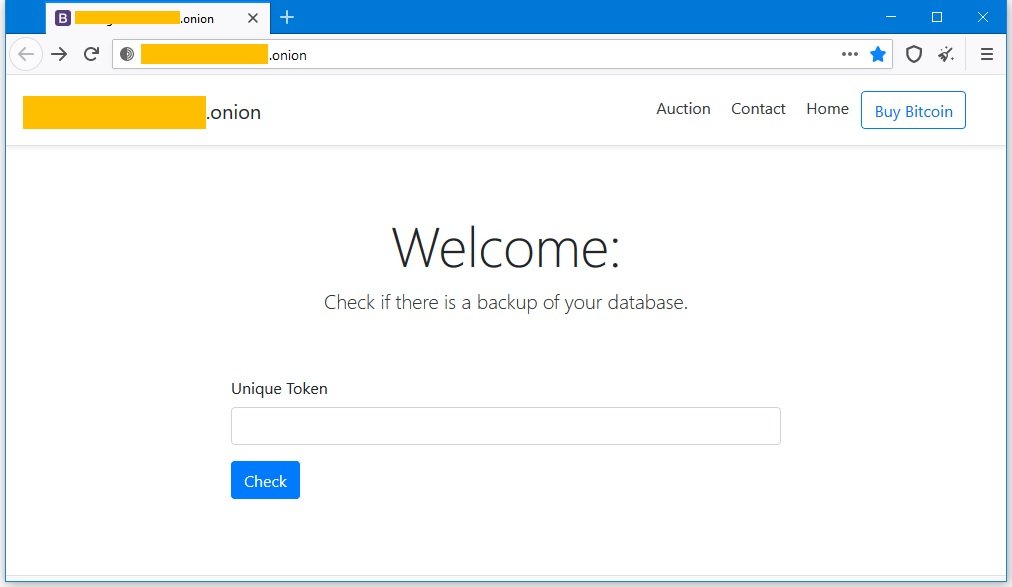
If victims do not pay the ransom within nine days after the incident, their data is auctioned in another section of the portal.
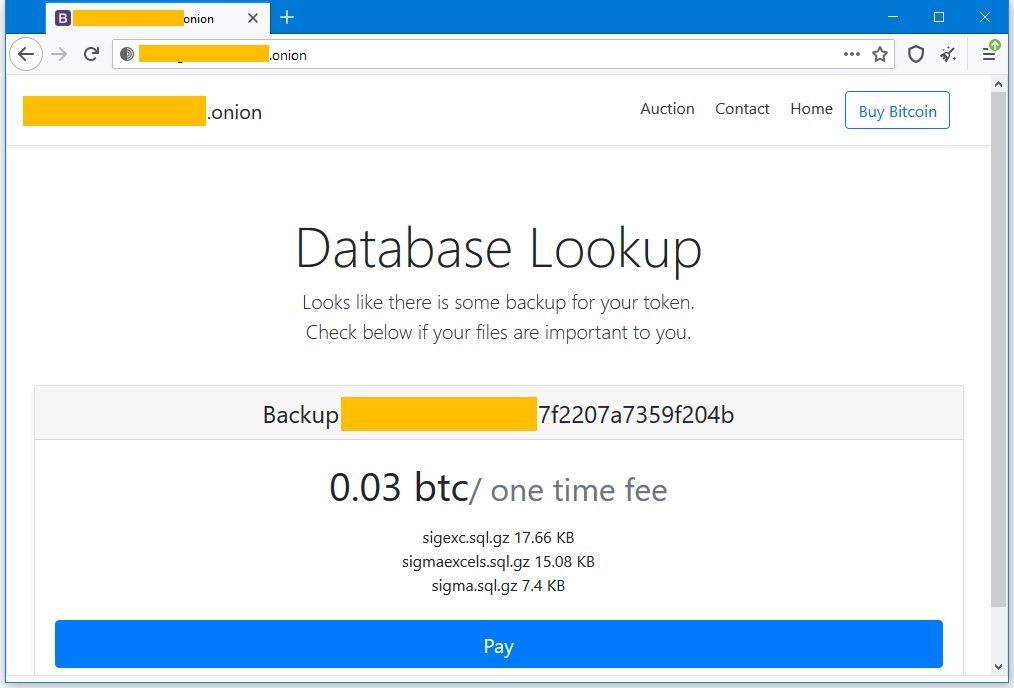
All payments on the platform must be made via Bitcoin transfers. Converted to dollars, this price is around $500 USD.
After analyzing the website, specialists concluded that their processes are fully automated, so threat actors do not perform further analysis of compromised databases looking for useful information. The cybersecurity community has fully identified all incidents linked to this hacking group, as they are used to put their claims in SQL tables titled “WARNING”.
Apparently most compromised databases belong to MySQL servers; although experts do not rule out that other database systems (such as PostrgeSQL or MSSQL) may have been compromised.
On the other hand, samples of these attacks have been detected throughout 2020, with ransom notes appearing on Reddit forums, MySQL, support platforms and all kinds of personal and business blogs.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











