Millions of Microsoft Office 365 users around the world are exposed to a new malicious phishing campaign targeting employees of financial companies, healthcare services, insurers, manufacturing companies, telecommunications, and public organizations.
This campaign could pose a high risk to affected companies, as even employees who have received information security training could be deceived by these seemingly legitimate messages.
According to a report by security firm Ironscales, more than 100 of its customers have been affected by this attack, revealed shortly after this same team of researchers discovered that about 50% of these attacks are able to bypass Microsoft’s protection mechanisms against advanced threats.
This attack uses a domain impersonation technique that occurs when the address of a fraudulent email fully matches the forged domain. Thanks to this, threat actors send messages from seemingly legitimate domains in order to deceive target users.
To give greater credibility to the scam, criminals use formal language, adding a tone of urgency that instills nervousness and prevents victims from detecting latent danger. The message includes a link that redirects users to a fraudulent portal where their sensitive information will be captured and sent to the attackers’ servers.
The portal prompts users to enter their sign-in credentials for Office 365; in this way threat actors collect the usernames and passwords necessary to gain illegitimate access to confidential information that will in the end be offered for sale on dark web forums.
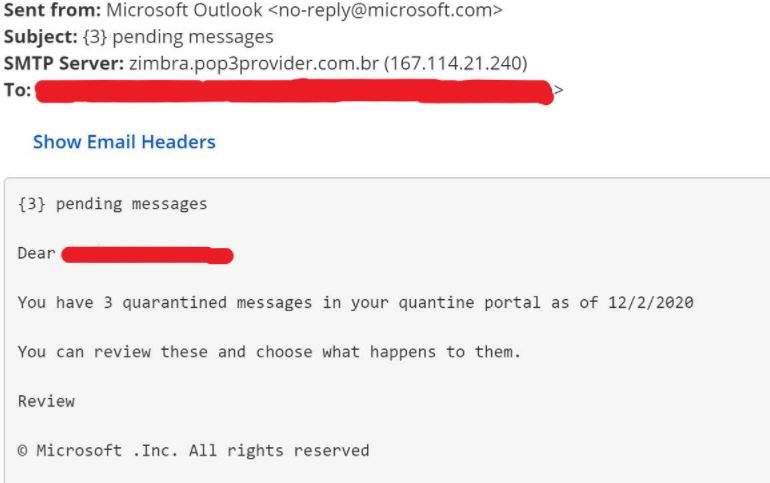
A noteworthy fact about this fraudulent campaign is that the complete forgery of a web domain is not considered a highly sophisticated attack, so conventional security measures (such as Secure Email Gateway) are perfectly capable of detecting and mitigating these incidents. The following is an example of an attack from a <no-reply@microsoft.com> domain, which failed in its attempt to bypass a security mechanism.
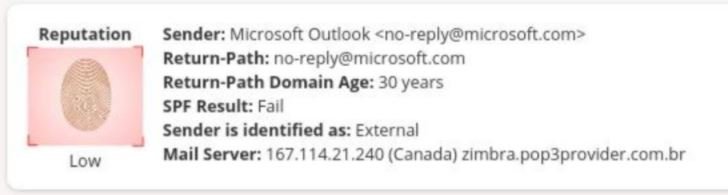
However, experts found that Microsoft servers do not apply the DMARC protocol, so such emails are not recognized as malicious by security controls, such as Office 365 EOP and ATP. To make matters worse, Microsoft is among the 5 companies most affected by domain forgery.
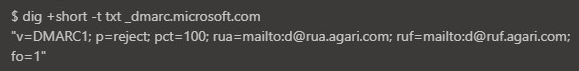
Ironscales experts recommend potentially affected organizations make sure to enable DMARC, as well as keep their email security tools up-to-date and train their staff to identify potential cybersecurity risks.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











