A flaw in a D-Link firmware, used by multiple router models with VPN pass-through functionality, would allow threat actors to take full control of an affected device. The vulnerability affects DSR-150, DSR-250, and DSR-1000AC router models, running firmware 3.17 or earlier.
The flaw, reported by the Digital Defense team of researchers last August, is a root command injection condition that can be exploited remotely if it is possible to access the “Unified Services Router” web interface using the conventional Internet.
According to the report, hackers could use their access to intercept or modify traffic and even attack other connected devices on the same network. The company has already recognized the problem by publishing some details a few days ago and recognizing that some CGI LUAs are accessible without authentication, which could be abused to run a LUA library function to pass user input.
The following is a list that lists vulnerable router models:
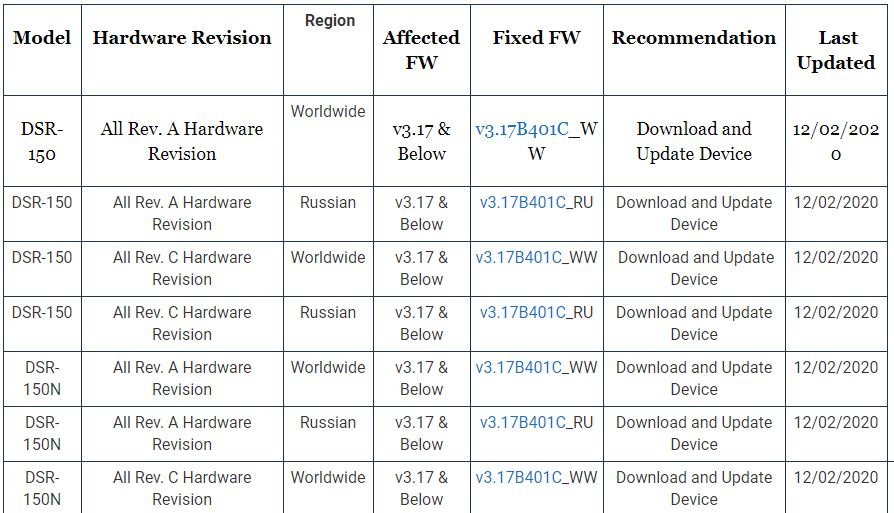
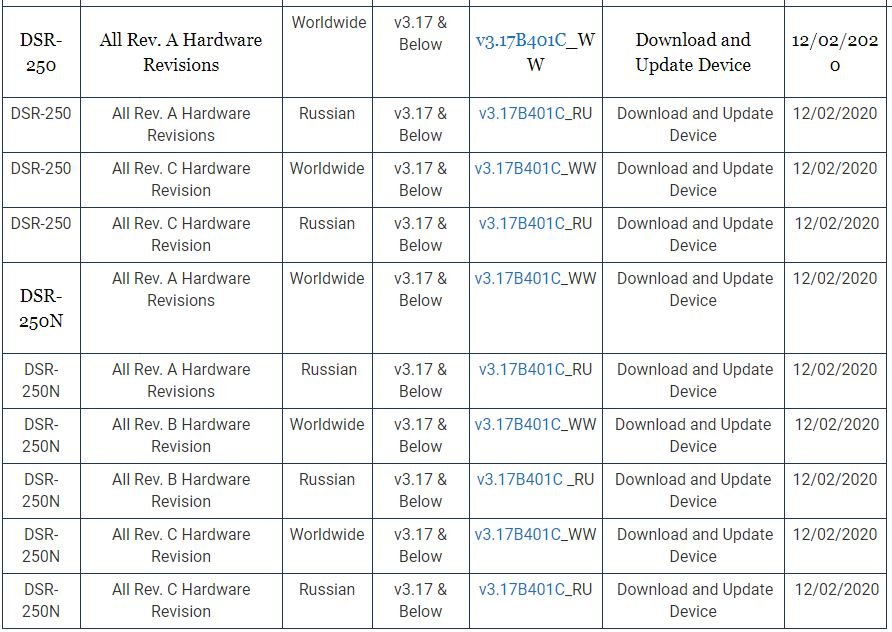
D-Link explains that hackers could enter malicious data into a command designed to calculate a hash that is processed by the “os.popen()” function. Following the Digital Defense report, which concerned only the DSR-250 router model, D-Link assessed that the vulnerable firmware version powered the other models (DSR-250/N, DSR-500, and DSR-1000AC).
The company released firmware version 3.17B401C, which contains fixes for compromised models.
In addition, the researchers reported two other low severity failures. The first failure is an exploitable root command injection using Unified Services Router that requires authentication, while the last failure is a crontab injection that would allow arbitrary commands with root privileges to run.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











