A recent report mentions that a hacker has released a database on HIV/AIDS patients. The alleged hacker also mentions that it can obtain databases of patients diagnosed with tuberculosis in multiple regions of the world.
According to a leak of a Telegram channel, the information was released on November 18 and includes information from more than 2,400 patients allegedly obtained from some health institutions in various parts of the world. This incident was perpetrated by the same Russian-speaking hacker who would have compromised the information of the Specialized Clinical Center in Novgorod, Russia. The cybercriminal demanded about 60,000 rubles in exchange for information.
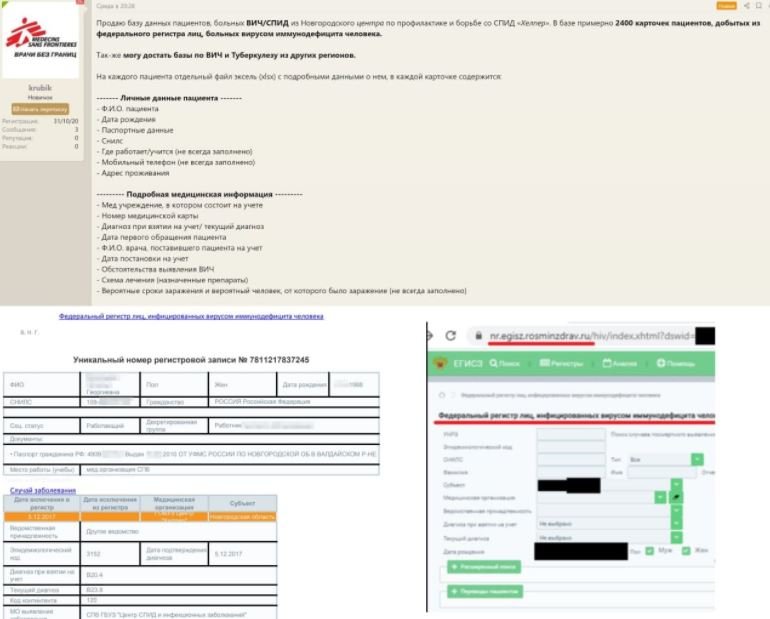
The information compromised on this occasion includes data such as:
- Full name
- Date of birth
- Passport details
- Phone
- Workplace
- Registration and address of real residence
- Detailed medical information
The seller published samples of three patients’ files, as well as a screenshot of access to a public health portal in Russia.
Selling sensitive information is an attractive business for cybercriminal groups, especially records related to people’s health. Recently, specialists at a security firm reported that a cybercriminal was selling a database of patient information diagnosed with COVID-19, all based in Latin America.
According to specialists who investigated this incident, the hacker is selling 350,000 records, including full names, phones, and addresses of people who have contracted the virus. The cyber-criminal claims that the database contains patient information in Mexico, Peru, Colombia and Argentina.
A technical cybersecurity alert issued jointly by four federal agencies, including the Treasury Department and fbi, mentions that a further increase in hacking efforts against hospitals deployed by the Russian government after a period of near-zero activity has been detected this year. Much of the data identified by cybersecurity experts is publicly available, and almost all cybercriminals regularly buy and sell on dark web platforms.
This information enables threat actors to deploy phishing, identity theft, and electronic fraud campaigns, so it’s critical that users protect themselves against such incidents.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











