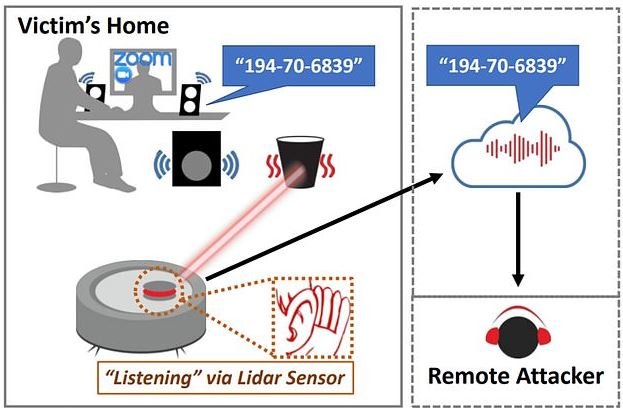
A group of specialists discovered that some robotic vacuum cleaner models could be abused by threat actors to listen to users’ private conversations remotely. Experts managed to access Lidar readings from a Xiaomi Roborock cleaner, which helps the device not to collide with furniture.
Lidar is a method for measuring distances through laser beams, although it can also capture sound signals by gaining reflections from objects around the device, which vibrate due to nearby sound sources, such as a person’s voice.
According to the report, threat actors could abuse the Lidar sensor to detect acoustic signals in the environment, collect their data remotely, and process the signal using “deep learning” techniques to extract audio data. A successful attack would allow you to extract information from your device and record user conversations, which could expose sensitive information.
Experts emphasize the serious problem posed by this attack, as even a smart device without a built-in microphone can be used to spy on users: “We are opening the doors of our house to intruders without even noticing it,” says security specialist Nirupam Roy.
In addition, Lidar allows these devices to build maps of each user’s home, information that is stored in the cloud. This practice poses a data breach risk that could expose affected users to invasive advertising campaigns and even compromise physical integrity and user security.
On the attack, experts mention that this hacking method relates to the manipulation of Lidar technology: “The navigation systems of these vacuum cleaners make a laser beam shine around a room, detecting the laser reflection when it bounces off nearby objects,” the report says. The attack works in the same way as a laser microphone, which projects a light onto an object placed near a sound source and measures this vibration to retrieve the audio source.
Experts say a dispersed signal received by the vacuum sensor provides only a fraction of the information needed to recover the sound waves. In testing, researchers hacked a vacuum cleaner to control the position of the laser beam and send the detected data to their computers via WiFi without interfering with the device’s navigation.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











