Compal Electronics, the world’s second largest laptop manufacturer, was the victim of a DoppelPaymer ransomware attack over the past weekend. Attackers demand a ransom of nearly $17 million from the company, recognized for its collaboration with renowned empress such as Apple, HP, Dell, Acer, among others.
Local media began receiving reports of the incident in recent days, although at first a company representative claimed that it was only a minor failure in the automation systems of its offices: “This Company is allegedly being attacked by hackers, although its operations are being restored,” the reports said.
Soon after, researchers from the BleepingComputer platform confirmed that the company was under ransomware attack, including a screenshot of the ransom note sent by the hackers.
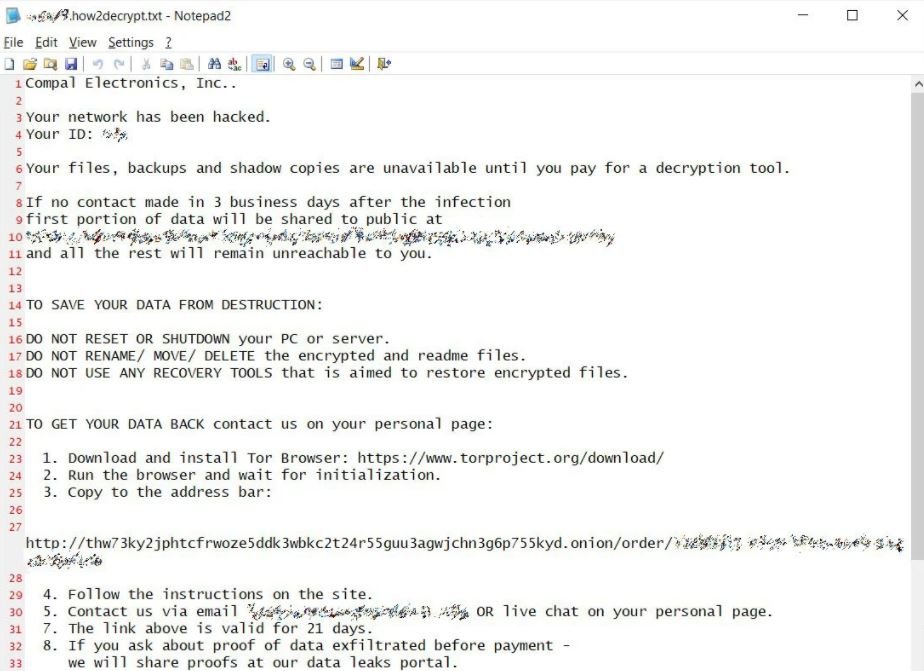
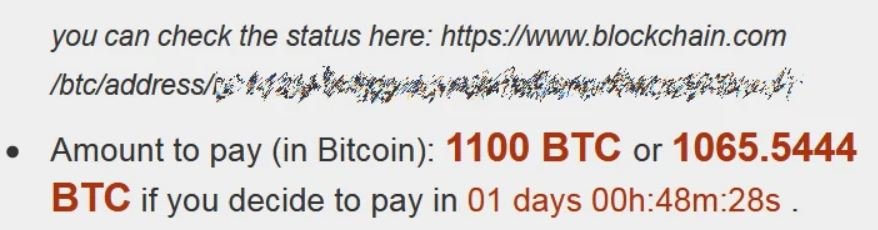
About the perpetrators of the attack, specialists mention that this is a group recognized for their continued attacks on business targets in order to gain access to administrator credentials and use them to spread the infection across the entire attacked network; Hackers then deliver DoppelPaymer payloads on all devices connected to the network and wait for victims to find the ransom note. In this case cybercriminals demand a ransom of 1100 Bitcoin from Compal, almost $17 million at the current exchange rate.
Although this group of ransomware also often steals information and uses it to pressure victims, it is still unknown whether Compal was also the subject of this practice. This is a trend that multiple hacking groups have recently adopted and that is apparently paying off.
Finally, hackers also tend to raise the ransom cost in case the payment is not made immediately. Other organizations attacked by DoppelPaymer previously include Petróleos Mexicanos (PEMEX), the California government, the University of Newcastle, Hall County in Georgia and Bretagne Télécom.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











