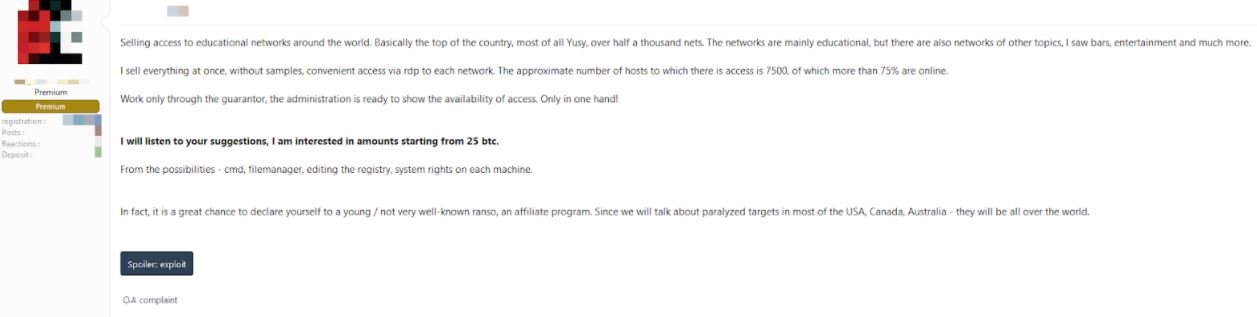
A group of malicious hackers is selling access to the networks of nearly 7500 organizations through various Russian-speaking dark web forums. Most affected organizations provide education services, but also include access to entertainment companies, the bar industry, among others. All of these deployments are vulnerable to Remote Desktop Protocol (RDP) attacks.
Access is sold through an auction, with an initial offer from 25 Bitcoin (approximately $330k USD). Interested parties can also buy all the accesses without entering the auction in exchange for 75 Bitcoin (almost one million USD).
Search for affected devices
It is difficult to know how many targets can fall victim to an RDP attack, although it is possible to know an approximate number using the Shodan IoT finder. An analysis by Cybernews yielded alarming results:

Millions of devices are open to the public, although this does not mean that all of them are vulnerable to RDP attacks, since some machines may have all their updates installed. Still, a significantly high percentage of the devices analyzed could be subject to these attacks.
Using a technique known as honeypot, researchers were able to detect how often threat actors exploit RDP vulnerabilities, collecting evidence of more than 440,000 security incidents within seven weeks.
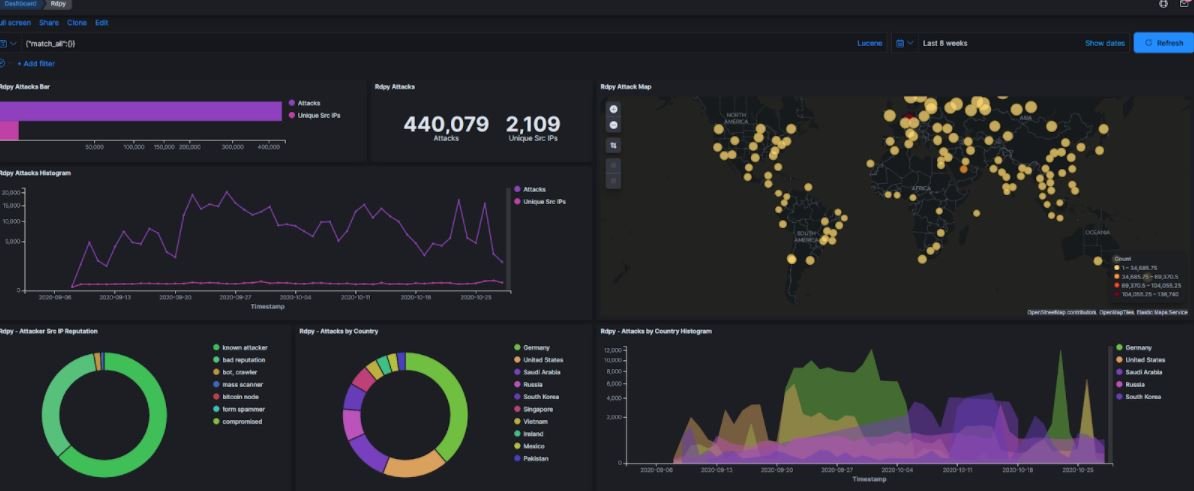
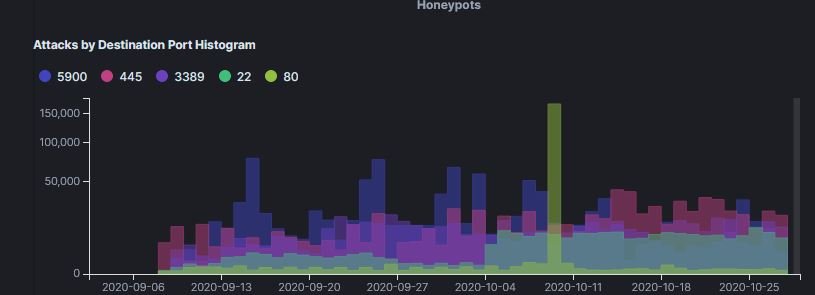
Port 3389 represents the RDP protocol, placing it among the 3 most attacked ports during the investigation. Ports 5900 (VNC) and 445 (SMB) are also popular attack vectors among the cybercriminal community, usually exploited for initial access to corporate networks.
The role of organizations in combating RDP attacks
There are many factors related to the increase of these attacks, although the main factor is the excessive way in which ransomware groups and other security threats have increased their presence. On the other hand, although installing security patches is one of the main methods for correcting these attacks, this practice has not become widespread in organizations, which continue to operate without security patches even for years.
An essential part of combating these attacks is up to organizations, so it’s worth remembering these simple tips that will help system administrators prevent these scenarios:
- Patch detected vulnerabilities
- Check if your machines have RDP ports exposed or not up-to-date
- Keep your networks and devices protected with a highly reliable firewall and antivirus solutions
Finding these available accesses in hacking forums is really common, so organizations need to start taking these risks seriously.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










