A report from security firm FireEye specialists details the detection of multiple ransomware distribution campaigns in which operators abuse the new KEGTAP, SINGLEMALT and WINEKEY bootloaders. In some of the reported cases, the infection chain was completed within 24 hours after the attack began.
The ransomware variants detected up to this point hold minimal similarities; however, experts discovered that they are all part of the same campaign after detecting that these variants interact with the same command and control server. These ransomware variants primarily target hospitals and health centers, a really worrying trend in the context of the pandemic.
For malware distribution, threat actors sent emails to employees of the targeted companies. These messages contained a link to a document in Google Docs, plus a link containing the payload of the ransomware in question.
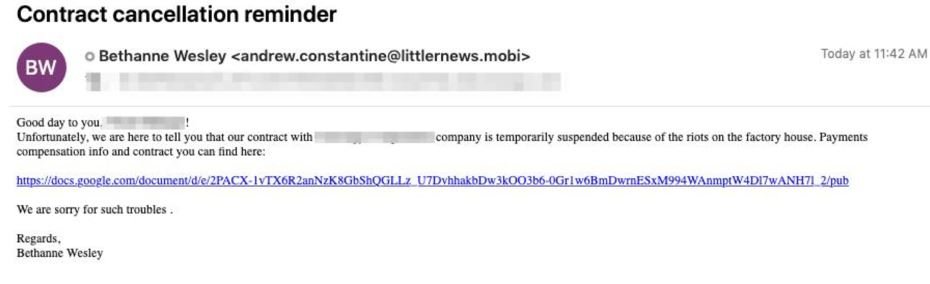
Clicking on the links would start downloading malware binaries with file names disguised as legitimate documents. After starting the bootloader and backdoor on the target system, the threat actors downloaded the POWETRICK and Cobalt Strike beacons, in addition to using other backdoor variants like ANCHOR for the use of the TrickBot ransomware.
In other attacks, malware binaries were hosted on a compromised infrastructure, but attackers soon switched to hosting their malware on legitimate web services, including Google Drive, Basecamp, Slack, Trello, Yougile and JetBrains.
In at least one case, cybercriminals maintained access to the victim’s environment using stolen credentials to access a VPN infrastructure without multi-factor authentication, allowing them to deploy a variety of malicious actions, such as running PowerShell commands via Cobalt Strike beacons.
Finally, experts also reported attacks related to KEGTAP, including Ryuk, Conti and Maze ransomware infections, all related to the ANCHOR backdoor.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











