The more popular a product, development or mobile app becomes, the more attractive it becomes for threat actors. This has been the case with Among Us, a growingly popular game that is facing increasing hacking issues, although a recent incident stands out among the rest of the attacks on the platform.
This is a highly specific attack that allows players to send spam messages about the channels of a user named Eris Loris on YouTube and Discord via in-game chat. In messages, Loris even threatens users to hack their devices if they do not subscribe to their channels; as if that weren’t the case, the messages conclude with a show of support for Donald Trump, president of the U.S.
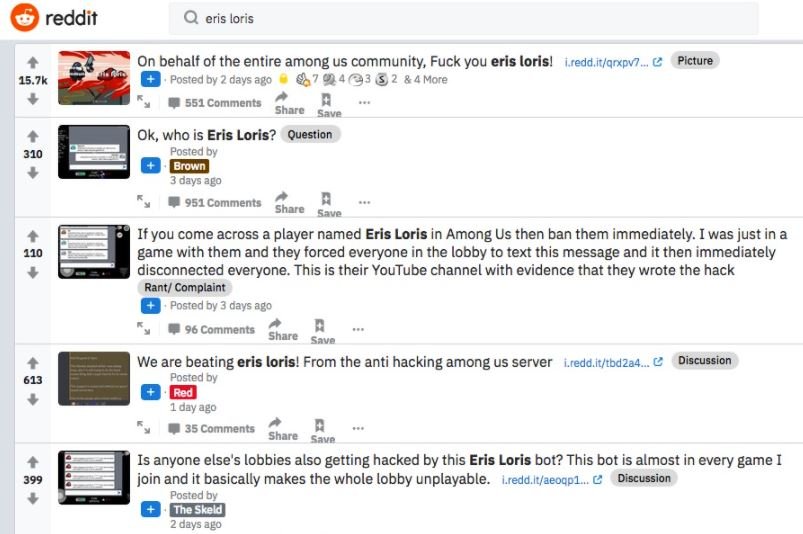
Using automated software (bots), the operator of this campaign has achieved a wide presence in Among Us, as thousands of users claim to have encountered these messages.
InnerSloth, the game’s developer mentions that they are aware of this hacking problem, so it would start an emergency update: “Please play in private games and only with people you trust,” the company asked its users. A few hours later Forest Willard, the company’s main programmer, posted an update on Twitter about the issue: “The update was not released earlier for fear of false positives, as it may sometimes seem that security in the game has been compromised even if everything is working normally.”
In this regard, the hacker mentions that his goal was only to off Among Us users: I was curious, I think its fun. I want to know if users care about this game as much as to let it go for finding some spam,” Loris said in an interview with a specialized website.
About the political message he has used, Loris recognizes himself as a Trump supporter, so he decided to use this message in his spam campaign. Specialists consider this to be a very common type of political message disclosure on video game platforms, this practice can only be curbed by users given its features.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











