The Nitro PDF service has been affected by a data breach incident, impacting its multiple business customers including firms such as Google, Apple, Microsoft, Citibank, among others. Nitro is one of the most important services for reading and editing documents in PDF format.
According to BleepingComputer, the incident was revealed on October 21, when the company sent a notice to the Australian Stock Exchange to report the incident, noting that customer data was not affected.
Although the firm contends that the incident did not cause further setbacks, there could still be details to be revealed. A report from cybersecurity company Cyble mentions that a threat actor is selling a 1TB database with confidential information allegedly extracted from Nitro. The hacker asks for $80, 000 in exchange for access to this information.
Experts mention that the ‘user_credential’ database table contains 70 million user records, including information such as full names, email addresses, hashed passwords, company name, IP addresses, and other information.
The document database contains the title of a file, in addition to some features about documents. According to the researchers, these databases contain a considerable number of records related to recognized companies, as shown below:
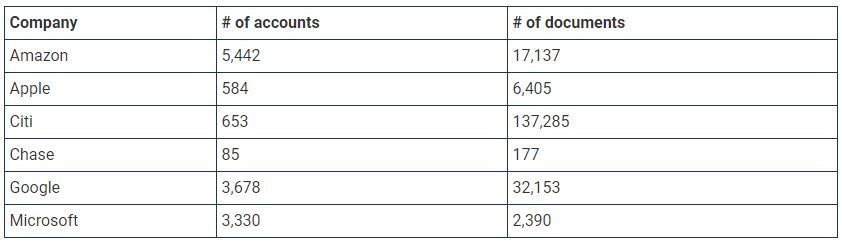
If the claims of threat actors are true, this could be one of the worst corporate data breaches seen in a long time. Because companies often use Nitro to digitally sign sensitive financial, legal, and marketing documents, it could allow the leak of information that would significantly affect a company’s business.
For those who are concerned that your Nitro account is part of this breach, Cyble has added the data to your AmIBreached.com. Users can send their email address and check if it was revealed in the stolen database using this service. The cybersecurity community tried to contact Nitro Software representatives with questions about the breach, but has not received an answer.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











