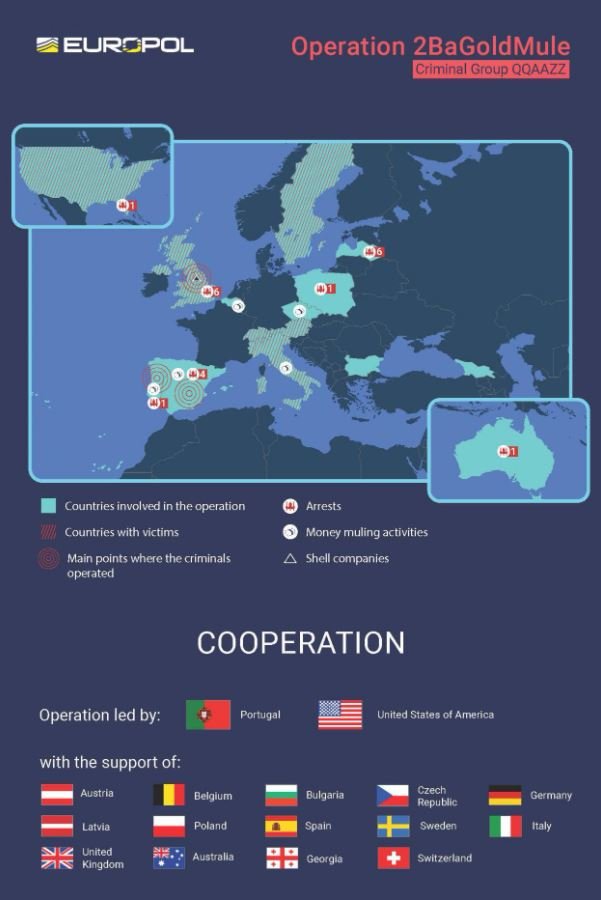
Thanks to an international operation involving the investigative agencies of 16 countries, in addition to Europol, 20 suspected individuals were arrested for their links to the QQAAZZ criminal network, responsible for washing tens of millions of Euros for the world’s largest criminal groups.
This operation consisted of the break-in of almost 40 locations in Bulgaria, Spain, Italy, Latvia and the United Kingdom, allowing legal proceedings to be initiated against those arrested in the United States, Portugal, the United Kingdom and Spain. Many of those arrested were in possession of computers for cryptocurrency mining.
According to accusations by U.S. prosecutors, the QQAAZZ network has been active since 2016, becoming one of the leading allies of multiple criminal groups.
Europol reports mention that the QQAAZZ network consists of individuals from Georgia, Romania, Belgium, among other countries, from where hundreds of bank accounts (individual and corporate) operated in financial institutions around the world in order to receive money from criminal groups. Subsequently these assets were transferred to other bank accounts controlled by the criminal network or converted into cryptocurrencies. Finally, after several bleaching processes, the assets were transferred back to the criminal groups.
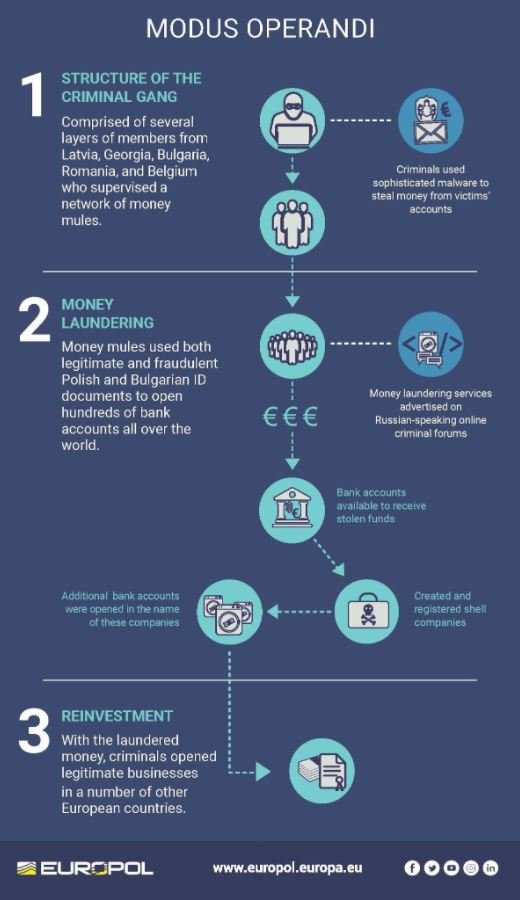
The criminals secured these bank accounts using fraudulent documentation from Poland and Bulgaria, creating dozens of fictitious companies that were only employed to hide their criminal activities.
According to the operators of the criminal network, QQAAZZ was a global service for bank transfers, mainly advertised in Russian hacking forums, where they found most of their clients. Europol mentions that this network provided its services to some of the world’s largest ransomware operator groups, ensuring the steady flow of revenue.
Europol’s European Cybercrime Centre (EC3) organized operational meetings, provided digital forensic support and facilitated the exchange of information between the various police agencies involved in this international operation, as well as assisting in the sending of specialized officers whose work was critical to the arrest of these individuals.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











