A report by security firm Comparitech mentions that Broadvoice, Voice over Internet Protocol (VoIP) service provider, leaked more than 350 million customer records related to the company’s “b-hive” cloud-based communications package.
The compromised information includes transcripts of voice messages, which potentially include confidential information from the company’s customers, including details about prescriptions and loans for substantial sums.
This platform supports the basic interactions of customers such as patients, customers, partners, suppliers and others, so a large amount of personal data circulates through these networks. In addition, the data is retained by the company in case its customers require it.
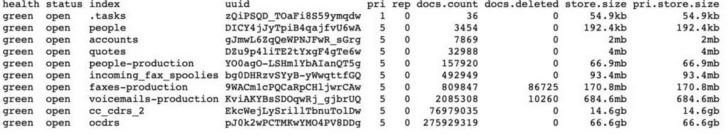
Apparently the incident is because the company left an Elasticsearch cluster exposed on the public Internet, so any user could have accessed this data without requiring authentication. This cache also included personal details of Broadvoice customers, deployed in 10 separate data collections.
The largest collection (with 275 million records) included the full name of the calling user, their ID, phone number, as well as the city and state. Another large collection titled “people-production” contained account identification numbers for the company’s own customers, allowing researchers to cross-reference records from other collections.
Finally, experts found 2 million voice mail records, with more than 200,000 transcripts. Experts also found some voice messages that included details about mortgages and other loans, including policy numbers.
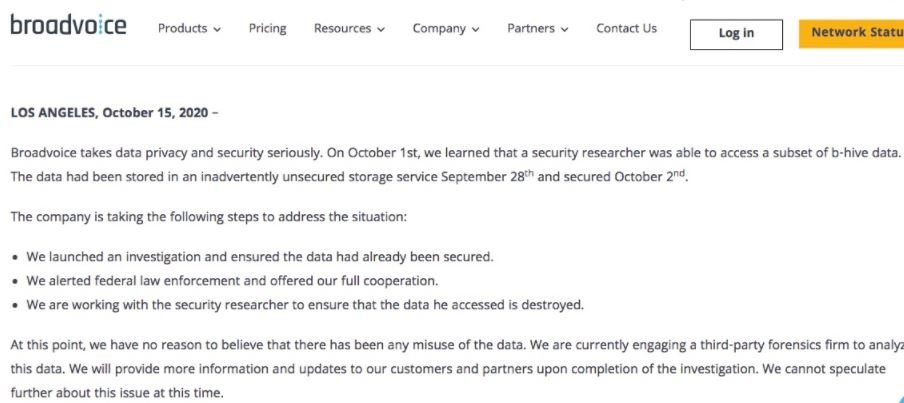
Rebecca Rosen, vice president of marekting at Broadvoice, said: “There are just fewer than 10,000 small and medium-sized companies affected during this incident; we believe that the researchers who reported the leak accessed a subset of data with a limited amount of information. Our research is still ongoing, so more details will be shared shortly.”
The information exposed could be useful for threat actors specializing in phishing, identity fraud, and other malicious activities, so it’s important for the company to clarify this incident as soon as possible, as well as take appropriate steps to protect its users.

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.











